2023巅峰极客WriteUp
rev - g0Re - elfUPX/AES/base64
查壳,发现是upx打包的elf文件
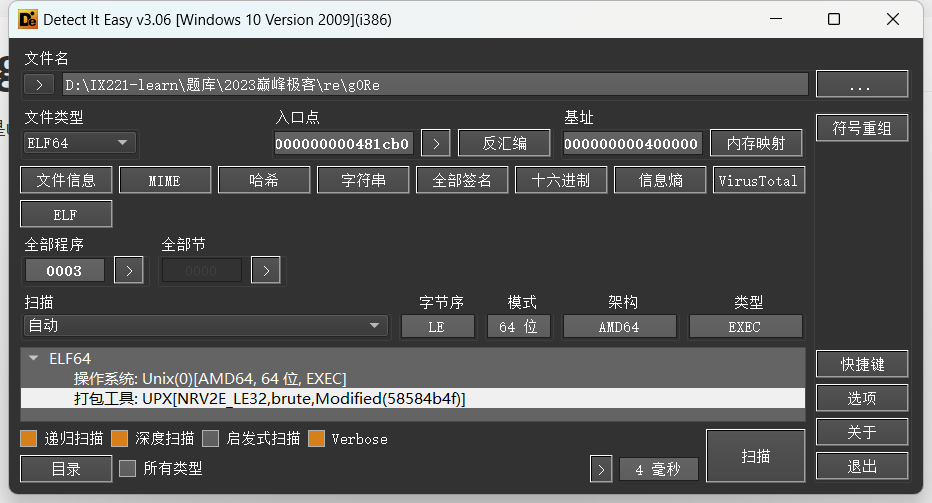
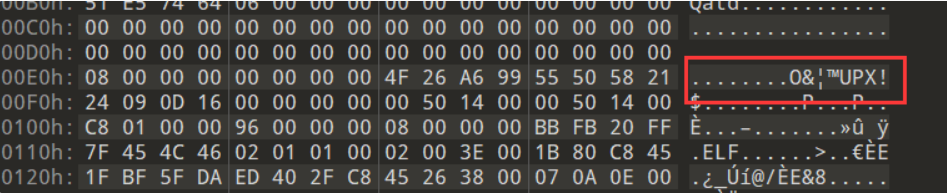
upx -d 脱壳脱不掉,010中发现魔改的特征码
将OKXX –> UPX! 即可
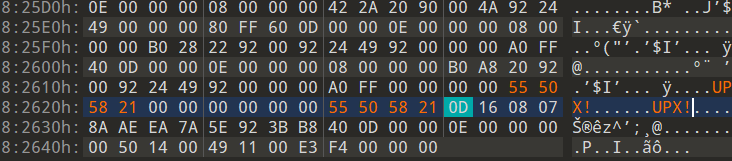
脱壳后拖入ida64分析
main函数审计代码
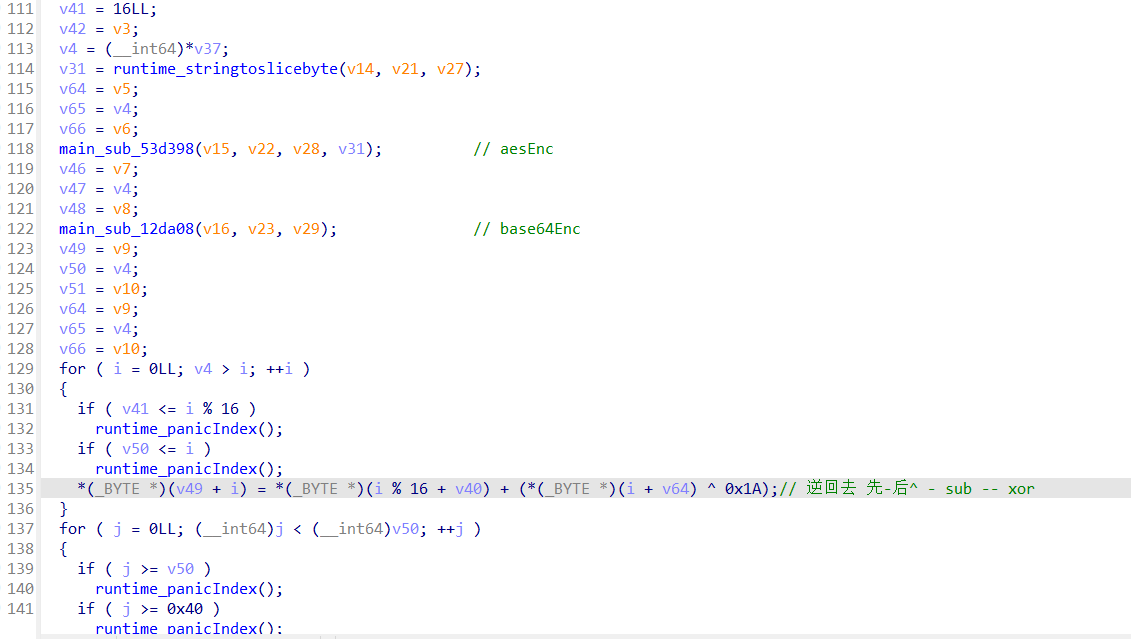
动调提取密文
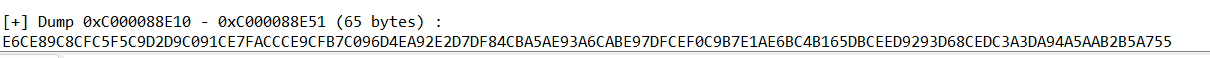
