2023通配符CTF-*CTF-WriteUp
goGpt
分析:
使用 go_parser恢复go符号表
使用方法:
1 | 在ida64中按下按键 `alt + P` 选择`go_parser.py` |
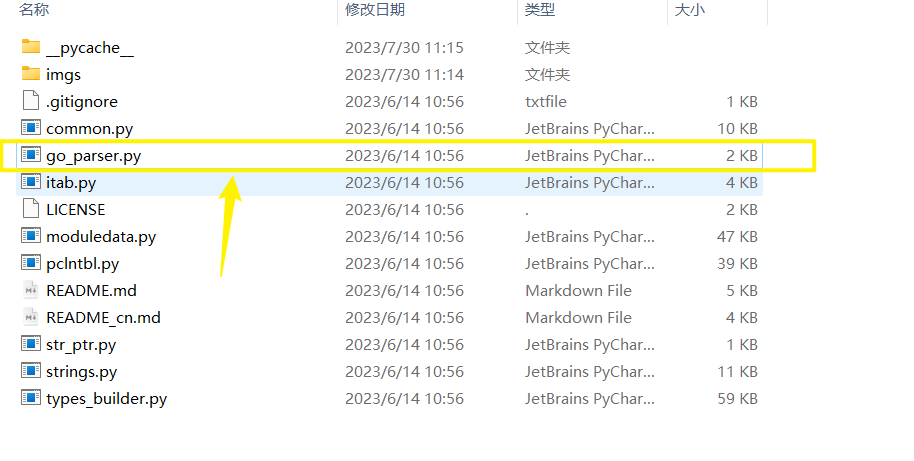
插件项目地址:GitHub - 