前言
不得不说,本科组真是太卷了,,,,哇哇哇哇哇哇
最近打的比赛 这下真成取证手了,hhhh
前蓝帽,陇剑负责取证,这块misc也是做出来了取证,哈哈哈哈
比赛总共输出2道逆向,2道杂项,题目做着很有手感,(
但是嘞,das的题目不想多说了
看题都能看出来是谁出的 (虽然也做不出来
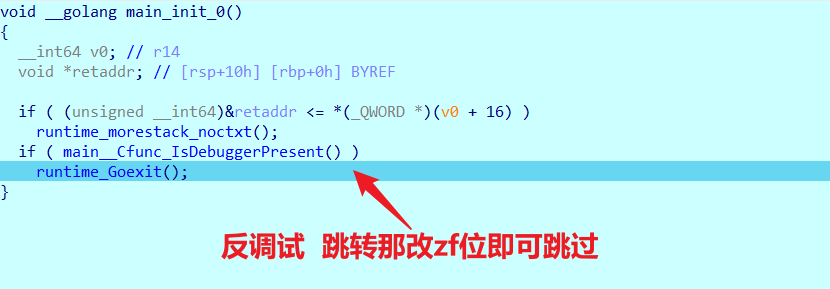
CSGO - GO/base64/反调试
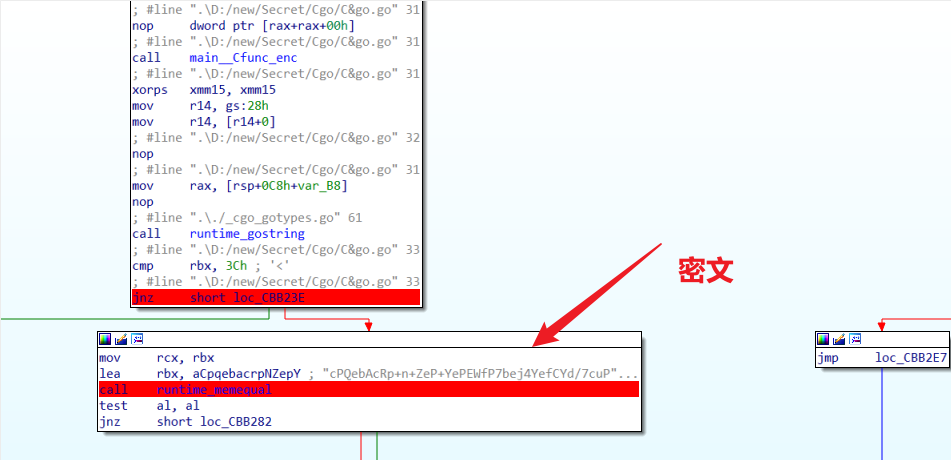
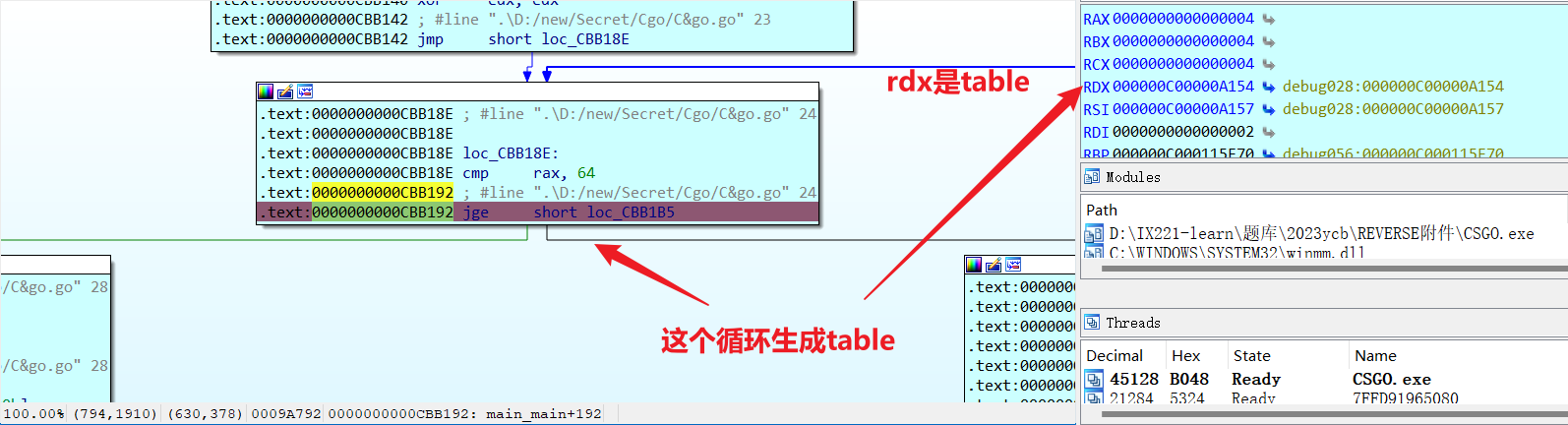
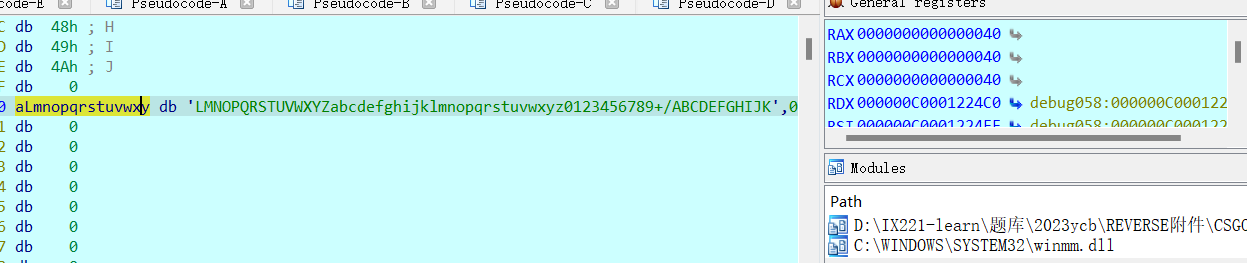
base64,动调出来table表即可得解
有个反调试,过掉即可
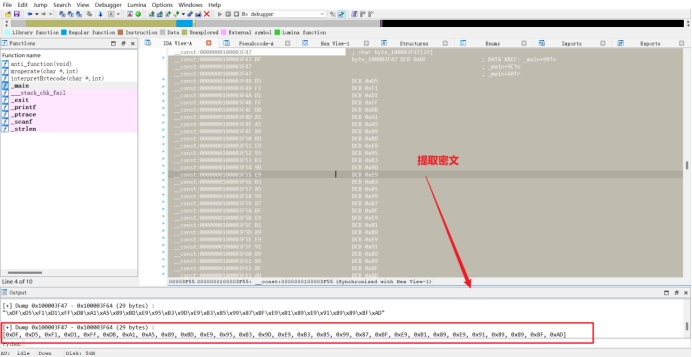
提取密文
动调
1
2
3
4
5
| table: LMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/ABCDEFGHIJK
cipher: cPQebAcRp+n+ZeP+YePEWfP7bej4YefCYd/7cuP7WfcPb/URYeMRbesObi/=
flag:DASCTF{73913519-A0A6-5575-0F10-DDCBF50FA8CA}
|
vm_wo - mac/vm
拿到附件 发现是macos系统文件
拖入ida64 函数很好看
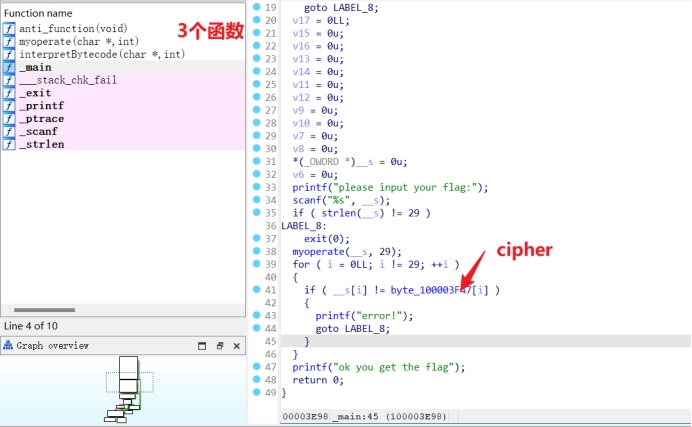
main函数,很明了
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
| int __cdecl main(int argc, const char **argv, const char **envp)
{
__int64 i;
char __s[16];