1 | E6CE89C8CFC5F5C9D2D9C091CE7FACCCE9CFB7C096D4EA92E2D7DF84CBA5AE93A6CABE97DFCEF0C9B7E1AE6BC4B165DBCEED9293D68CEDC3A3DA94A5AAB2B5A755 |
然后提取aes的密钥 - 按a键转化为字符串 – > wvgitbygwbk2b46d
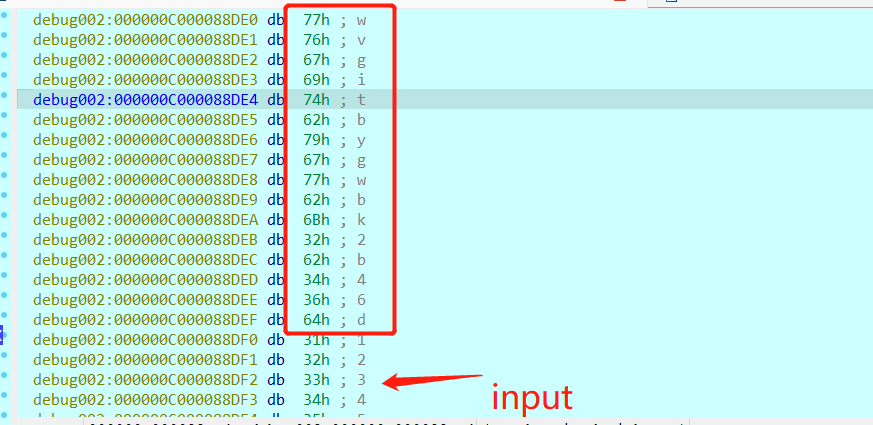
发现base64换表了,提取表

1 | 456789}#IJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123ABCDEFGH |
最后动调sub,找出sub的key –> key还是这个
cyberchef—-!!!