0xjiayu/go_parser:IDAPro 的又一个 Golang 二进制解析器
恢复后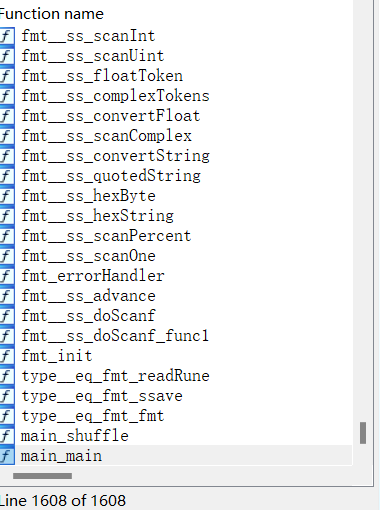
mian函数
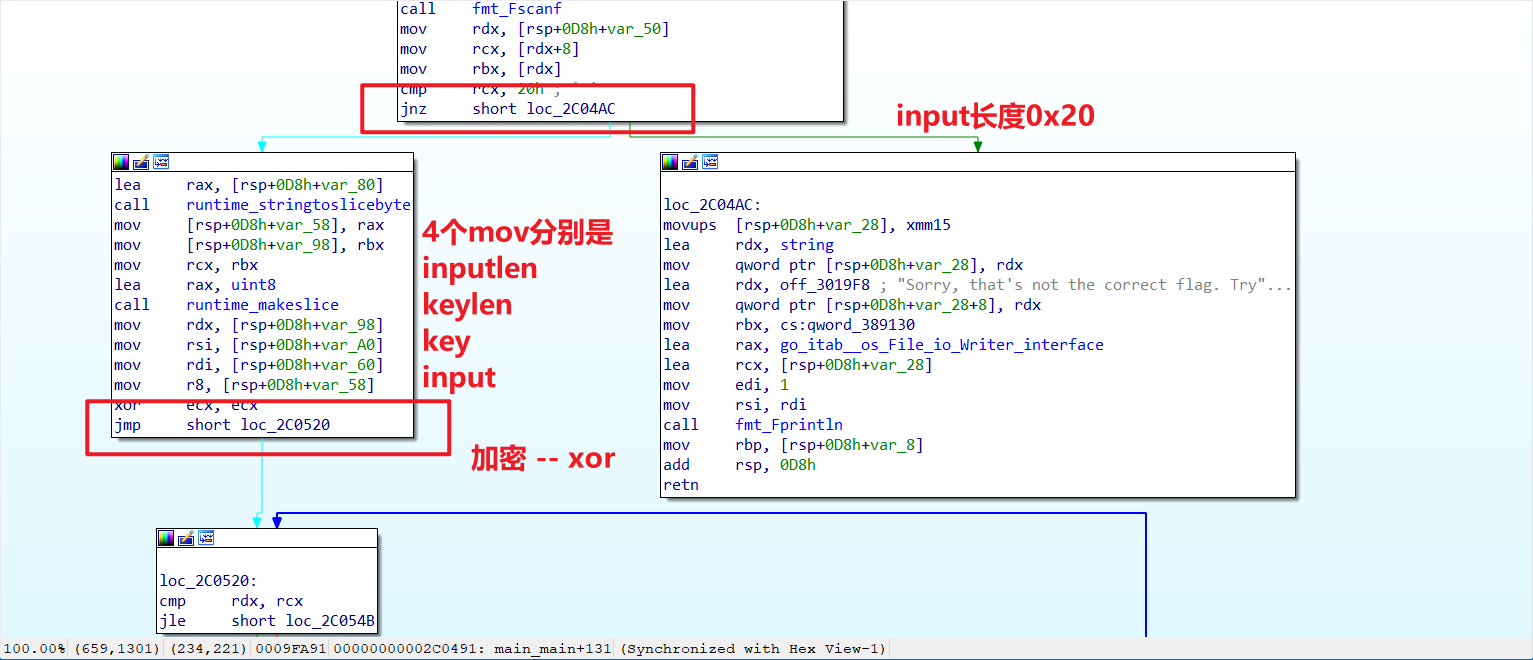
往下
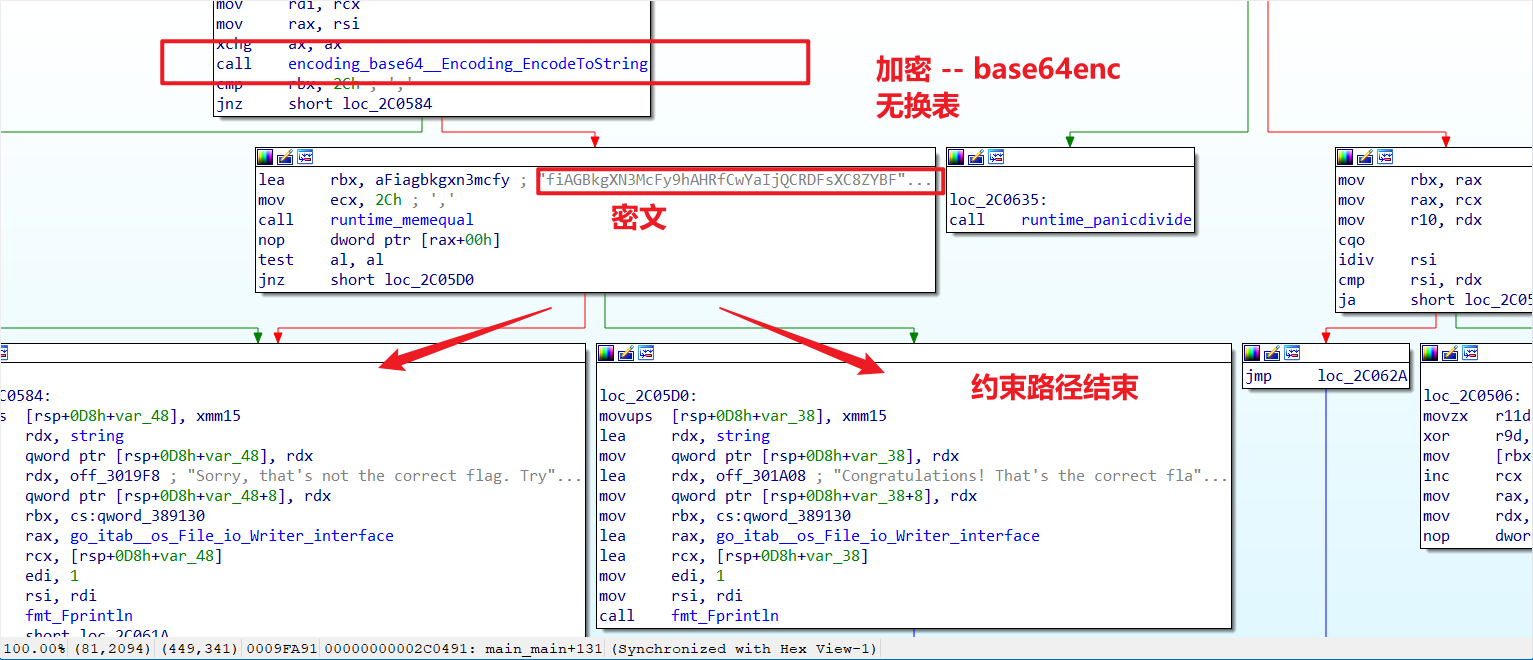
解密:
接着呢
