2023河南省金盾杯WriteUp
前言
题目质量不错
打穿逆向区跟杂项区(bushi)
累死了,我靠,比赛刚结束就得赶高铁去青岛,在高铁上写Wp,我的天,要晕过去的节奏
嗨嗨嗨 Orz
Rev
RE1 - tls/小花指令/RC4
主要是RC4加密有个tls,不用管
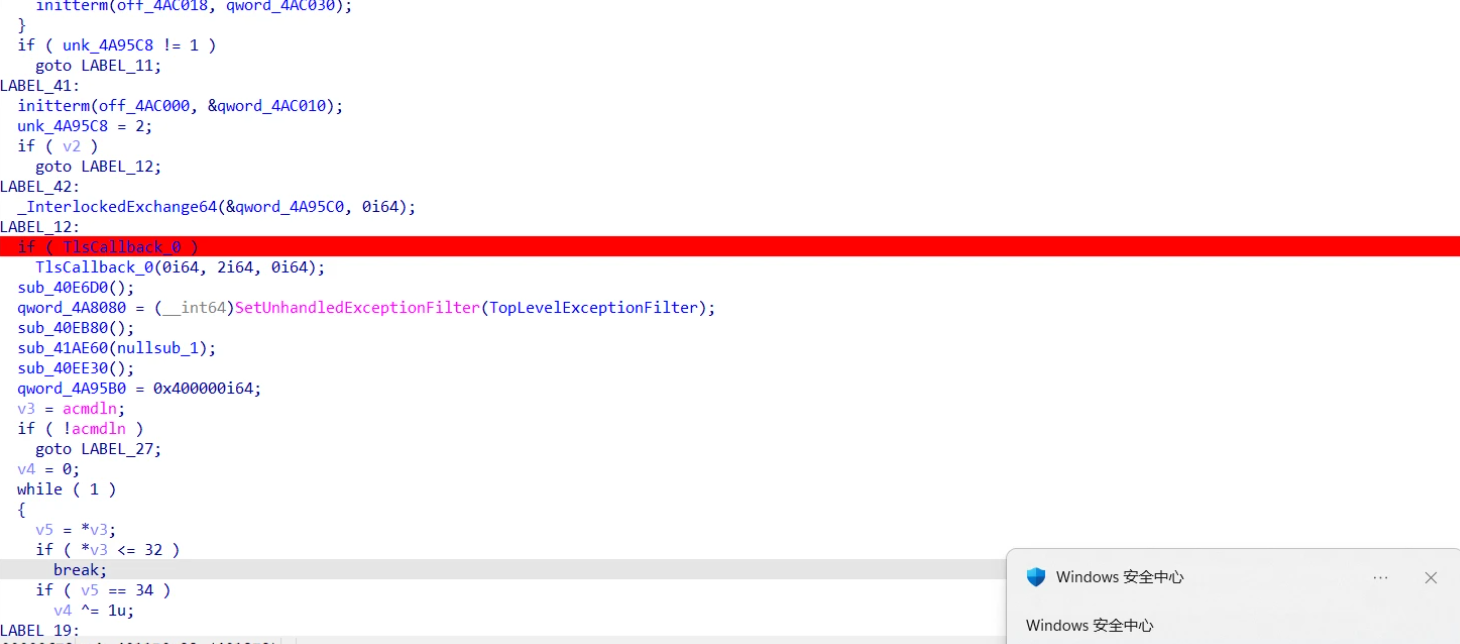
主要RC4的call在这儿
这儿应该算是花指令的一种吧
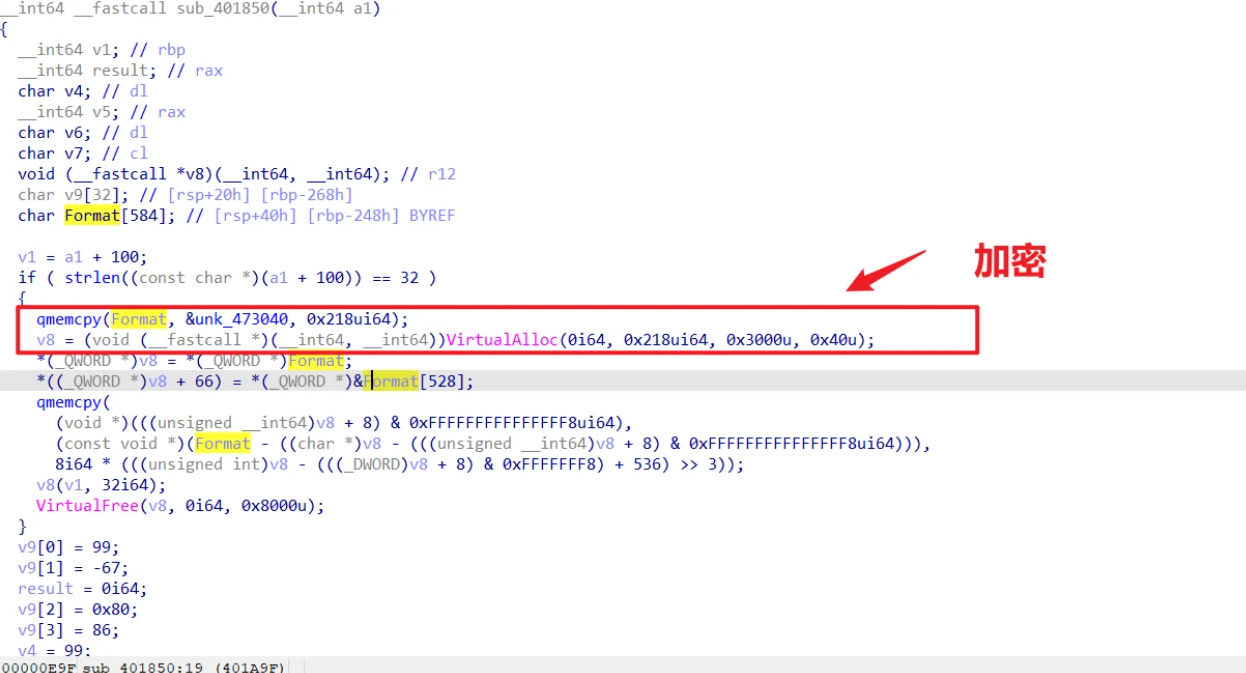