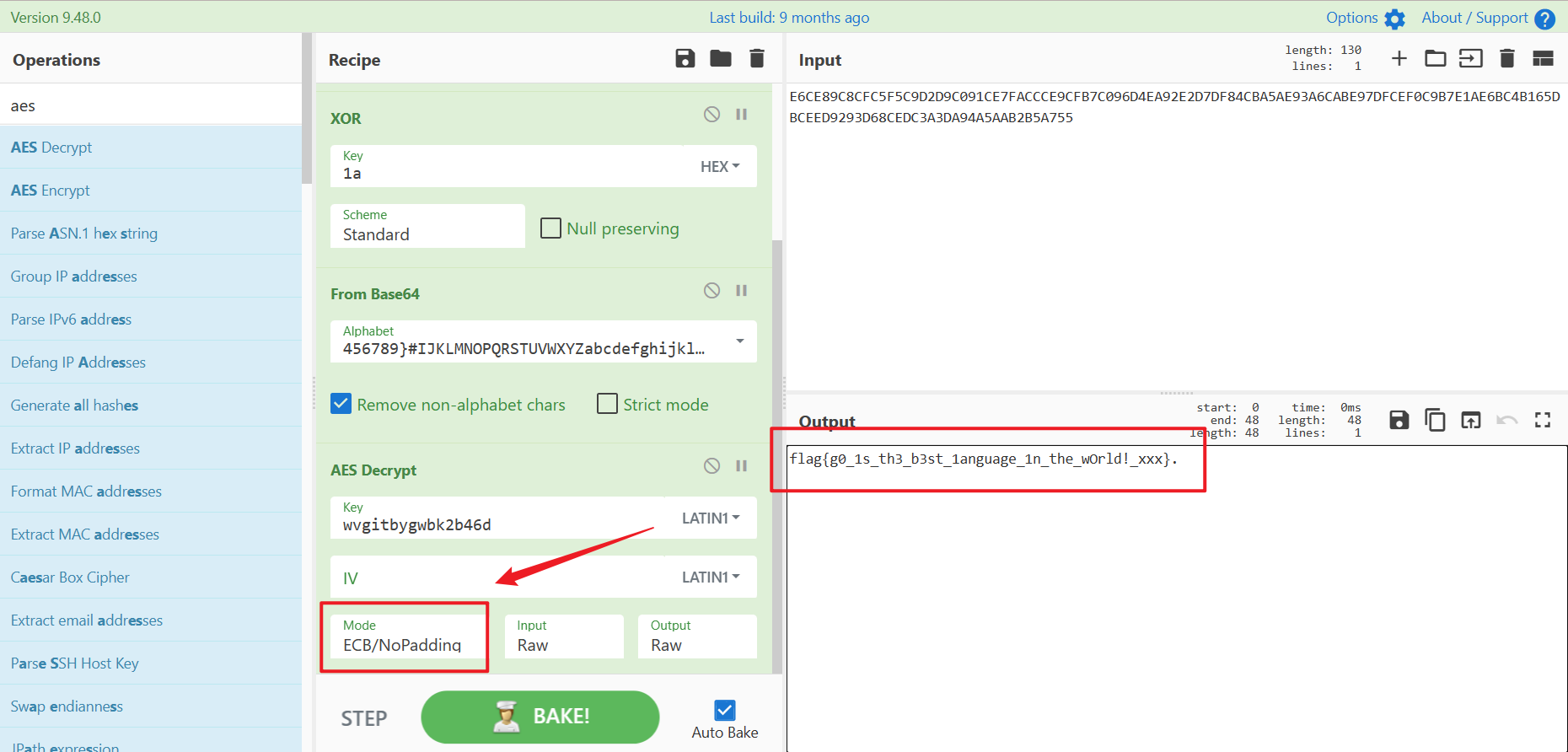
flag{g0_1s_th3_b3st_1anguage_1n_the_wOrld!_xxx}
exp
1 | from Crypto.Cipher import AES |
misc - foundme
strings find.DMP | grep “flag”
