前言 这周末,四级英语考试,强网杯,楚慧杯,还通宵打强网,我滴妈,差点猝si =。=
然后这篇写的楚慧杯的,就重点说(吐槽)一下
vocal,就3个小时的比赛,还得比赛结束前交WP,写了re1,misc1,misc2,0.o真的极限=。=
楚慧杯学生组
还好,收获满满,强网先锋应该够了,楚慧杯也晋级了,四级的话,阿巴阿巴 =。=
rev babyre - ollvm/tea?xtea 打完强网库库打ollvm,这玩意又来
好好,周末就ollvm大赛
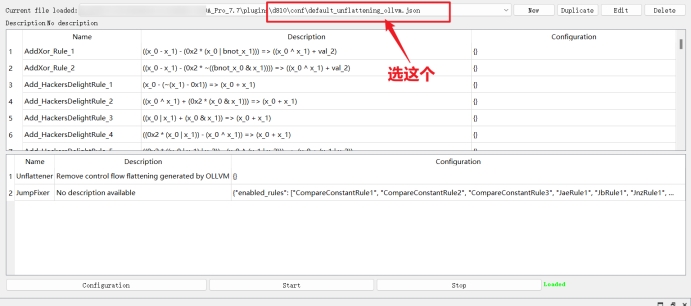
D810去混淆
D810是插件 搜到直接用 前提:angr要装好
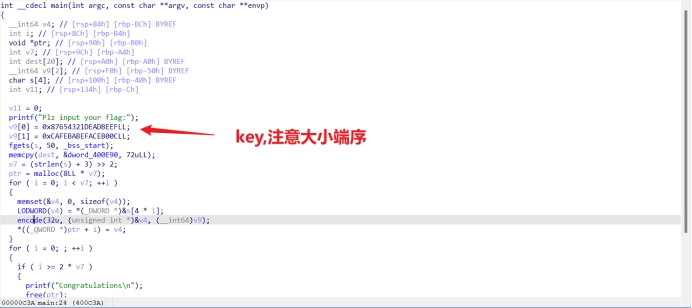
main函数
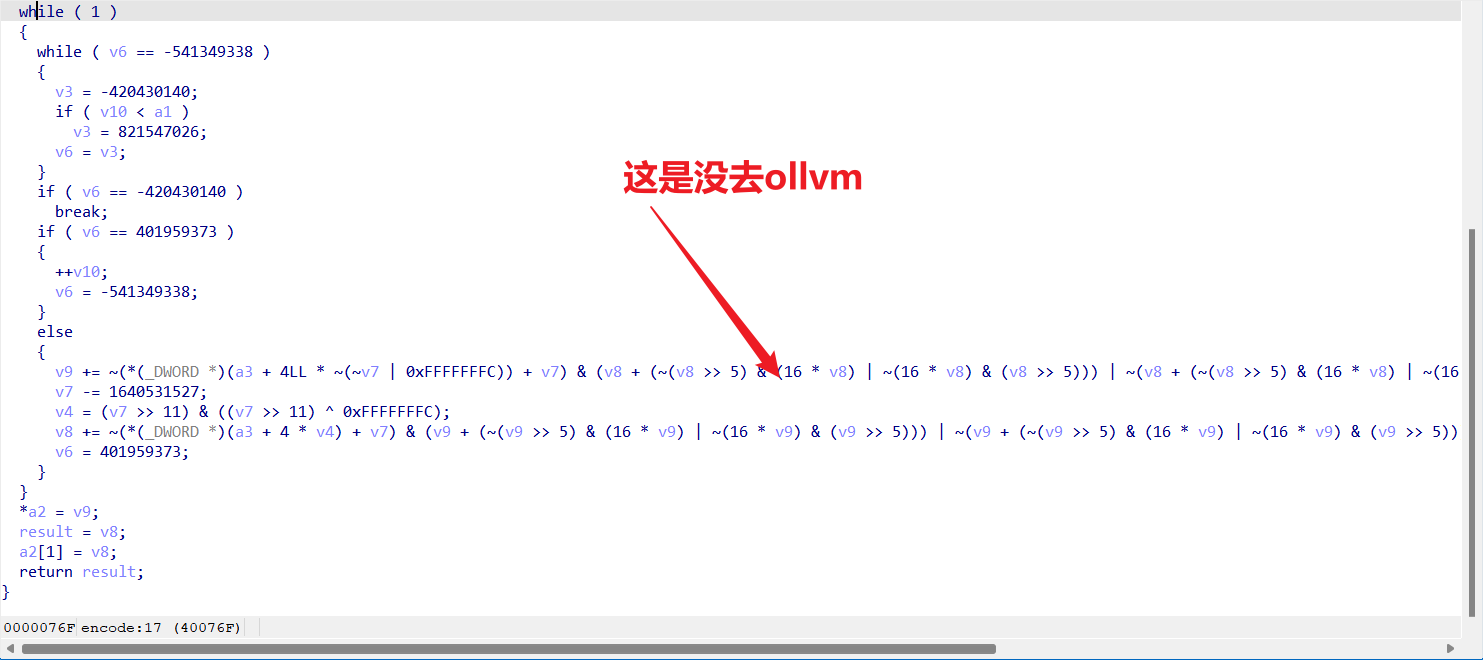
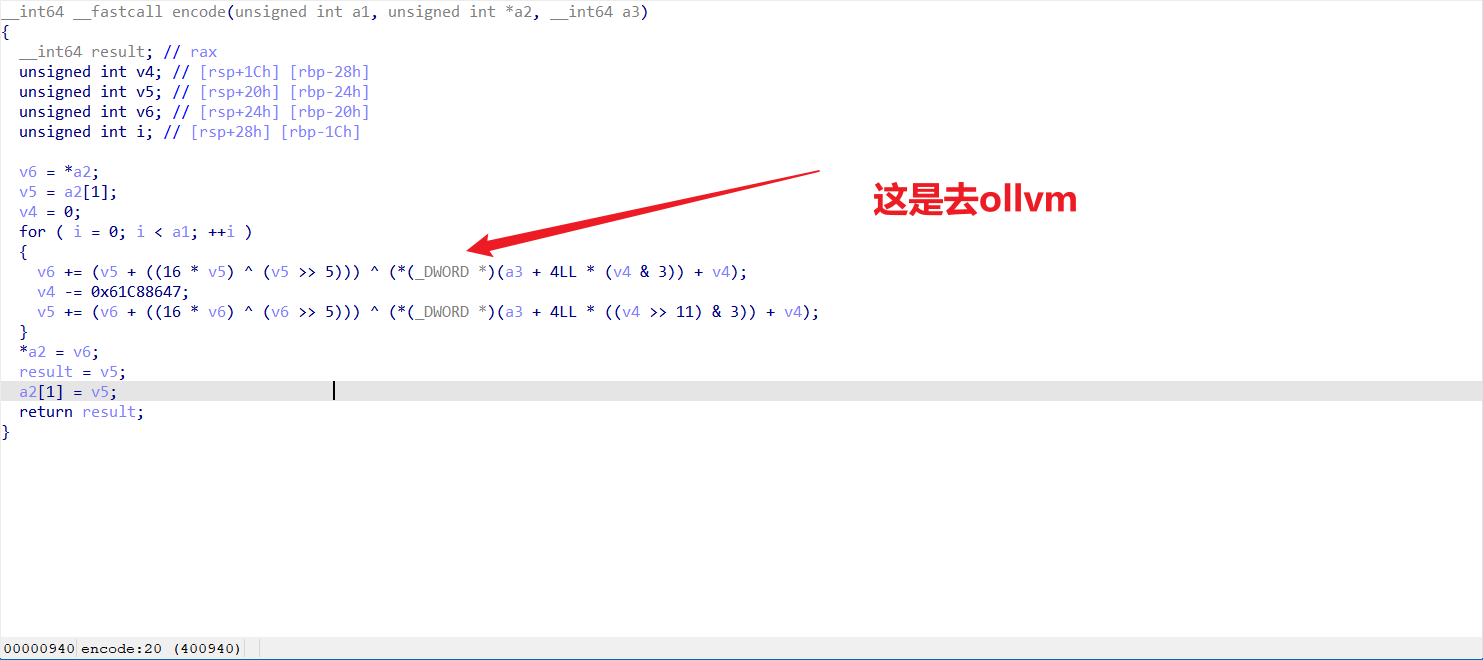
Encode 离谱,我去玩ollvm脚本没跑出来
然后我没去ollvm改了一下跑出来了,vocal
这个是去ollvm
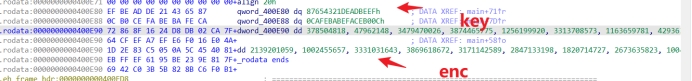
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 #include <stdio.h> #include <stdint.h> typedef unsigned long _DWORD;void decrypt (uint32_t * v, uint32_t * k) { uint32_t v0 = v[0 ], v1 = v[1 ], i; uint32_t delta = 0x61C88647 ; uint32_t sum = -0xc3910c8e0 ; uint32_t k0 = k[0 ], k1 = k[1 ], k2 = k[2 ], k3 = k[3 ]; for (i = 0 ; i < 32 ; i++) { v1 -= ((v0 << 4 ) + k1) ^ (v0 + sum) ^ ((v0 >> 5 ) + k0); sum += delta; v0 -= ((v1 << 4 ) + k3) ^ (v1 + sum) ^ ((v1 >> 5 ) + k2); } v[0 ] = v0; v[1 ] = v1; } void encodec (unsigned int * a2, __int64 k) { __int64 result; __int64 v4; unsigned int sum; unsigned int v1; unsigned int v0; unsigned int i; v0 = *a2; v1 = a2[1 ]; sum = -0xc3910c8e0 ; for (i = 0 ; i < 32 ; ++i) { v4 = (sum >> 11 ) & ((sum >> 11 ) ^ 0xFFFFFFFC ); v1 -= ~(*(_DWORD*)(k + 4 * v4) + sum) & (v0 + (~(v0 >> 5 ) & (16 * v0) | ~(16 * v0) & (v0 >> 5 ))) | ~(v0 + (~(v0 >> 5 ) & (16 * v0) | ~(16 * v0) & (v0 >> 5 ))) & (*(_DWORD*)(k + 4 * v4) + sum); sum += 0x61C88647 ; v0 -= ~(*(_DWORD*)(k + 4LL * ~(~sum | 0xFFFFFFFC )) + sum) & (v1 + (~(v1 >> 5 ) & (16 * v1) | ~(16 * v1) & (v1 >> 5 ))) | ~(v1 + (~(v1 >> 5 ) & (16 * v1) | ~(16 * v1) & (v1 >> 5 ))) & (*(_DWORD*)(k + 4LL * ~(~sum | 0xFFFFFFFC )) + sum); } *a2 = v0; result = v1; a2[1 ] = v1; } int main () { uint32_t cipher[] = { 0x168F8672 , 0x02DBD824 , 0xCF647FCA , 0xE6EFA7EF , 0x4AE016F0 , 0xC5832E1D , 0x455C0A05 , 0xFFEB8140 , 0xBE9561EF , 0x7F819E23 , 0x3BC04269 , 0xC68B825B , 0xE6A5B1F0 , 0xBD03CBBD , 0xA9B3CE0E , 0x6C85E6E7 , 0x9F5C71EF , 0x3BE4BD57 }; uint32_t key[4 ] = { 0xDEADBEEF , 0x87654321 , 0xFACEB00C , 0xCAFEBABE }; for (int i = 0 ; i < 18 ; i += 2 ) { uint32_t temp[2 ]; temp[0 ] = cipher[i]; temp[1 ] = cipher[i + 1 ]; encodec(temp, (__int64)key); printf ("%c%c%c%c%c%c%c%c" , *((char *)&temp[0 ] + 0 ), *((char *)&temp[0 ] + 1 ), *((char *)&temp[0 ] + 2 ), *((char *)&temp[0 ] + 3 ), *((char *)&temp[1 ] + 0 ), *((char *)&temp[1 ] + 1 ), *((char *)&temp[1 ] + 2 ), *((char *)&temp[1 ] + 3 )); } return 0 ; }
DASCTF{Don’t_forget_to_drink_tea}
后边俩题没出来,3个小时的比赛,还得比赛前交WP,hhhhhhh
做出3道题已经是我的极限了
misc ez_zip 看到循环嵌套解压缩包,简单了
差点前3血,还是慢了(不愧是DAS的题,我本来还想投这种题目呢)
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 import os import zipfile import tarfile import py7zr import sys sys.setrecursionlimit(100000) input_archive_file = "4096.zip" output_folder = "extracted_files" os.makedirs(output_folder, exist_ok=True) def