unk_473040是RC4函数的地址
c一下即可
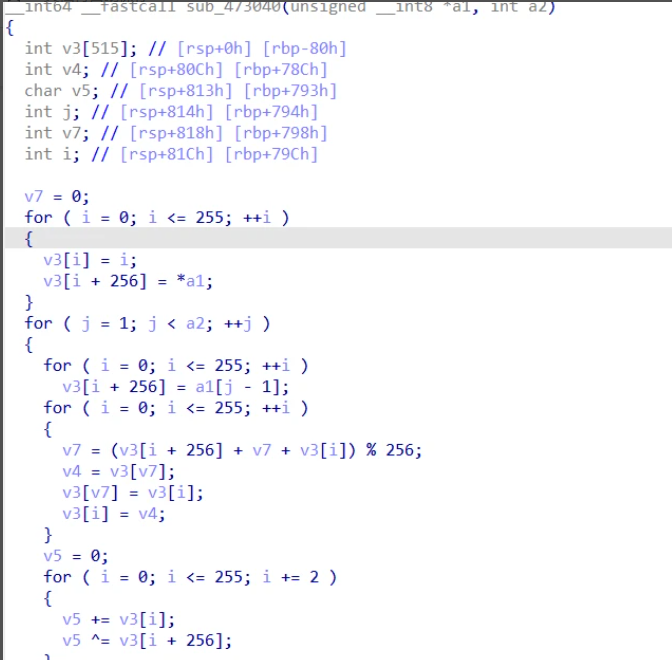
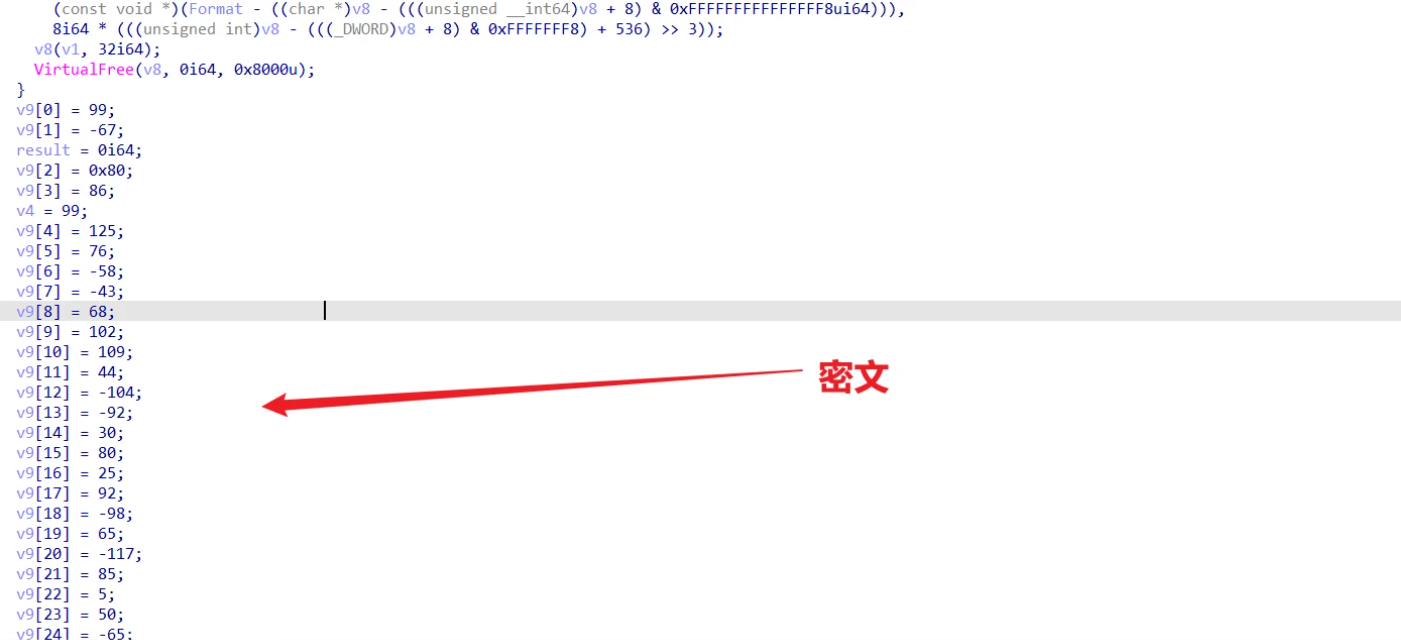
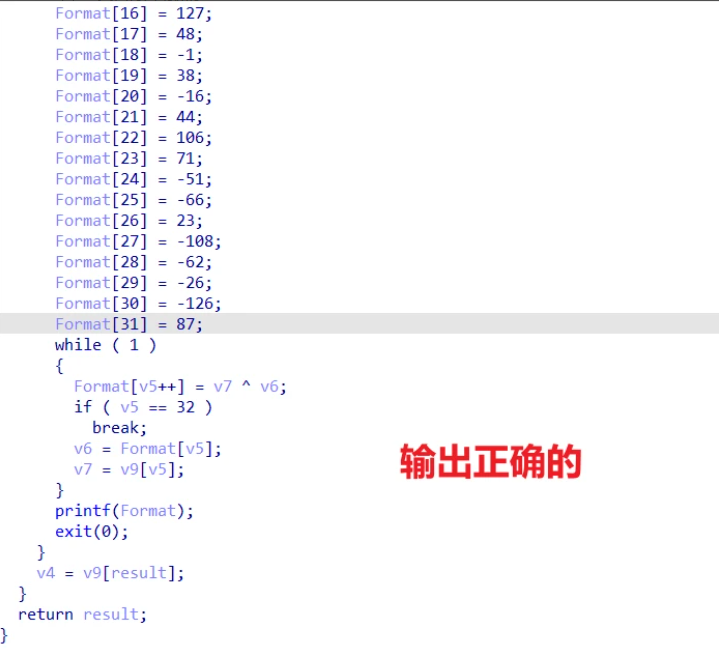
1 |
|
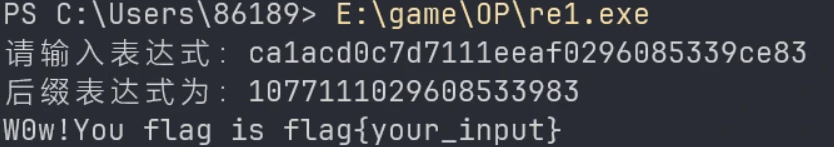