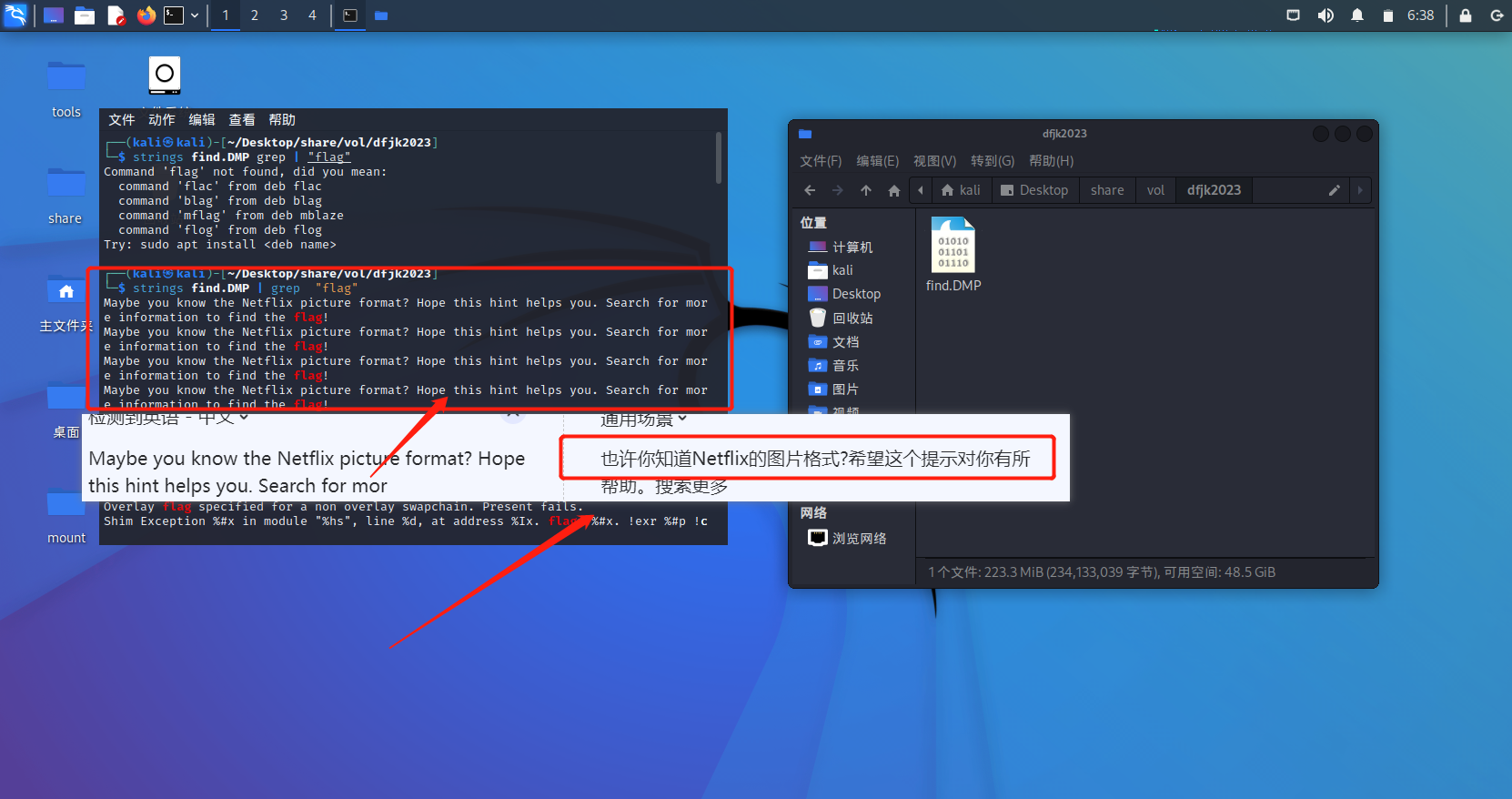
根据提示 搜索引擎搜索
avif文件是一种图像的格式,推测,找出此文件打开即为flag

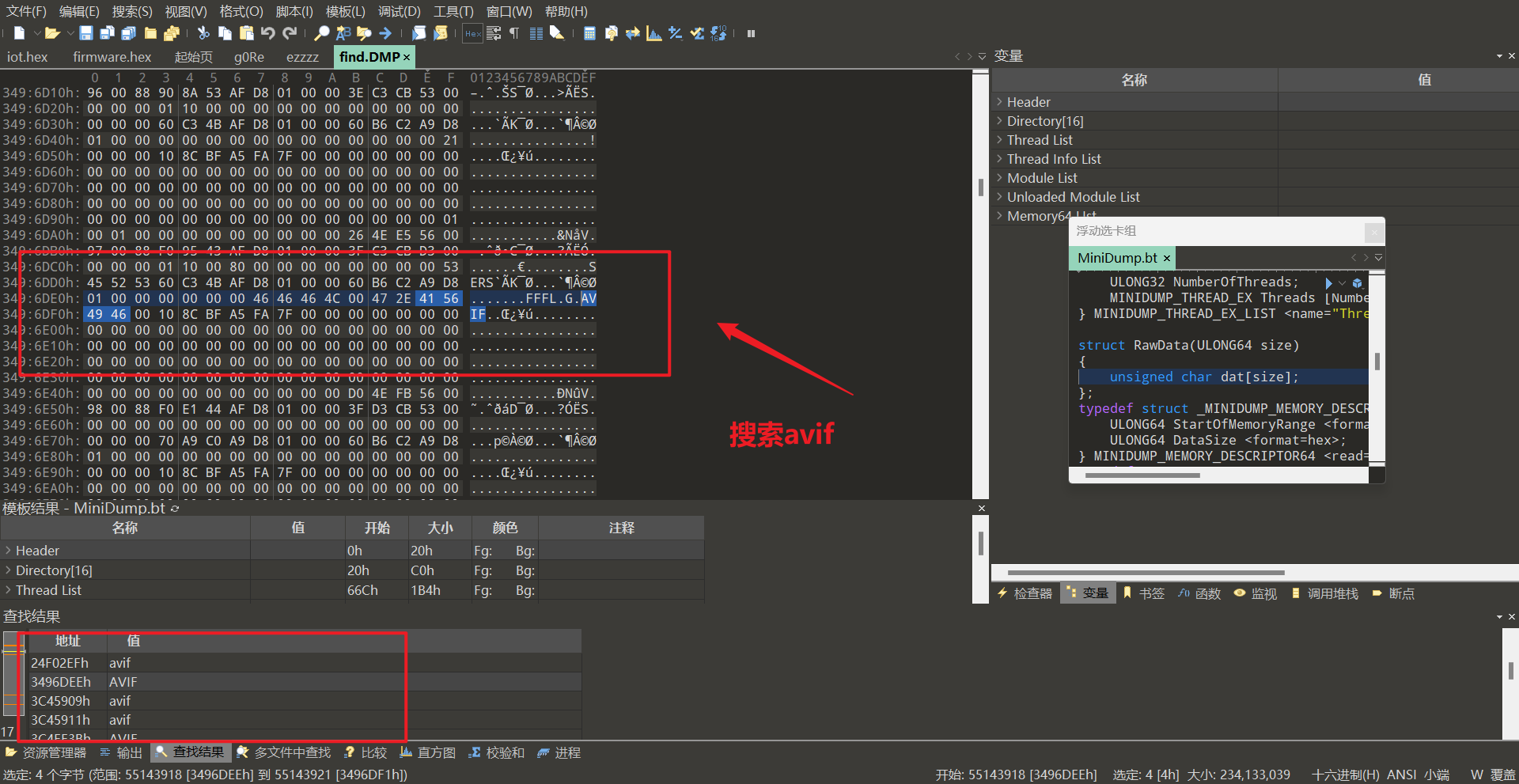
在010中搜索avif,发现一个flag标识
将此文件提取出来