动调找到key
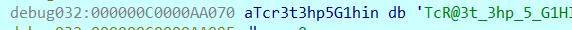
然后编写脚本解密即可
exp
1 | x="fiAGBkgXN3McFy9hAHRfCwYaIjQCRDFsXC8ZYBFmEDU=" |
ez_code
法一:终端运行
题目描述 –>powershell脚本语言
将整个powershell代码在powershell中运行,得到
将 最后面的| .${-``} 去掉,得到这一段
这一段(上图)是假的
程序的结构大概是这样 xxx1 = "xxx2"; "xxx3" | xxx4
然后再跑这一段,这一段是 "xxx2"
得到真的代码
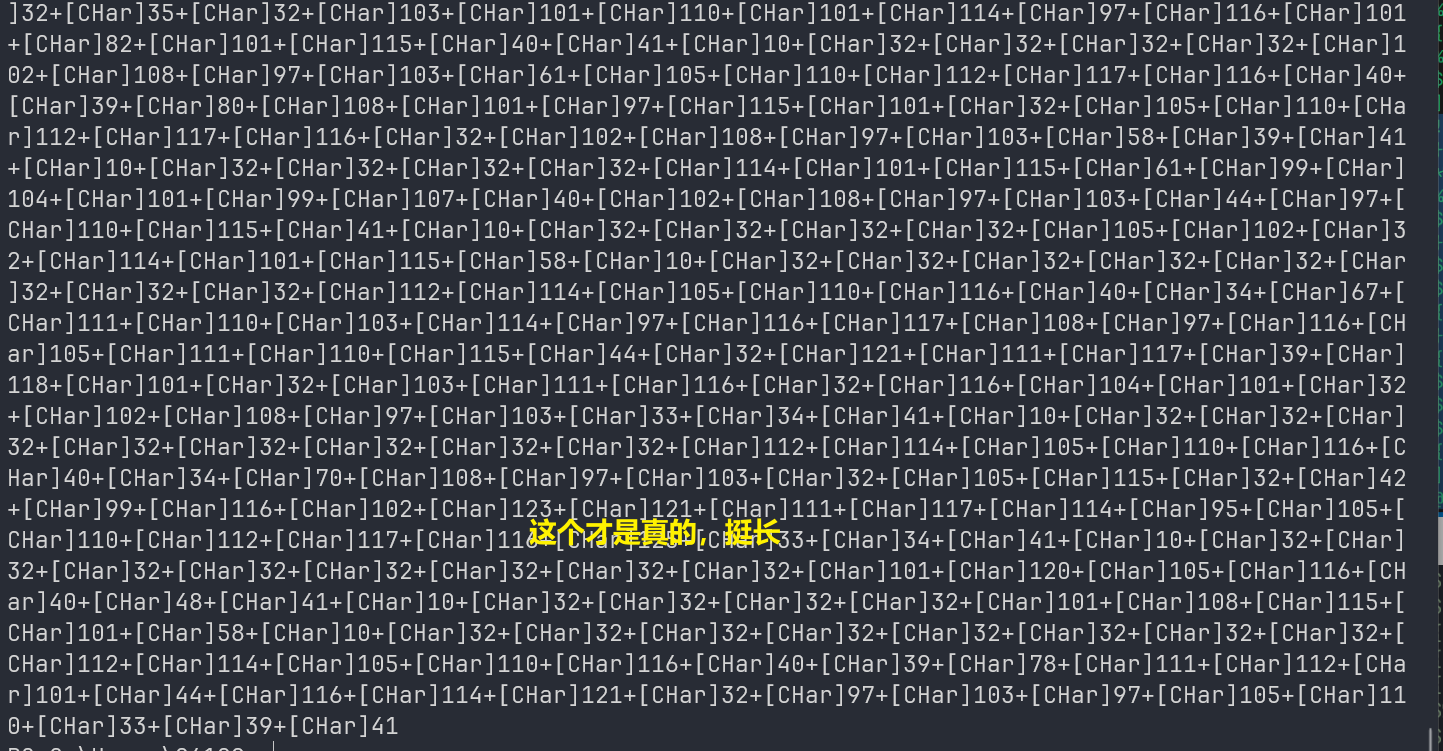
将此代码cv跑一遍得到python代码