flag{ca1acd0c7d7111eeaf0296085339ce83}
Android -SM4/so动调
发现是SM4标准加密
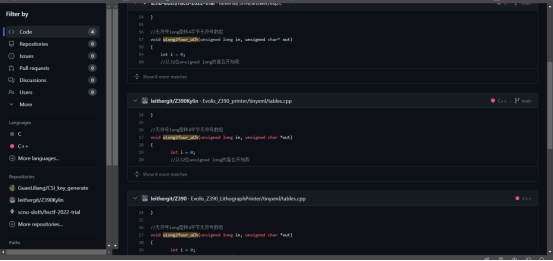
包名
com.moible.midand
so名
lib midand
寻找方法:
readResourceFileBytes
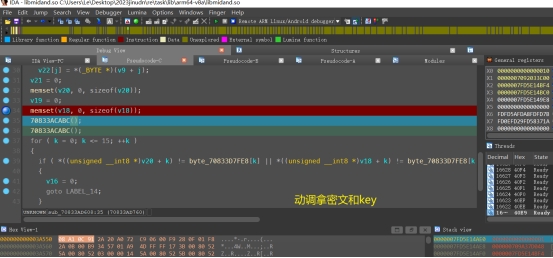
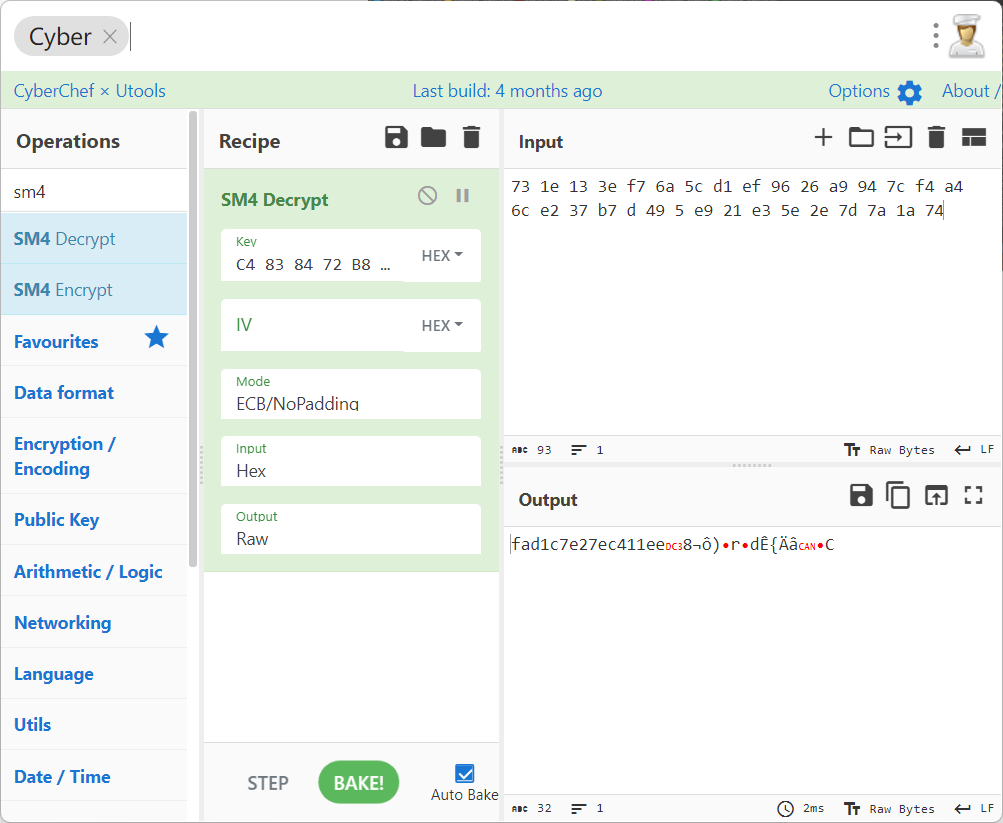