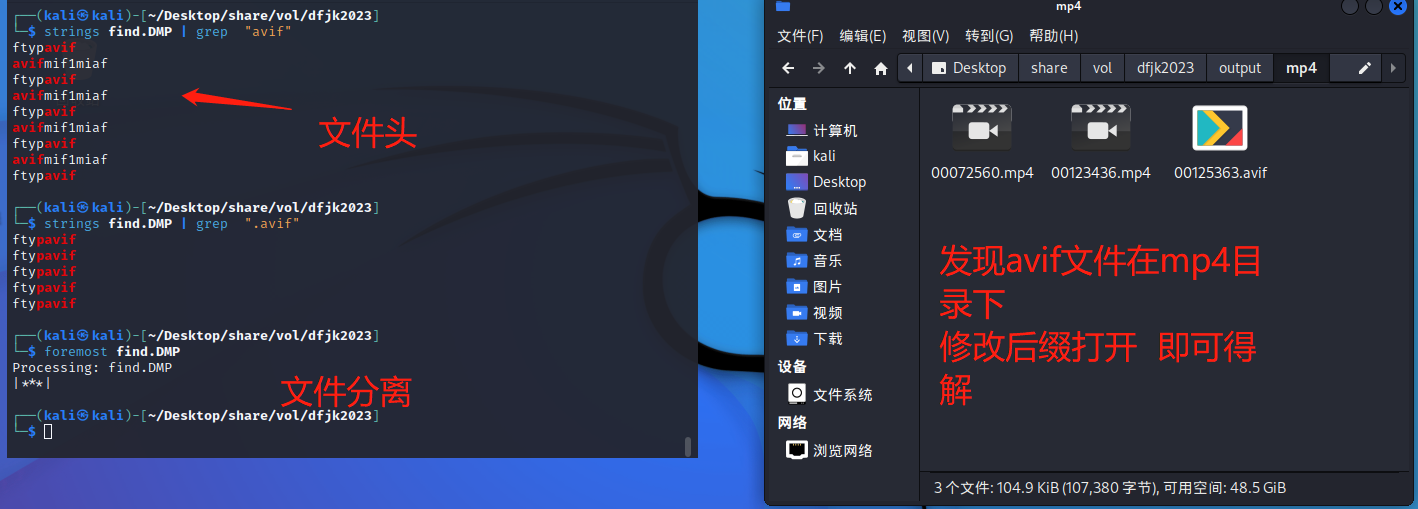

flag(YOung_Ju57_fomward}
misc - song - ape=deppsound/ook
文件拖入010分析,在结尾发现PK标识,而文件无文件头,猜测时PK文件,修改
504B0304
成功打开(虽然报错-文件格式错误/
在\ppt\media中发现