__int128 v6;
__int128 v7;
__int128 v8;
__int128 v9;
__int128 v10;
__int128 v11;
__int128 v12;
__int128 v13;
__int128 v14;
__int128 v15;
__int128 v16;
__int64 v17;
if ( ptrace(0, 0, (caddr_t)1, 0) == -1 )
goto LABEL_8;
v17 = 0LL;
v15 = 0u;
v16 = 0u;
v13 = 0u;
v14 = 0u;
v11 = 0u;
v12 = 0u;
v9 = 0u;
v10 = 0u;
v7 = 0u;
v8 = 0u;
*(_OWORD *)__s = 0u;
v6 = 0u;
printf("please input your flag:");
scanf("%s", __s);
if ( strlen(__s) != 29 )
LABEL_8:
exit(0);
myoperate(__s, 29);
for ( i = 0LL; i != 29; ++i )
{
if ( __s[i] != byte_100003F47[i] )
{
printf("error!");
goto LABEL_8;
}
}
printf("ok you get the flag");
return 0;
}
|
1
| encData= [0xDF, 0xD5, 0xF1, 0xD1, 0xFF, 0xDB, 0xA1, 0xA5, 0x89, 0xBD, 0xE9, 0x95, 0xB3, 0x9D, 0xE9, 0xB3, 0x85, 0x99, 0x87, 0xBF, 0xE9, 0xB1, 0x89, 0xE9, 0x91, 0x89, 0x89, 0x8F, 0xAD]
|
主要的指令
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
| __int64 __fastcall myoperate(char *a1, int a2)
{
__int64 v2;
_QWORD v5[2];
_QWORD v6[2];
_QWORD v7[2];
_QWORD v8[2];
LODWORD(v2) = a2;
dword_100008003 = -1091715345;