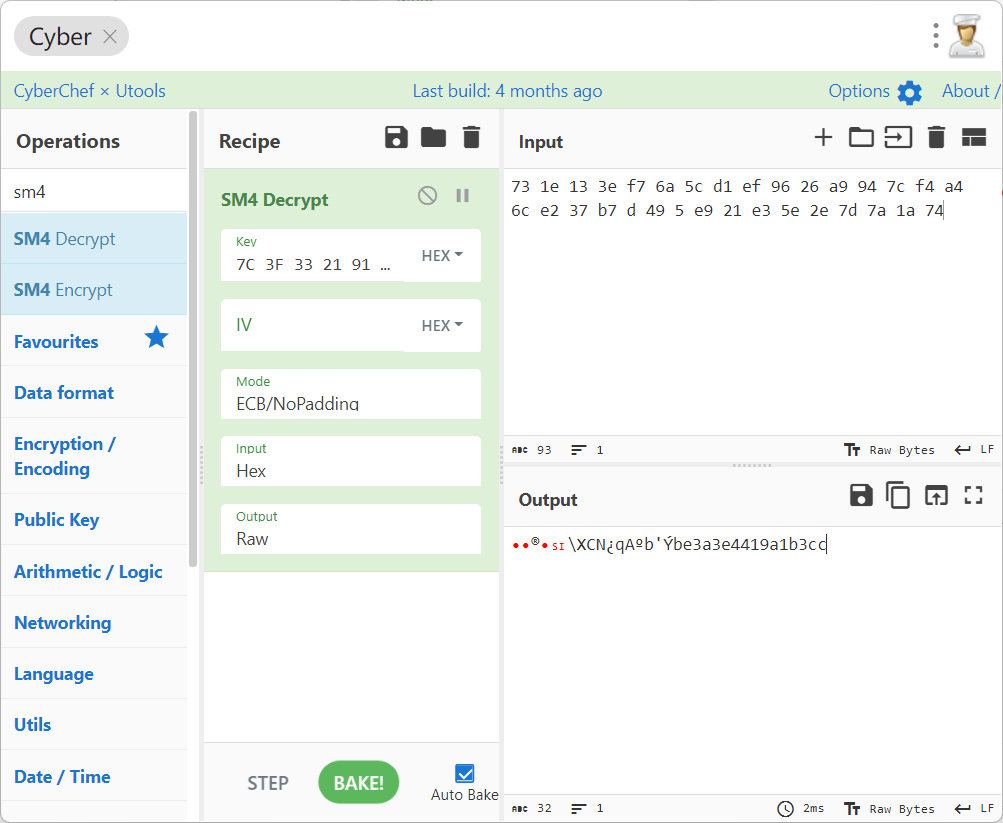
要解密的密文:
73 1e 13 3e f7 6a 5c d1 ef 96 26 a9 94 7c f4 a4 6c e2 37 b7 d 49 5 e9 21 e3 5e 2e 7d 7a 1a 74
这是两串秘钥,分别解密
C4 83 84 72 B8 E1 60 BA 5D 99 5A 6B E3 67 40 17