1 | class chiper(): |
法二:vscode动调
打开vscode,创建文件1.PS1
复制完就一行,很长
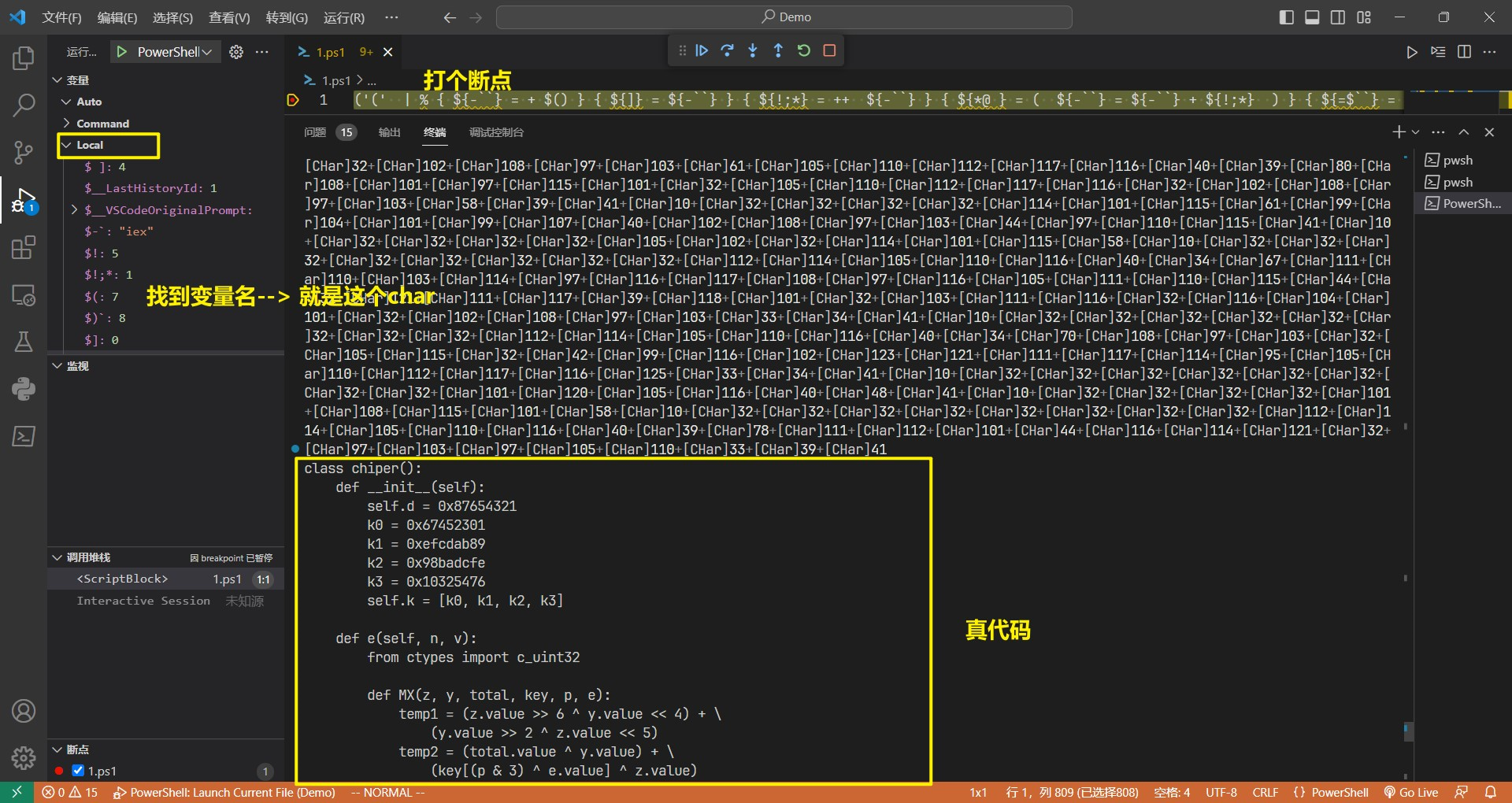
打个断点
运行,在local板块找到变量${@*}
因为,变量有两段,两段中间有个;, 第一段是真的,第二段是假的