if ( ptrace(0, 0, (caddr_t)1, 0) == -1 )
exit(0);
if ( (int)v2 >= 1 )
{
v2 = (unsigned int)v2;
do
{
v8[0] = 0x20D01011903001ALL;
*(_QWORD *)((char *)v8 + 7) = 0x300010201180702LL;
BYTE2(v8[0]) = *a1;
interpretBytecode((char *)v8, 15);
v7[0] = 0x20D02011903001ALL;
*(_QWORD *)((char *)v7 + 7) = 0x400010201180602LL;
BYTE2(v7[0]) = vm_body;
interpretBytecode((char *)v7, 15);
v6[0] = 0x20D03011903001ALL;
*(_QWORD *)((char *)v6 + 7) = 0x500010201180502LL;
BYTE2(v6[0]) = vm_body;
interpretBytecode((char *)v6, 15);
v5[0] = 0x20D04011903001ALL;
*(_QWORD *)((char *)v5 + 7) = 0x600010201180402LL;
BYTE2(v5[0]) = vm_body;
interpretBytecode((char *)v5, 15);
*a1++ = ((unsigned __int8)vm_body >> 5) | (8 * vm_body);
--v2;
}
while ( v2 );
}
return 0LL;
}
|
发现指令是写死的,解密即可
exp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| if __name__ == '__main__':
encData = [0xDF, 0xD5, 0xF1, 0xD1, 0xFF, 0xDB, 0xA1, 0xA5, 0x89, 0xBD, 0xE9, 0x95, 0xB3, 0x9D, 0xE9, 0xB3, 0x85,