7C 3F 33 21 91 1C FA 54 8F 35 30 73 DD 2B 80 A7
分别解密(解密两次)
两部分的flag
flag{fad1c7e27ec411eebe3a3e4419a1b3cc}
MISC
来都来了 - 伪加密
伪加密使用java -jar ZipCenOp.jar r 压缩包
打开的字符base64解密
芙宁娜 - pyc隐写=stegosaurus
图片上的base64解码差5位
ZmxhZ3tiYzgzOTRhYS03ZTMyLTQ3ZTgtYTlmZC0xYmY2ODNhZg==
flag{bc8394aa-7e32-47e8-a9fd-1bf683af
010可以找到图片下方盖住的16进制hex->string
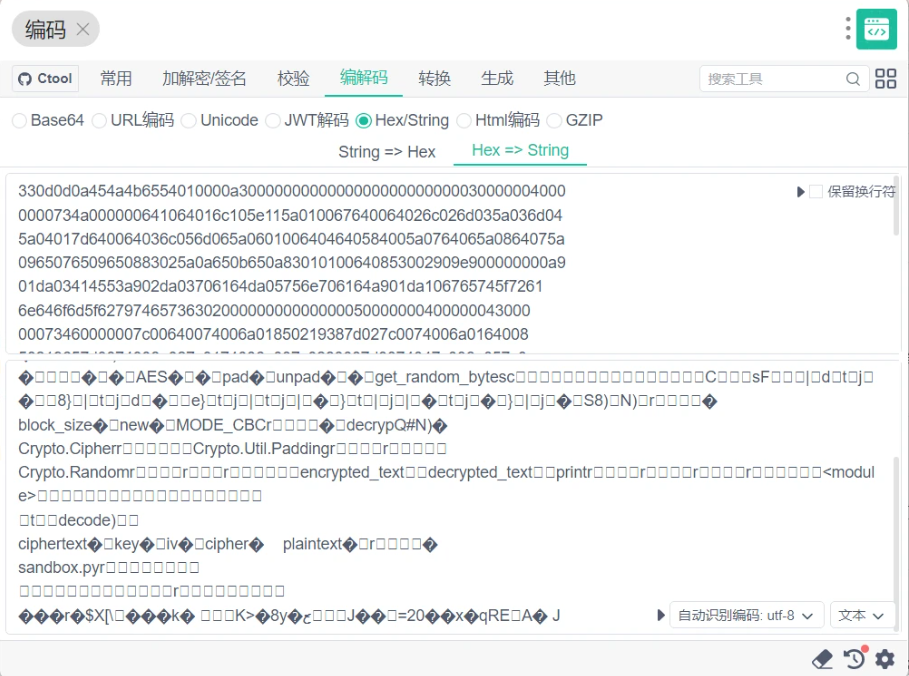
发现可能是python代码,将所有16进制代码取出来重组成pyc文件,stegosaurus-master pyc隐写得出剩下的几位
8e8f}
