2023强网杯WriteUp
前言
2023-12-18创建的文件夹,搁到现在才上传,忘了,麻麻了
rev === 强ollvm杯
babyre
Tls附加dbg
过掉
把程序运行,在这儿附加
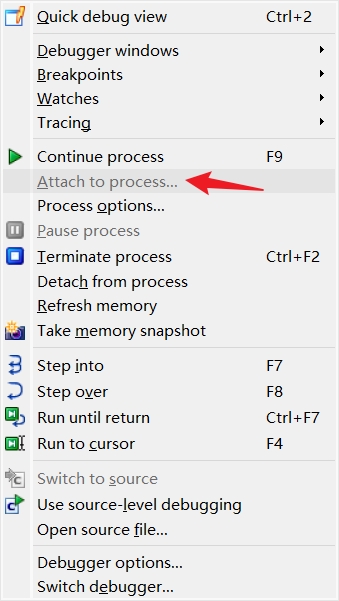
静态密文,key都是假的
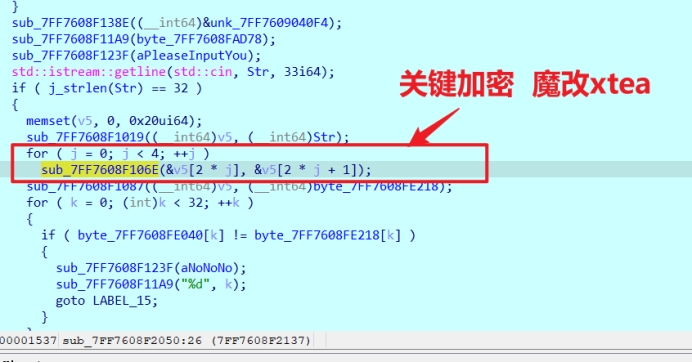
动调起来得到真的
密文
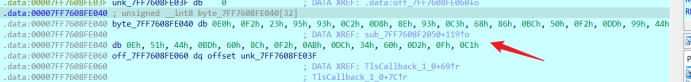
Key
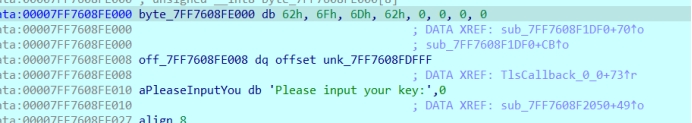
这是delta
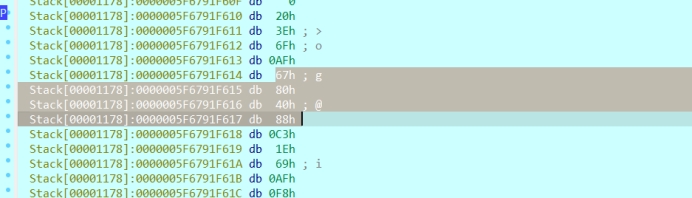
调到跳出循环,得到sum
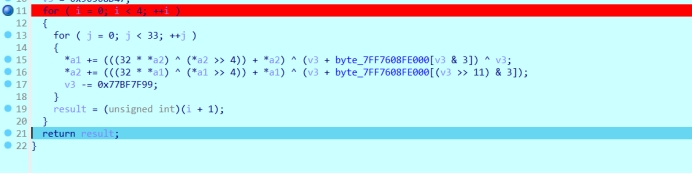
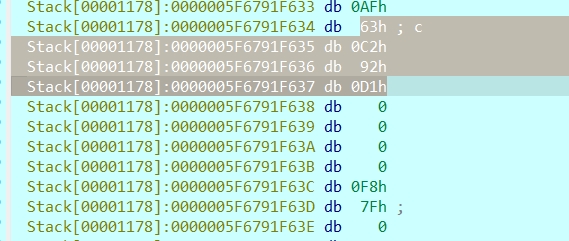
Exp
1 |
|
flag{W31com3_2_Th3_QwbS7_4nd_H4v3_Fun}
ezre
ida打开D810去ollvm混淆,start!