0x99,
0x87, 0xBF, 0xE9, 0xB1, 0x89, 0xE9, 0x91, 0x89, 0x89, 0x8F, 0xAD, 0x57]
length = len(encData)
for i in range(length):
temp = encData[i]
temp = ((temp >> 3) | (temp << 5)) & 0xff
temp ^= 0xBE
temp = ((temp >> 4) | (temp << 4)) & 0xff
temp ^= 0xED
temp = ((temp >> 5) | (temp << 3)) & 0xff
temp ^= 0xBE
temp = ((temp >> 6) | (temp << 2)) & 0xff
temp ^= 0xEF
temp = ((temp >> 7) | (temp << 1)) & 0xff
print(chr(temp), end='')
|
DASCTF{you_are_right_so_cool}
拿到附件看到有一部分裸漏的,直接crc爆破修复
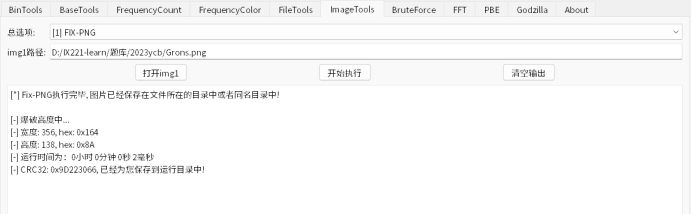
得到了这个。。
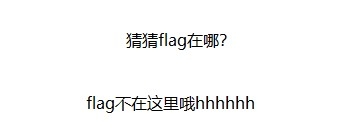
010发现了fivenumber 字样
并且pk 03 04修复一下
解压得到vzbtrvplnnvphsqkxsiqibroou
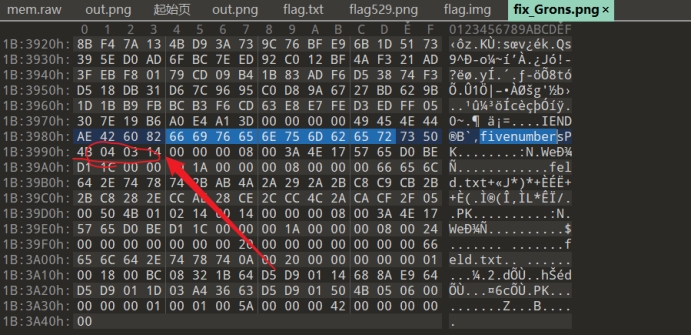
根据fivenumber暴破
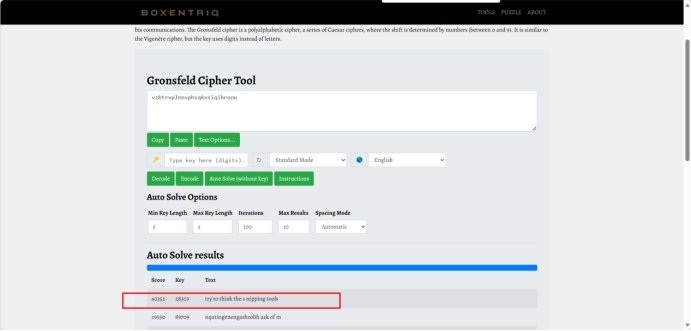
得到try to think the s nipping tools
联想到前段时间*CTF的snipping tools
使用同款工具 得解
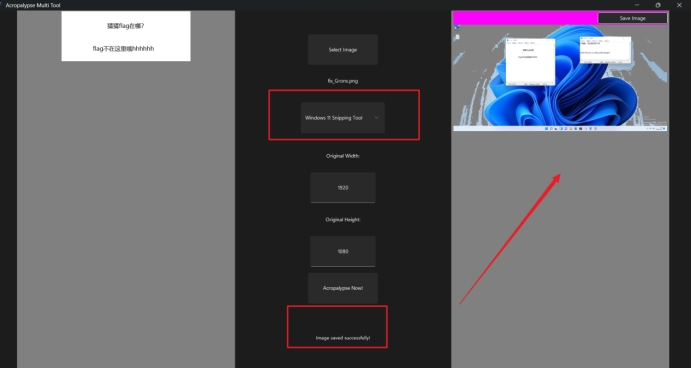
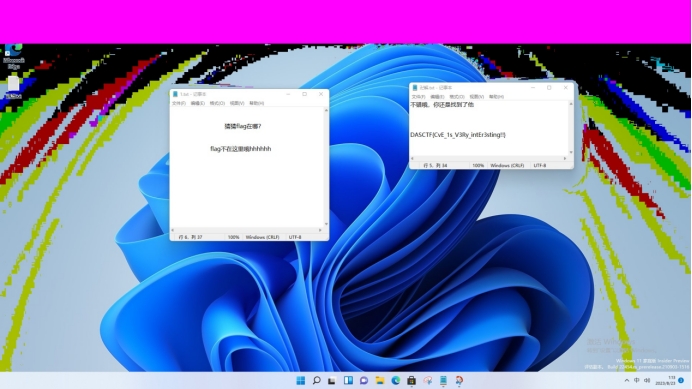
CvE_1s_V3Ry_intEr3sting!!