flag{bc8394aa-7e32-47e8-a9fd-1bf683af8e8f}
honor - steghide隐写
binwalk发现藏了张jpg图片
foremost 分离出来
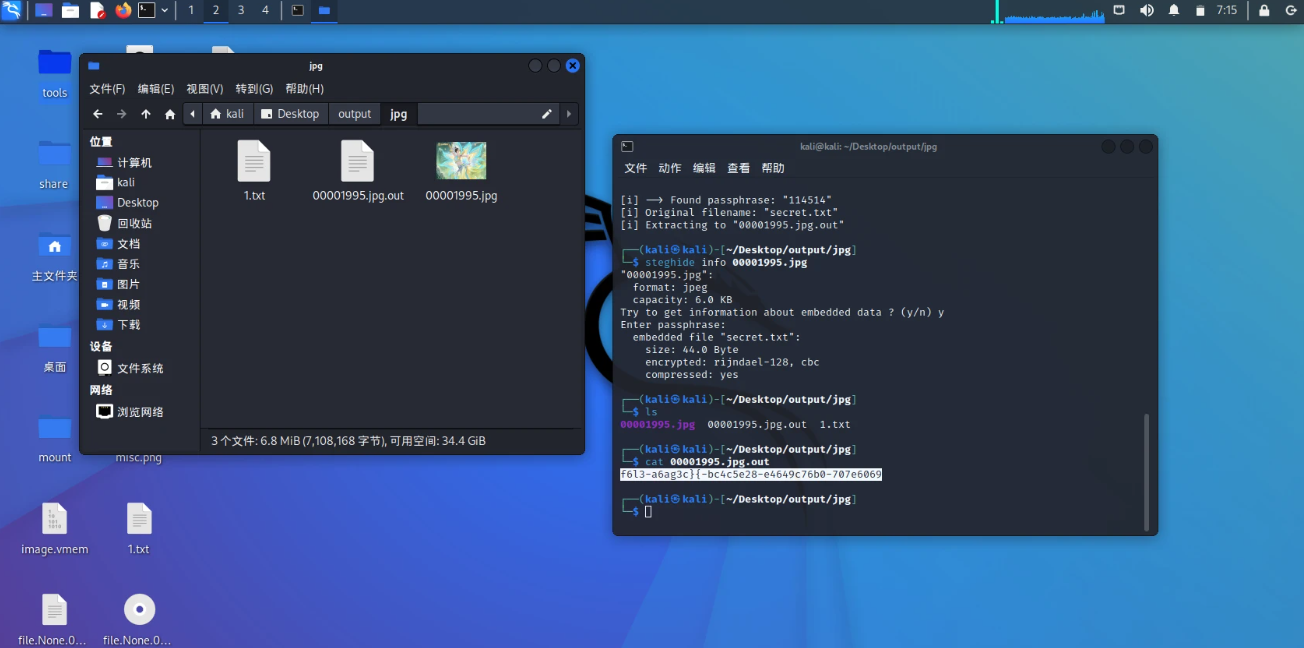
steghide隐写
stegseek暴破密码
解题步骤如下
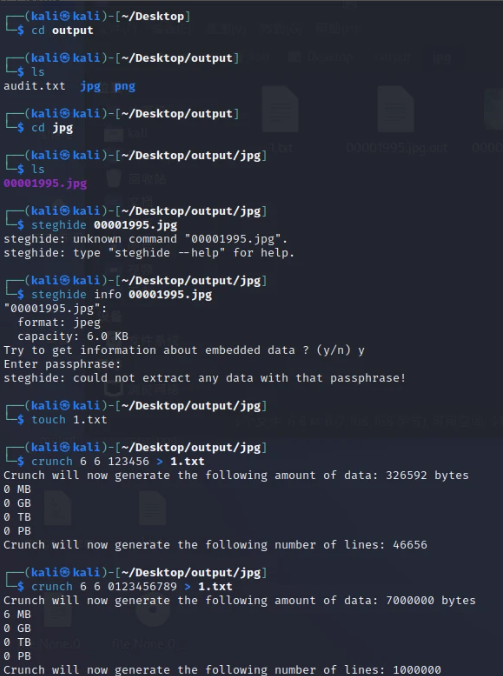
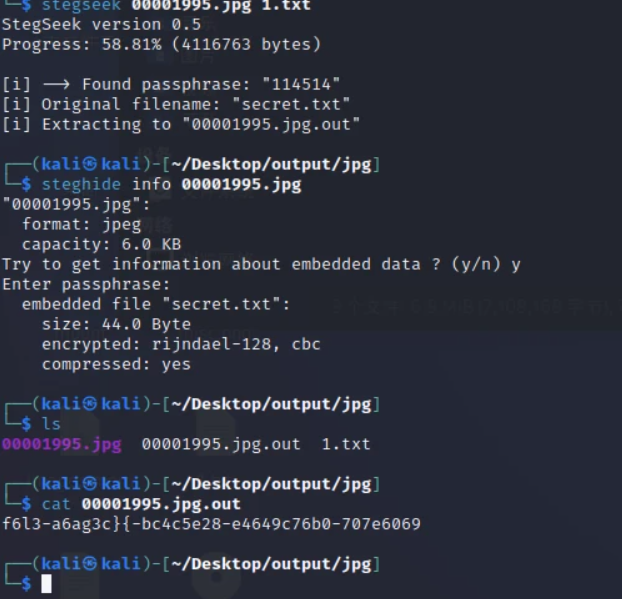