D810是插件 搜到直接用 前提:angr要装好
main函数无有用信息
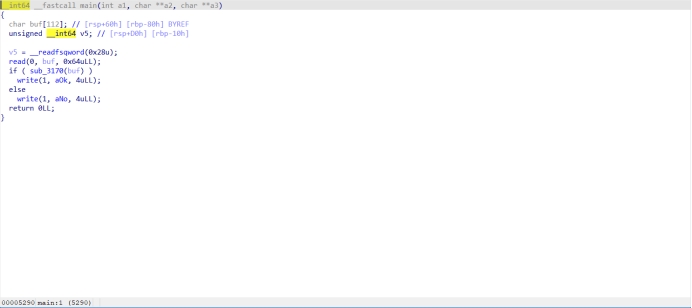
SM4加密
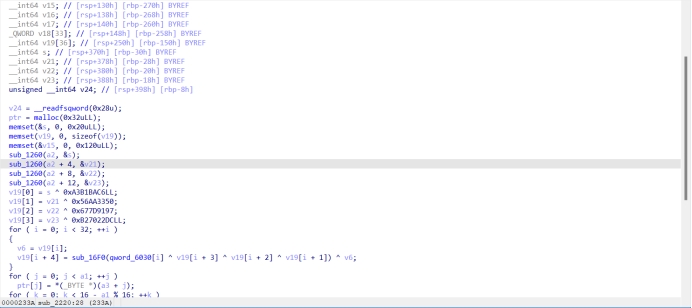
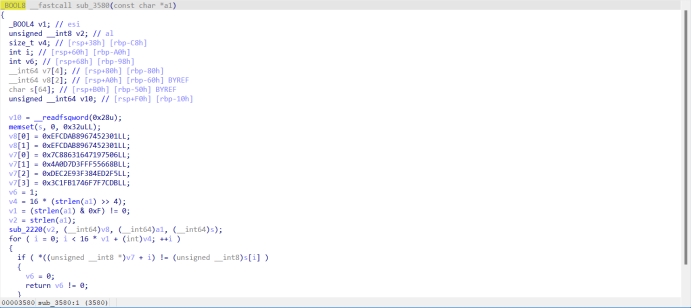
也可以搜固定的数组
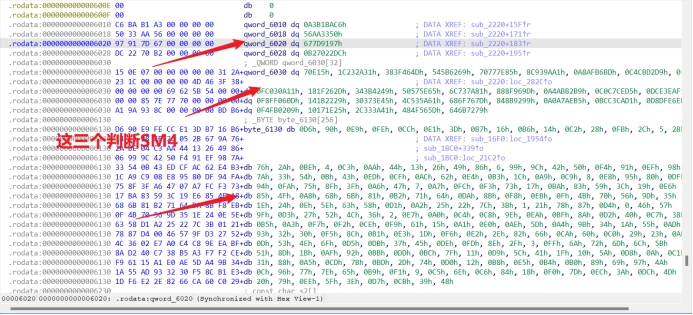
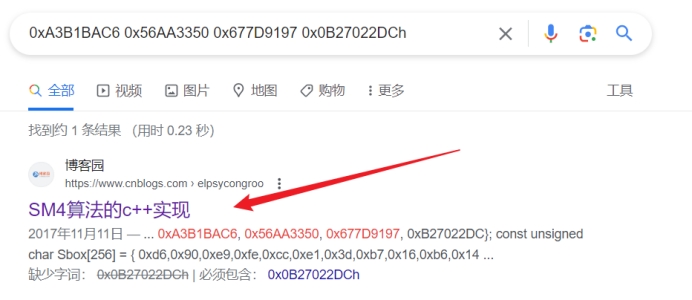
密文和密钥在这
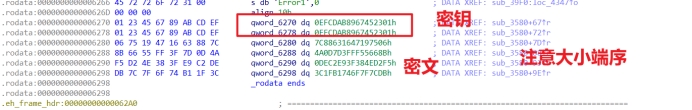
Key :
0123456789ABCDEF0123456789ABCDEF
Cipher:
067519471663887C8B6655FF3F7D0D4AF5D24E383FE9C2DEDB7C7F6F74B11F3C
Flag:
flag{h3kk0_w0rld_sur3_3n0ugh}
cyberchef解
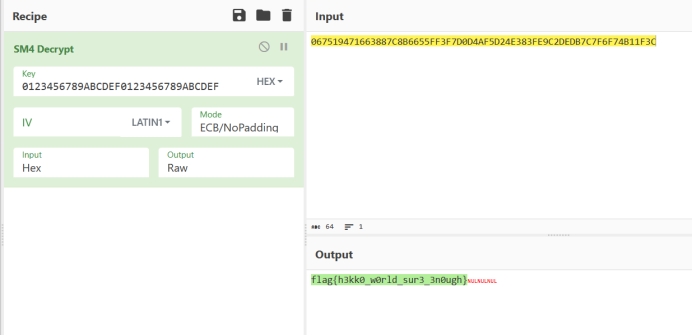
也可以脚本,贴一个自己去研究
1 |
|
ezre-强网先锋
打开题目发现是ollvm平坦化混淆。
可以使用插件D810去控制流平坦化
使用前提:angr要装好
也可以使用OLLVM去除 https://github.com/cq674350529/deflat 中的混淆。