extract_zip(input_zip_file, output_folder): with zipfile.ZipFile(input_zip_file, "r") as zip_ref: zip_ref.extractall(output_folder) def extract_tar_gz(input_tar_gz_file, output_folder): with tarfile.open(input_tar_gz_file, "r:gz") as tar_ref: tar_ref.extractall(output_folder) def extract_7z(input_7z_file, output_folder): with py7zr.SevenZipFile(input_7z_file, mode='r') as zr: zr.extractall(output_folder) def extract_and_delete_archive(input_file, output_folder): file_extension = os.path.splitext(input_file)[1] print(file_extension) if file_extension == ".zip": extract_function = extract_zip elif file_extension == ".gz": extract_function = extract_tar_gz elif file_extension == ".7z": extract_function = extract_7z else: raise ValueError("Unsupported file format") extract_function(input_file, output_folder) os.remove(input_file) def extract_all_nested_archives(input_file, output_folder): stack = [(input_file, output_folder)] while stack: current_input_file, current_output_folder = stack.pop() extract_and_delete_archive(current_input_file, current_output_folder) extracted_files = os.listdir(current_output_folder) for extracted_file in extracted_files: extracted_file_path = os.path.join(current_output_folder, extracted_file) if os.path.isfile(extracted_file_path): stack.append((extracted_file_path, current_output_folder)) extract_all_nested_archives(input_archive_file, output_folder)
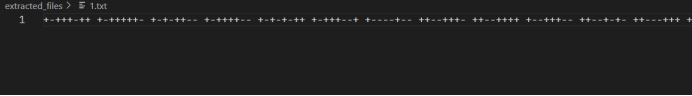
解出