Matryoshka - veracrypt/零宽隐写
winhex打开挂载,找到了encrypt
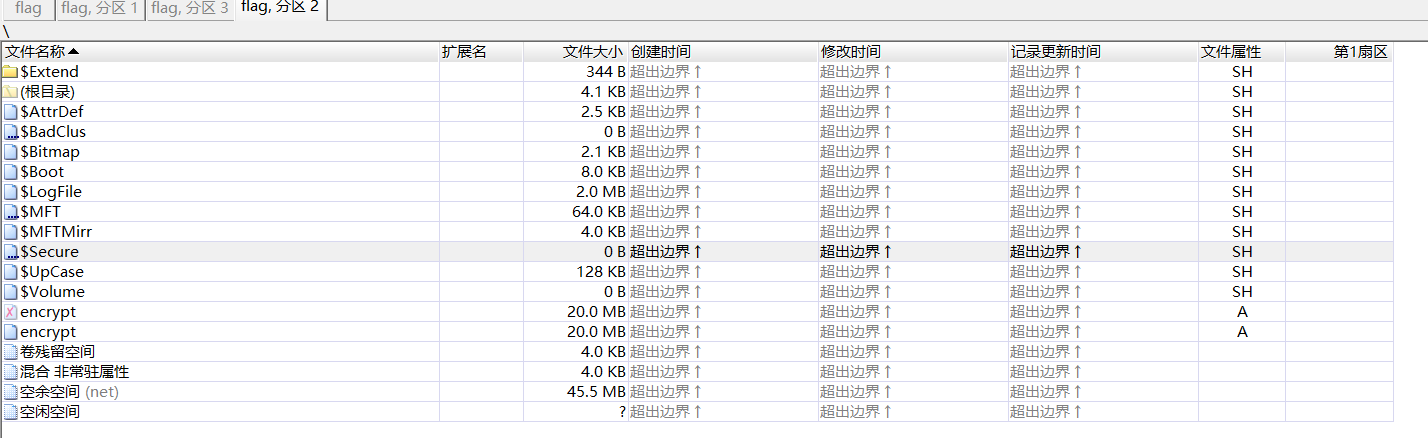
3个flag分区
得到这几个附件
提示盲水印