所以下断运行,得到的是第一段的结果(真的)
然后cv结果,即可得到python源代码
解密:
魔改xxtea
写脚本解密
Exp
1 |
|
old language
谷歌识图
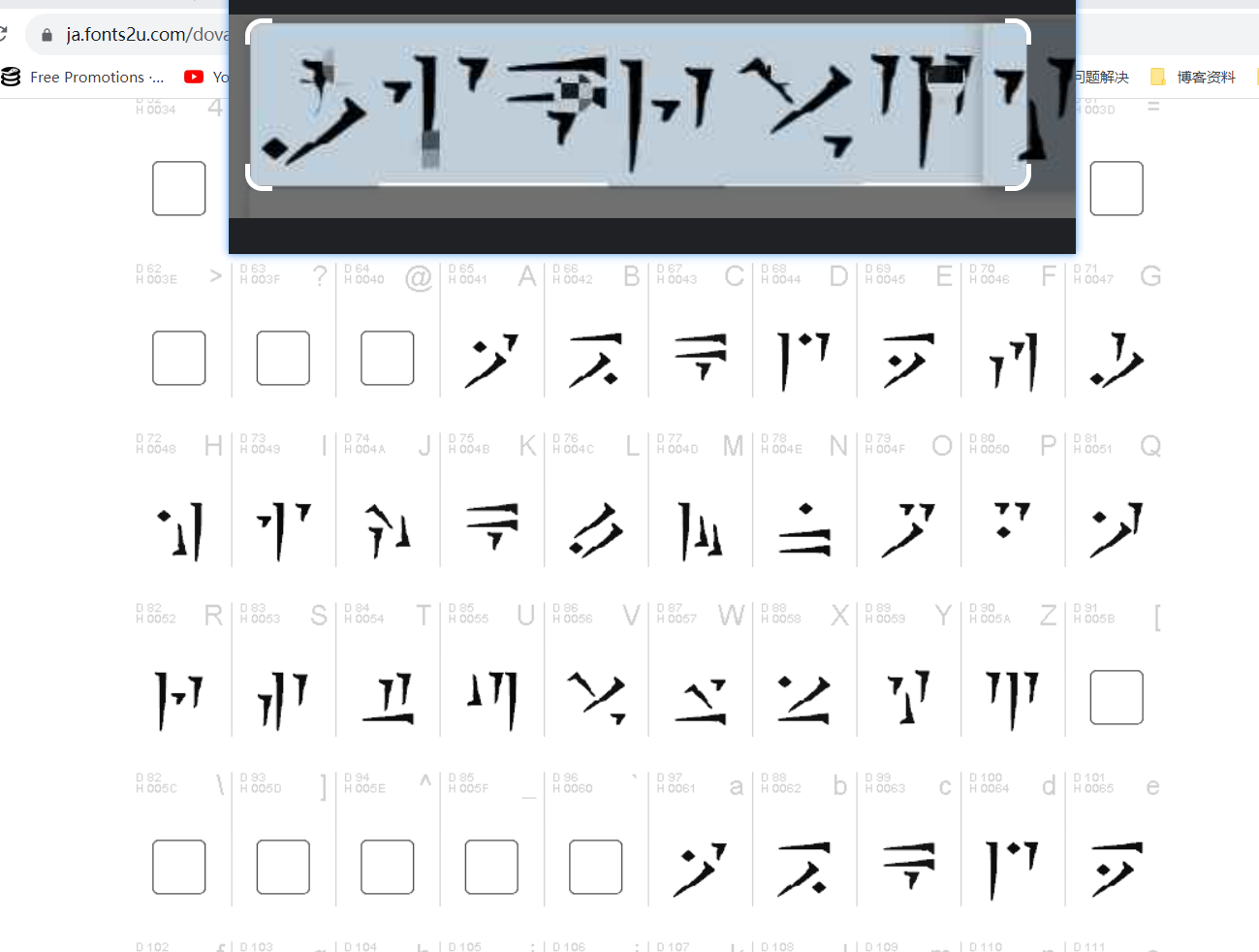
dovahkiin字体
逐个对照即可
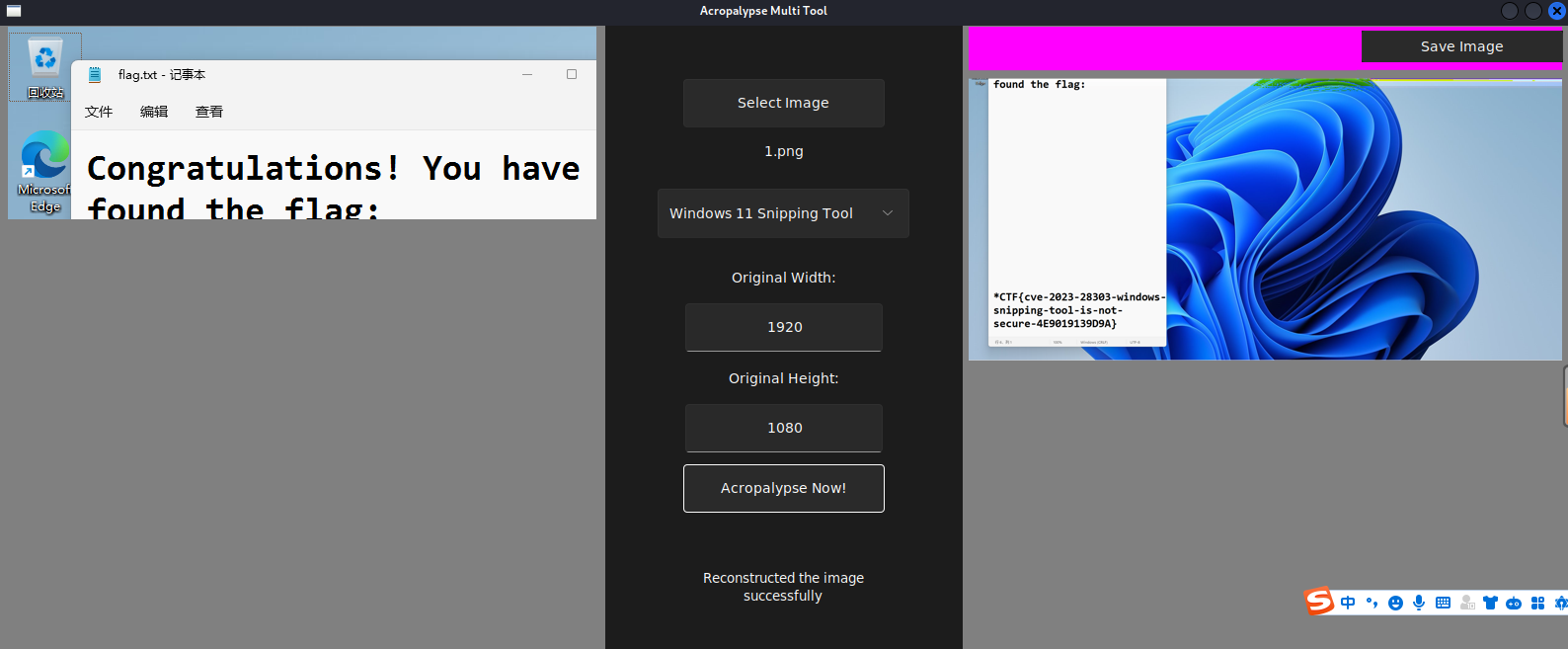
