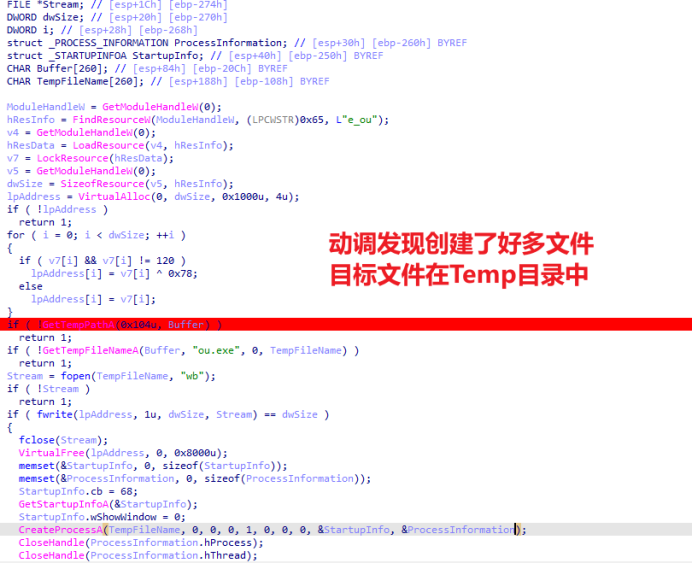
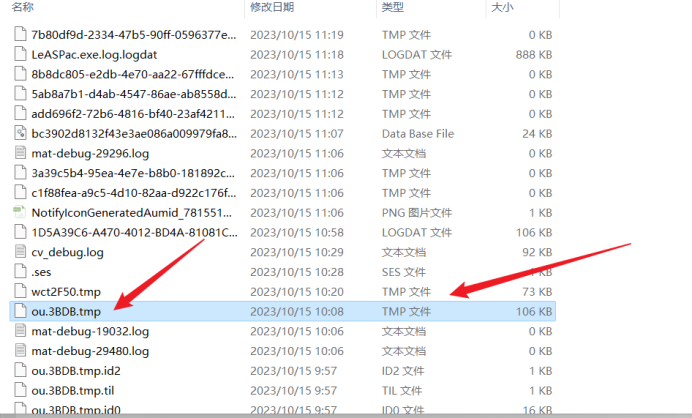
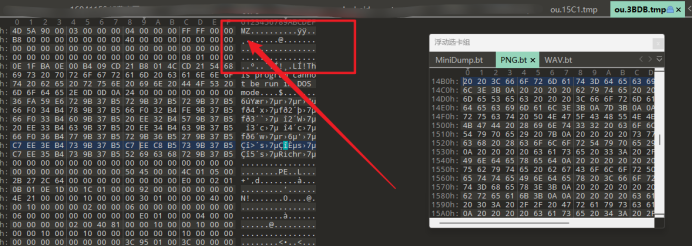
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
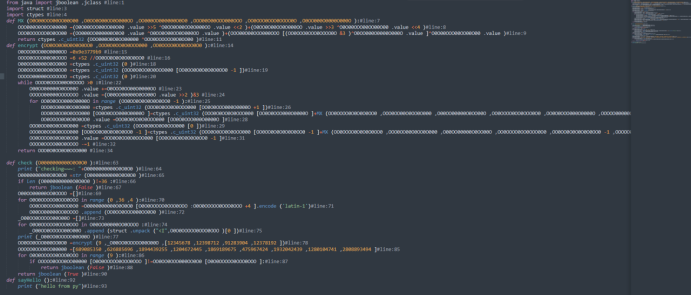
| #define _CRT_SECURE_NO_WARNINGS 1
#define _CRT_SECURE_NO_WARNINGS 1
#include<stdio.h>
#include<stdint.h>
#define DELTA 0x9e3779b9
#define MX (((z>>5^y<<2) + (y>>3^z<<4)) ^ ((sum^y) + (key[(p&3)^e] ^ z)))
using namespace std;
unsigned int cipher[9] = { 689085350 ,626885696 ,1894439255 ,1204672445 ,1869189675 ,475967424 ,1932042439 ,1280104741 ,2808893494 };
unsigned int key[4] = { 12345678 ,12398712 ,91283904 ,12378192 };
void xxtea(uint32_t* v, int n, uint32_t const key[4])
{
uint32_t y, z, sum;
unsigned p, rounds, e;
if (n < -1)
{
n = -n;
rounds = 6 + 52 / n;
sum = rounds * DELTA;
y = v[0];
do
{
e = (sum >> 2) & 3;
for (p = n - 1; p > 0; p--)
{
z = v[p - 1];
y = v[p] -= MX;
}
z = v[n - 1];
y = v[0] -= MX;
sum -= DELTA;
} while (--rounds);
}
}
int main()
{
xxtea(cipher, -9, key);
for (int i = 0; i < 9; i++)
{
printf("0x%x,0x%x,0x%x,0x%x,", *((char*)&cipher[i] + 0) & 0xff, *((char*)&cipher[i] + 1) & 0xff, *((char*)&cipher[i] + 2) & 0xff, *((char*)&cipher[i] + 3) & 0xff);
}
printf("\n");
int Dec[] =
{
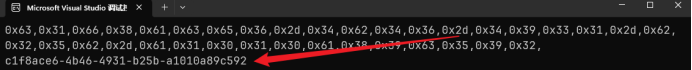
0x63,0x31,0x66,0x38,0x61,0x63,0x65,0x36,0x2d,0x34,0x62,0x34,0x36,0x2d,0x34,0x39,0x33,0x31,0x2d,0x62,0x32,0x35,0x62,0x2d,0x61,0x31,0x30,0x31,0x30,0x61,0x38,0x39,0x63,0x35,0x39,0x32
};
for (int i = 0; i < 36; i++)
printf("%c", Dec[i]);
return 0;
}
|