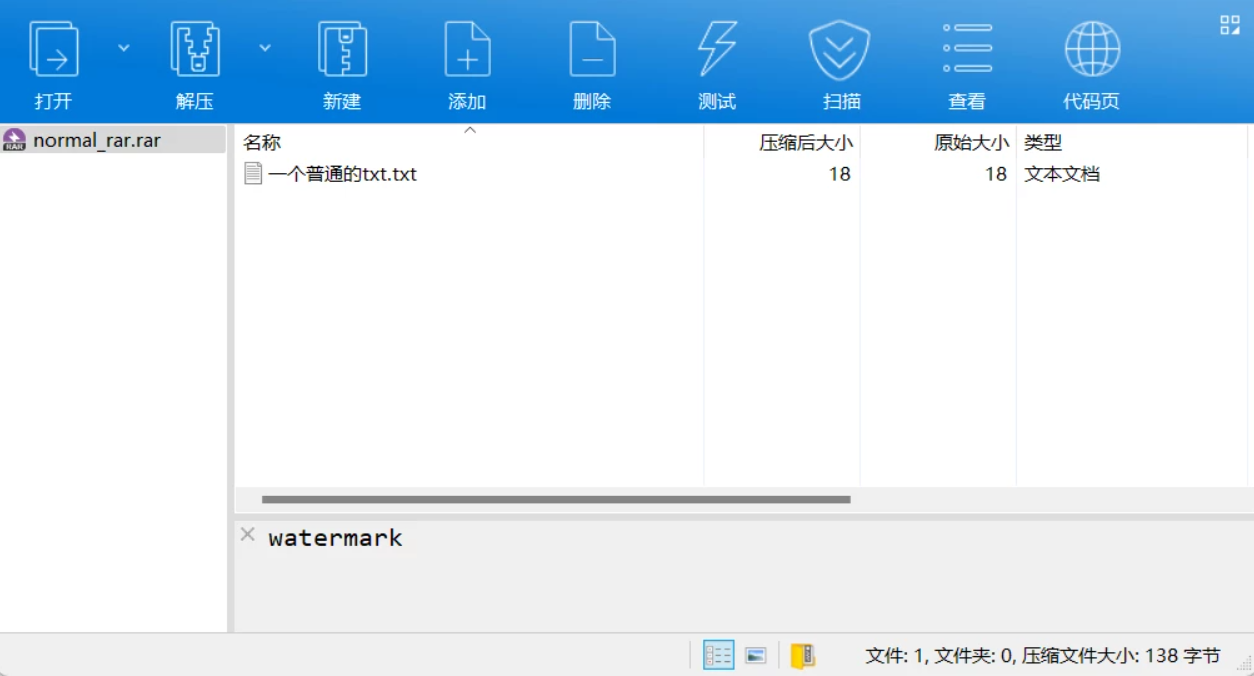
解出encrypt密码:watermark_is_fun
将encrypt使用veracrypt挂载,得到flag.txt
明显看见了零宽隐写
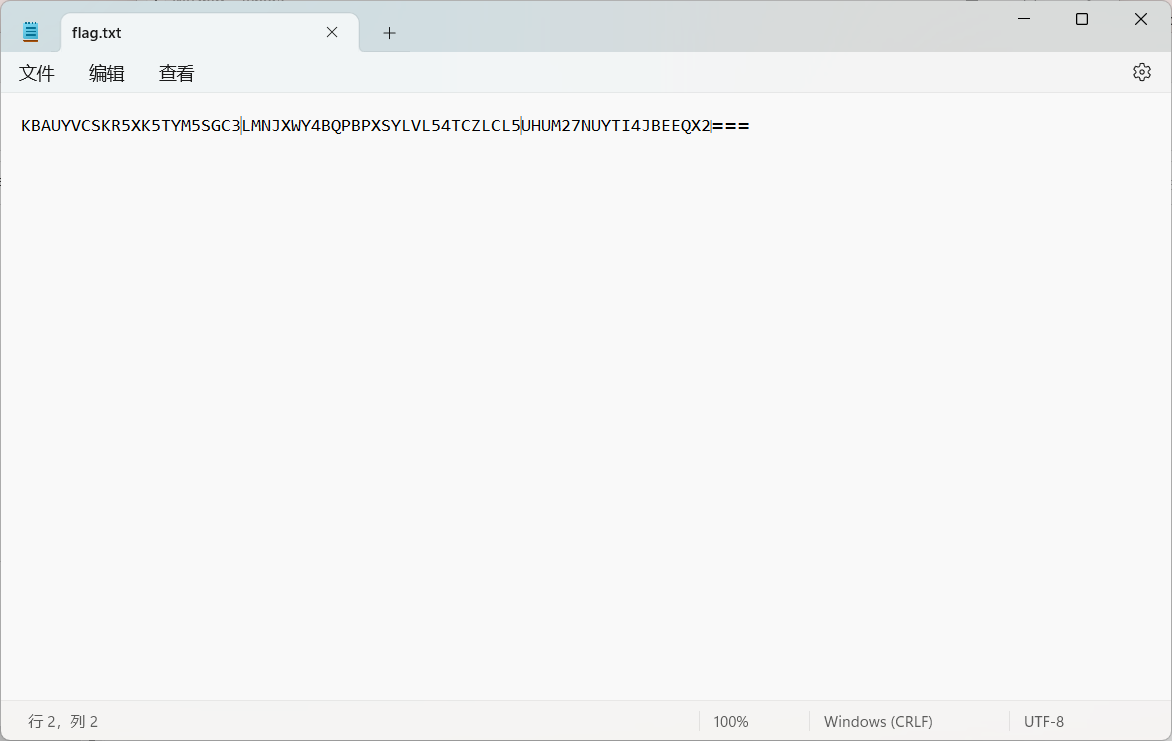