snippingTools
Google搜索 github CVE-2023-28303
搜出个工具
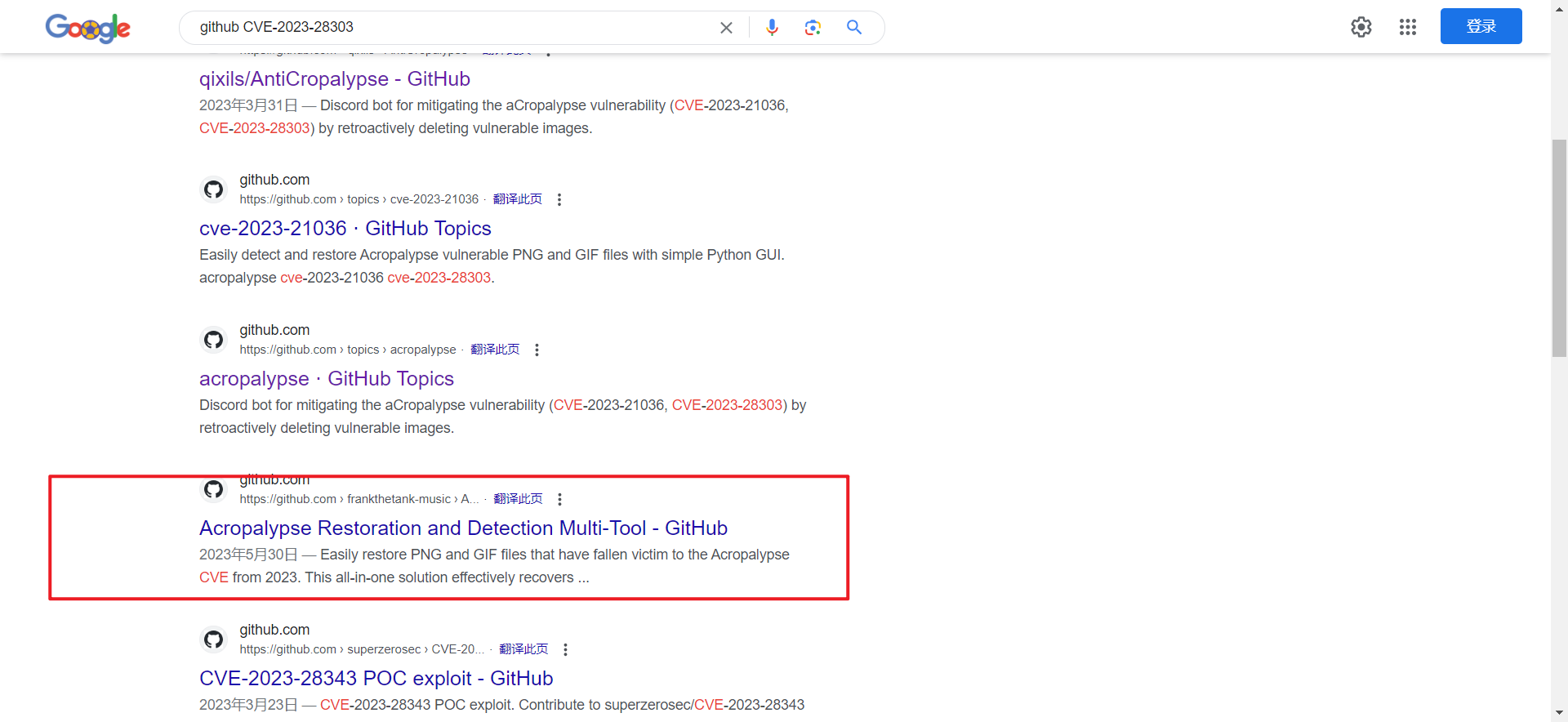
安装好 上传图片 即可得解
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 摘星阁!