解出来 工具梭
fence密码
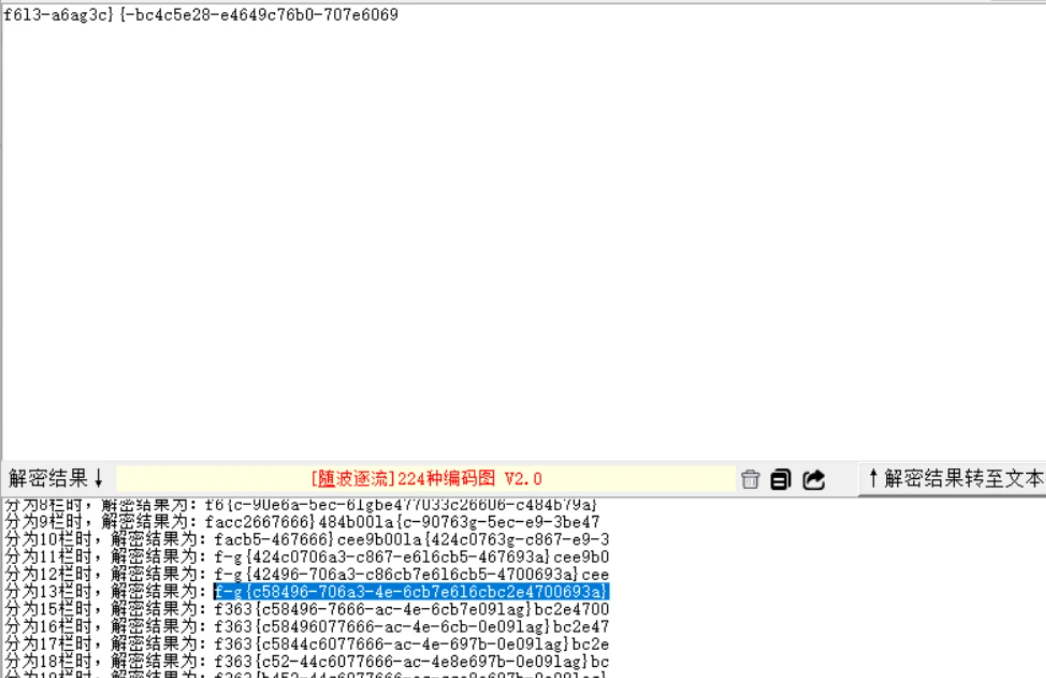
flag{c58496-706a3-4e-6cb7e6l6cbc2e4700693a}
Crypto
hakiehs
塞尔达传说(Pi)
塞尔达文字
席卡古文
格鲁德文
海利亚文



flag{linkzeldaganon}
我看看谁还不会RSA
RSA =.=
1 | import gmpy2 |
