2025西湖论剑初赛唯一RE题WriteUp
0. 概述
本次西湖论剑revere分区只有一道题目,并且没有附件,只给了个纯靶机。。。
。。。。
思路:对于无附件的题目,我们采取通过回显来判断出题人意图,从而得解的方式。
1. 测试
题目无附件,只给了个靶机
名字叫bitdance
连接靶机,发现只有个长度回显,所以我们首先测试长度,看长度正确回显
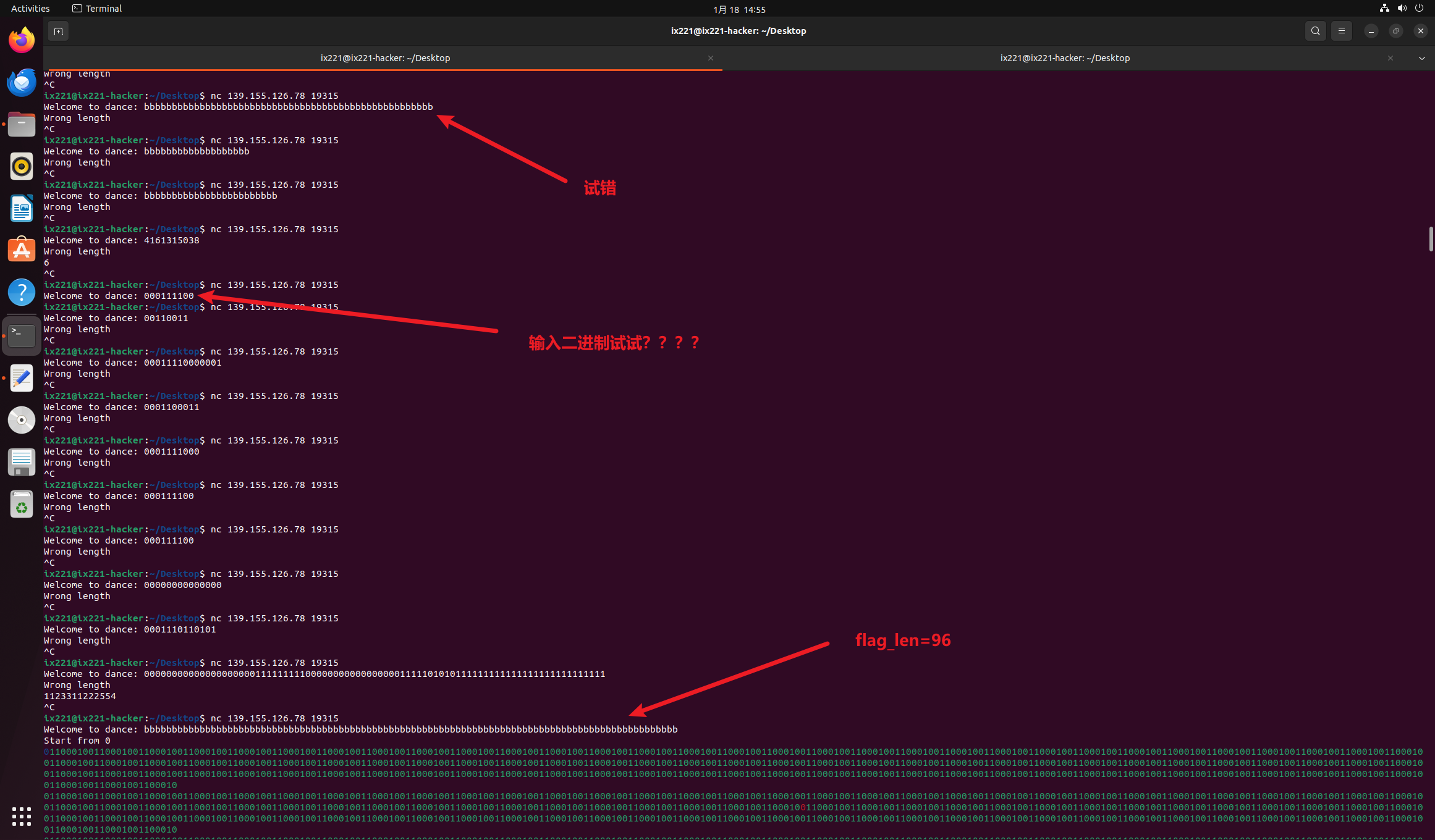
测试得知,flag_len = 96
2. 求解
回显比较长,我们把回显报存到文件中
1 | HOST = '139.155.126.78' # 这里请替换为目标主机的真实地址 |
然后看回显文本,这些数据的行数正好是768,并且发现有一些数据是红色的,
也就是是96*8=768
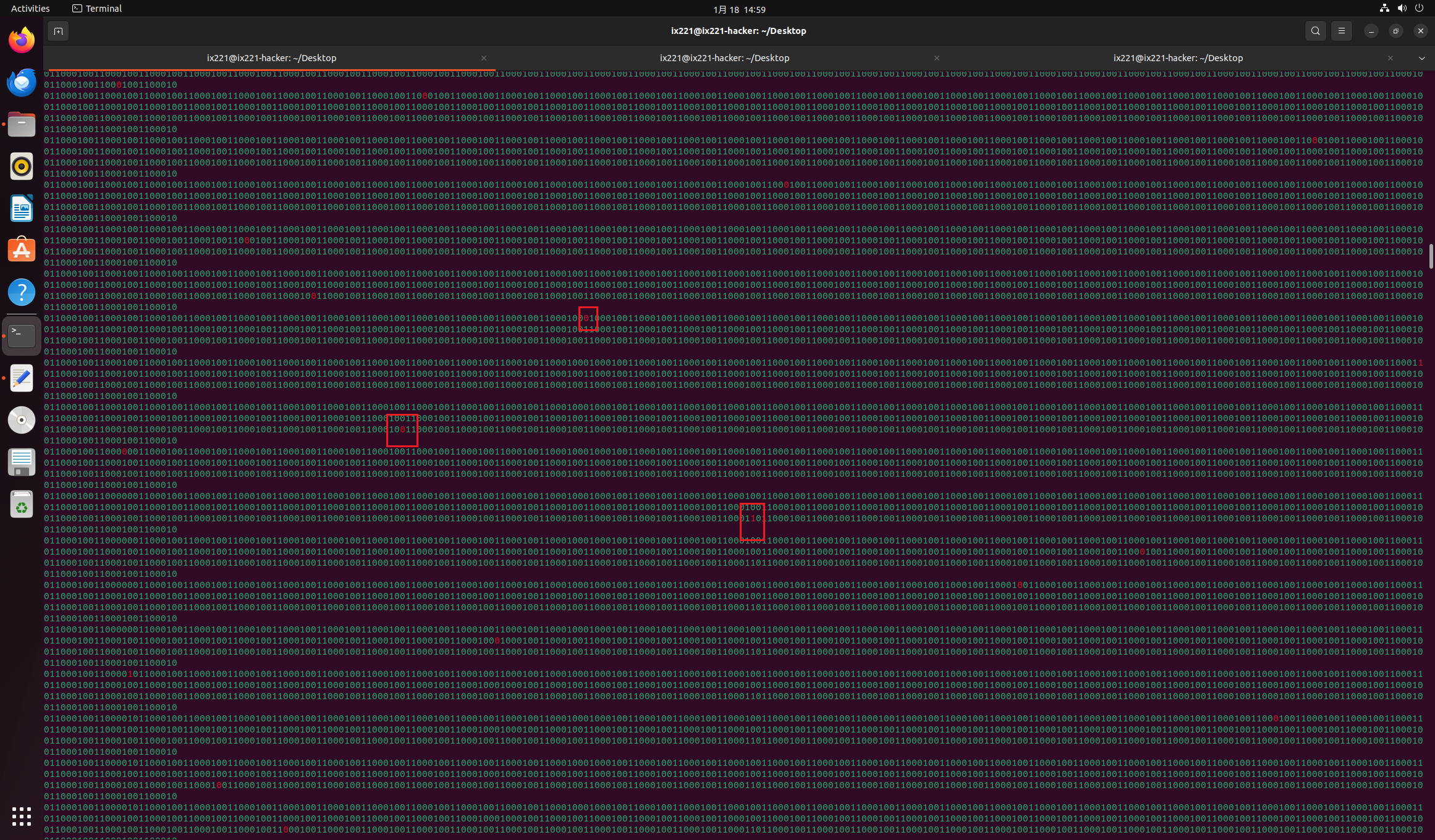
密文如下,总共有768个二进制位。
1 | Checking with 000011000110000101001000001110100000000101000100110100101000110111001010000010111011100000000010101100011100010110001000011001000110011101101001001001100110100100010001110001110100011100011111110111001011011100001110000110100101000011000011010101110000110101110101101011110000000101011000000101001010001000001010111111111100100010001100000001011101100101000000111101101010001100010110001000010101101100111101111111110101100111000010111110110101010010000011100000011011010010001110011010100101000000011100000010001010010110111000111001000100110101000001101000110001001000000000111100001100100000001010100101101010101001111001010010001111000101011011001001001101000010011101011101011011011110101000110110101000011001000100001101110000101110110000010001000010010001001100 |
通过红色字符判断,每次都会对一行数据进行操作,所以我们将红色字符的位置爆破出来。
猜测是对密文进行类似字符映射的机制,从而求解。
1 | from pwn import * |
跑出结果
1 | [4, [295]] |
然后映射字符
1 | dict_map ={ |
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 摘星阁!