可以使用以下Python命令进行操作:python deflat.py -f ezre –addr 0xxxxxxxx。
去完混淆分析代码,发现就是经过5次bas加解密,问题在于密文
交叉引用,有个反调试
审计发现,如果赋值为1,则修改密文
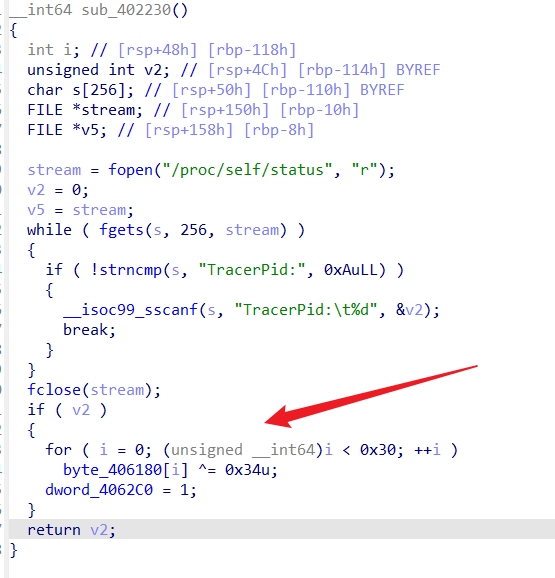
那么我们可以动调,在main函数把base的table取出
通过异或得到密文
然后复现加密流程,经过5次加解密得到flag
这个是main函数中调用的Base加密函数
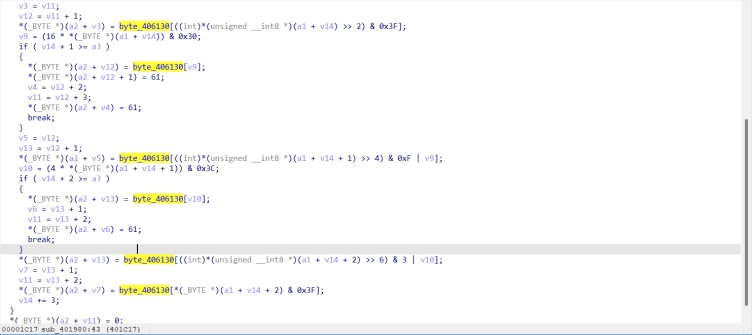
这个是动调出来的base的table
From base64
plxXOZtaiUneJIhk7qSYEjD1Km94o0FTu52VQgNL3vCBH8zsA/b+dycGPRMwWfr6
To base64
pnHQwlAveo4DhGg1jE3SsIqJ2mrzxCiNb+Mf0YVd5L8c97/WkOTtuKFZyRBUPX6a
From base64
Hc0xwuZmy3DpQnSgj2LhUtrlVvNYks+BX/MOoETaKqR4eb9WF8ICGzf6id1P75JA
To base64
FGseVD3ibtHWR1czhLnUfJK6SEZ2OyPAIpQoqgY0w49u+7rad5CxljMXvNTBkm/8
From base64
l+USN4J5Rfj0TaVOcnzXiPGZIBpoAExuQtHyKD692hwmqe7/Mgk8v1sdCW3bYFLr