零宽隐写得到一个key:Matryoshka
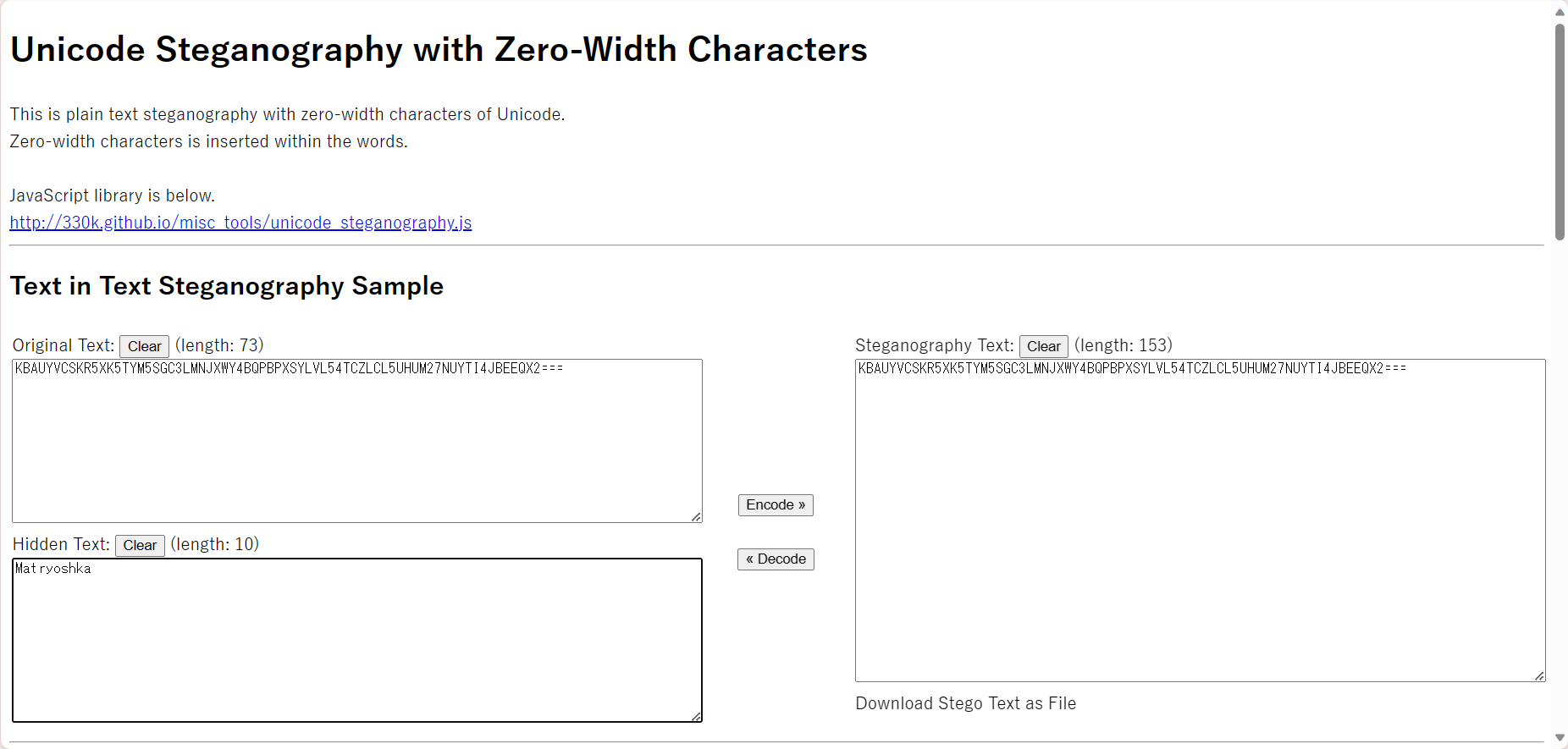
将flag(密文)
base32解码得到PALTRT{uvxgdamljolp0x_yau_y1eb_hz3_m14q!!!}