+-+++-++ +-+++++- +-+-++– +-++++– +-+-+-++ +-+++–+ +—-+– ++–+++- ++–++++ +–+++– ++–+-+- ++—+++ ++–++-+ ++–+-+- ++—+++ +–+++– +–+++– +–++–+ ++–+++- +–++-+- ++–+— +–+++– ++–+–+ ++–++– ++–+++- +–++-+- ++–+-+- ++—++- ++–+++- ++–+++- +–++-+- +–++-++ ++–+–+ +–++++- +–+++– +–+++– ++–+-++ +–++-+- +–++-++ +—–+-
+ –>. 摩斯解密
.-…-../.-…..-/.-.-..–/.-….–/.-.-.-../.-…–./.—-.–/..–…-/..–…./.–…–/..–.-.-/..—…/..–..-./..–.-.-/..—…/.–…–/.–…–/.–..–./..–…-/.–..-.-/..–.—/.–…–/..–.–./..–..–/..–…-/.–..-.-/..–.-.-/..—..-/..–…-/..–…-/.–..-.-/.–..-../..–.–./.–….-/.–…–/.–…–/..–.-../.–..-.-/.–..-../.—–.-
得到
%u44%u41%u53%u43%u54%u46%u7b%u31%u30%u63%u35%u38%u32%u35%u38%u63%u63%u66%u31%u65%u37%u63%u36%u33%u31%u65%u35%u39%u31%u31%u65%u64%u36%u61%u63%u63%u34%u65%u64%u7d
转16进制
DASCTF{10c58258ccf1e7c631e5911ed6acc4ed}
easy取证 - snow隐写 snow隐写,vocal
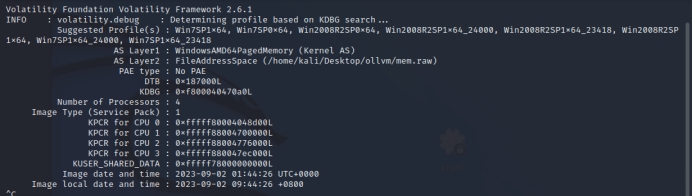
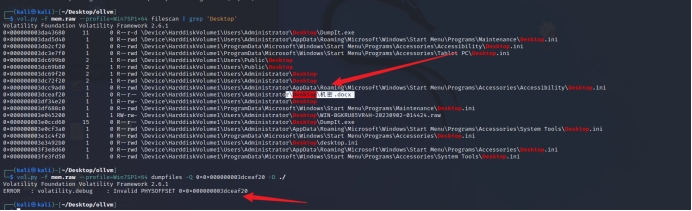
vol.py -f mem.raw –profile=Win7SP1x64 filescan | grep ‘Desktop’
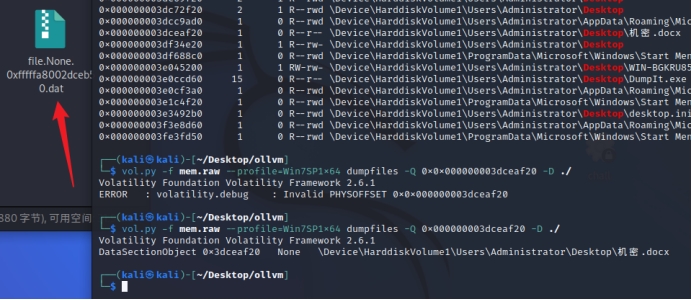
vol.py -f mem.raw –profile=Win7SP1x64 dumpfiles -Q 0x000000003dceaf20 -D ./
桌面有个docx,dump下来
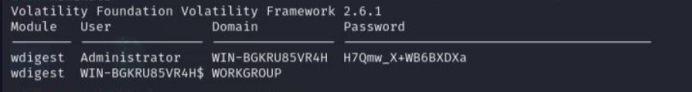
打开docx,snow隐写,密码使用mimikatz提取
密码: H7Qmw_X+WB6BXDXa
DASCTF{f891eff370a2cbefec49d2a577b552d3}
└─$ vol.py -f –plugins=/kali/Desktop/tools/volatility/volatility/plugins/ -f mem.raw –profile=Win7SP1x64 mimikatz
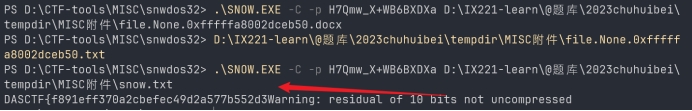
.\SNOW.EXE -C -p H7Qmw_X+WB6BXDXa snow.txt
获得flag
DASCTF{f891eff370a2cbefec49d2a577b552d3}