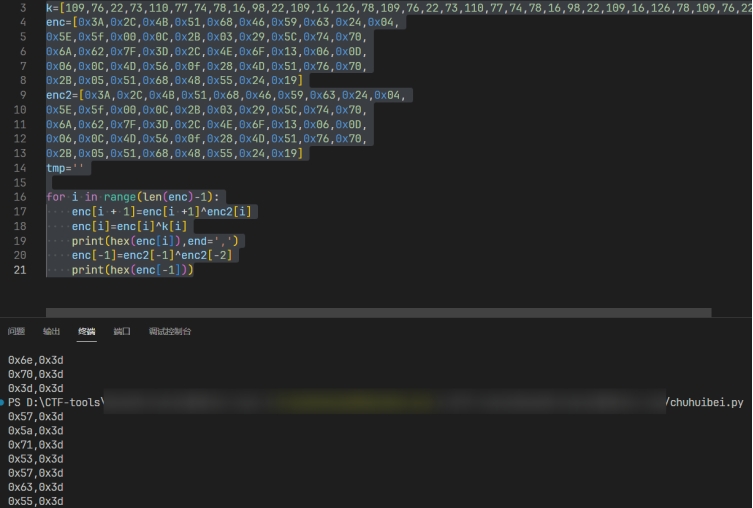
这是反解密文的脚本
1 | k=[109,76,22,73,110,77,74,78,16,98,22,109,16,126,78,109,76,22,73,110,77,74,78,16,98,22,109,16,126,78,109,76,22,73,110,77,74,78,16,98,22,109,16,126,78,109,76,0] |
得出密文
0x57,0x3d
0x5a,0x3d
0x71,0x3d
0x53,0x3d
0x57,0x3d
0x63,0x3d
0x55,0x3d
0x74,0x3d
0x57,0x3d
0x42,0x3d
0x4c,0x3d
0x6c,0x3d
0x4f,0x3d
0x72,0x3d
0x69,0x3d
0x45,0x3d
0x66,0x3d
0x63,0x3d
0x61,0x3d
0x6a,0x3d
0x57,0x3d
0x42,0x3d
0x53,0x3d
0x52,0x3d
0x73,0x3d
0x74,0x3d
0x4c,0x3d
0x6c,0x3d
0x6b,0x3d
0x45,0x3d
0x66,0x3d
0x46,0x3d
0x57,0x3d
0x52,0x3d
0x37,0x3d
0x6a,0x3d
0x2f,0x3d
0x52,0x3d
0x37,0x3d
0x64,0x3d
0x4d,0x3d
0x43,0x3d