猜测维吉尼亚解码,使用上面key解码得解
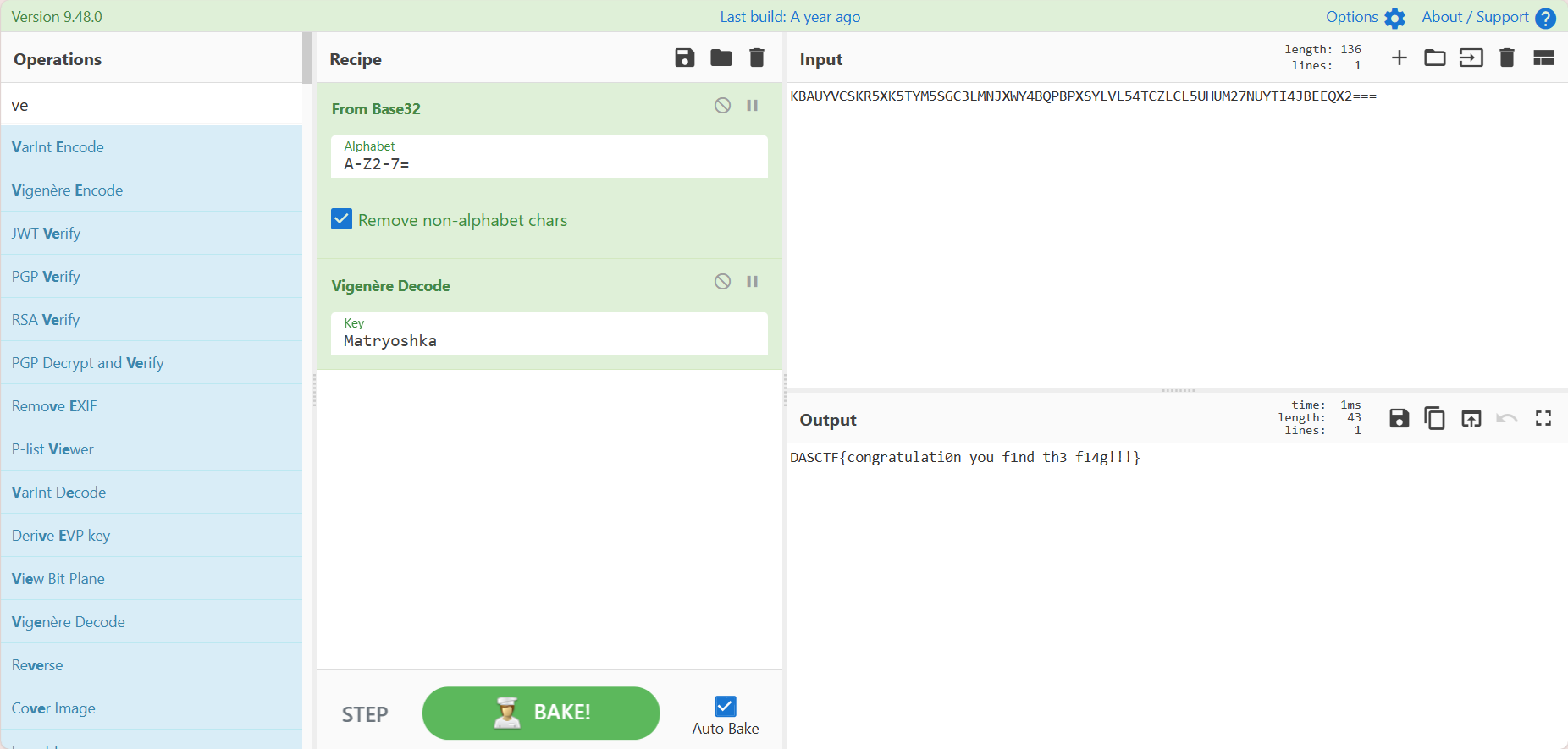
DASCTF{congratulati0n_you_f1nd_th3_f14g!!!}



