0x44,0x3d
0x47,0x3d
0x6e,0x3d
0x70,0x3d
0x3d,0x3d
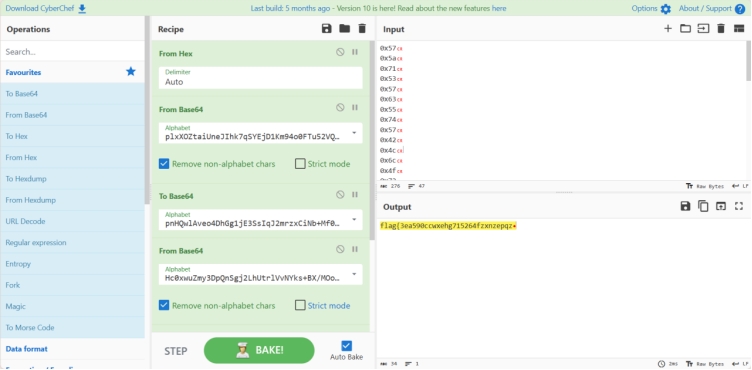
flag{3ea590ccwxehg715264fzxnzepqz}
dotdot
还是可以学到东西的
因为前期尝试手动解密,对加密的流程有了很深刻理解(
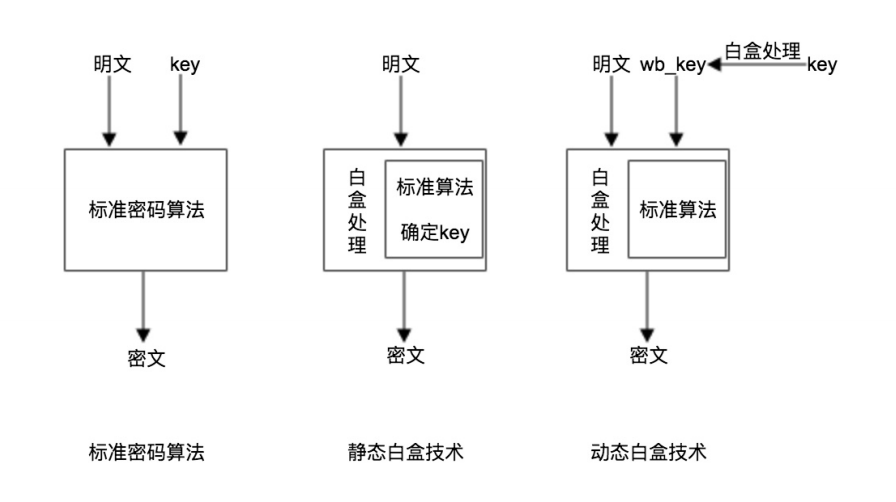
白盒技术
白盒密码技术是一项能够抵抗白盒攻击的密码技术。
白盒攻击是指攻击者对设备终端拥有完全的控制能力,能够观测和更改程序运行时的内部数据。
这种攻击环境称为白盒攻击环境。大多智能终端环境(Android、iOS等)在很多情况下就是一个白
盒攻击环境。
大概就是这样
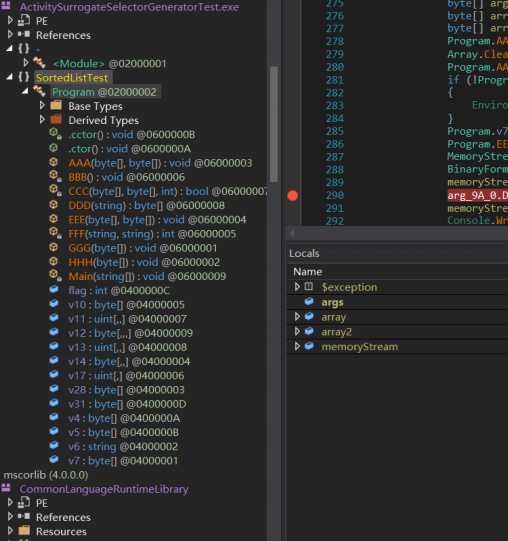
主要还是 AAA -> AES白盒加密
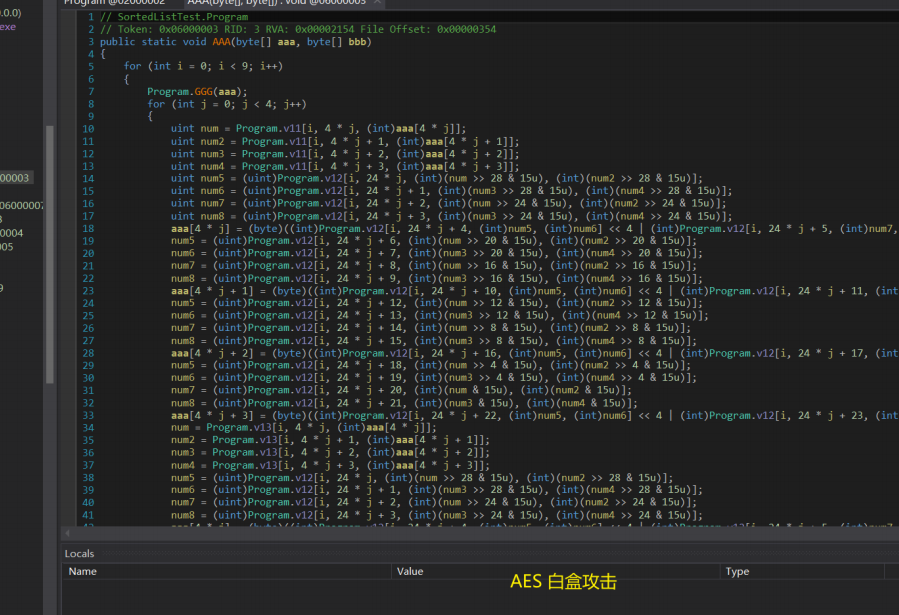
前期铺垫
将复杂的加密修改成简单的步骤
当没有chang_index函数时,加密就变成了4字节为单位进行加密了。
下面是我将题目给的代码,进行了修改,然后整理如下:
1 | from data import * |
改成这样,就变成了4字节爆破。
发现改变1个字节(4个字节单位)发生变化
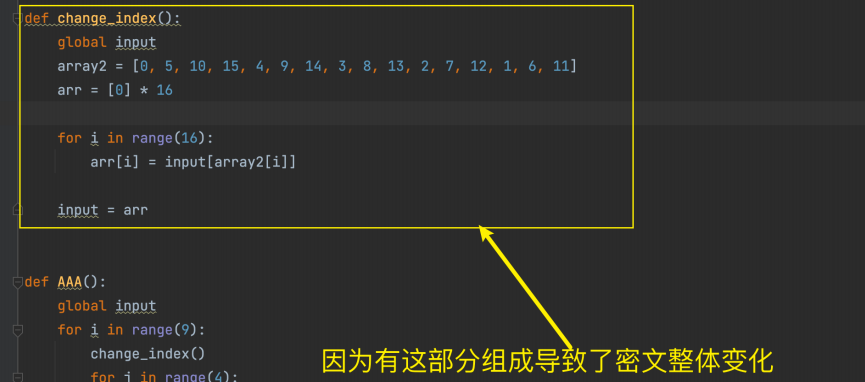
1 | def change_index(): |