image4.png文件过大,
其余wmf文件

对比两个png文件
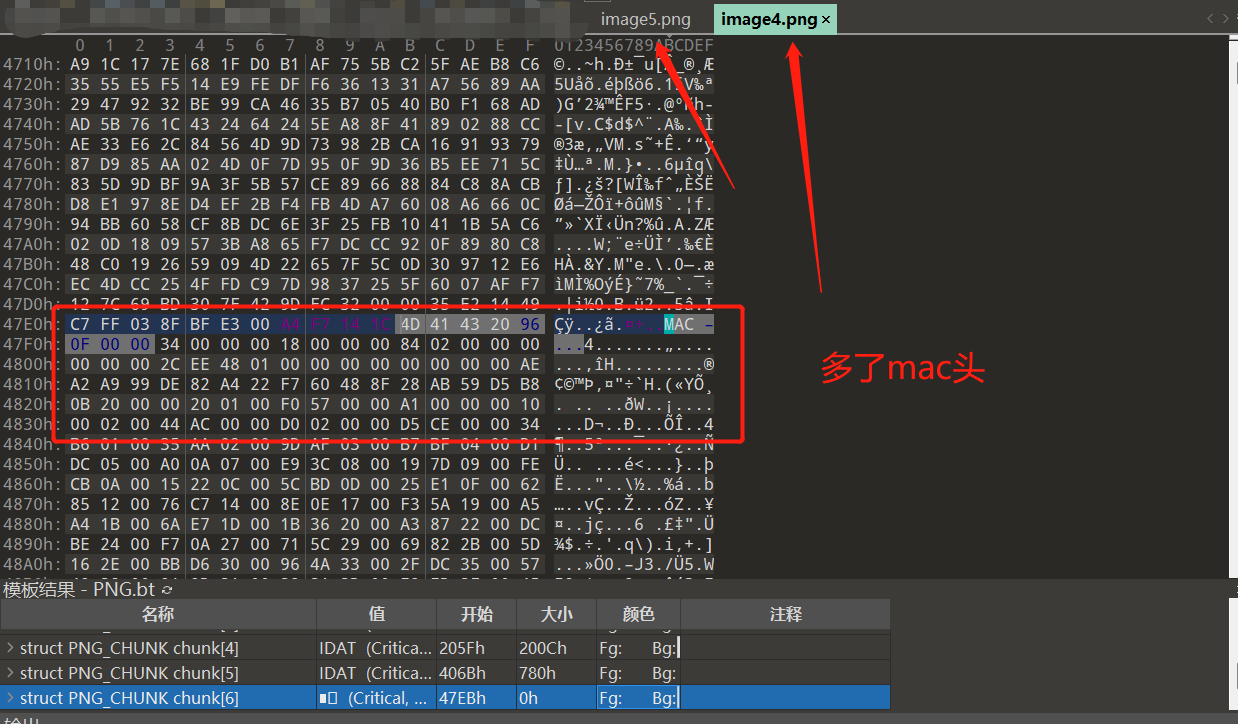
MAC 是ape文件的标识,其中ape格式也可以用deepsound加密
而deppsound解密需要密码
在\docProps中 thumbnail.jpg文件是个压缩包,
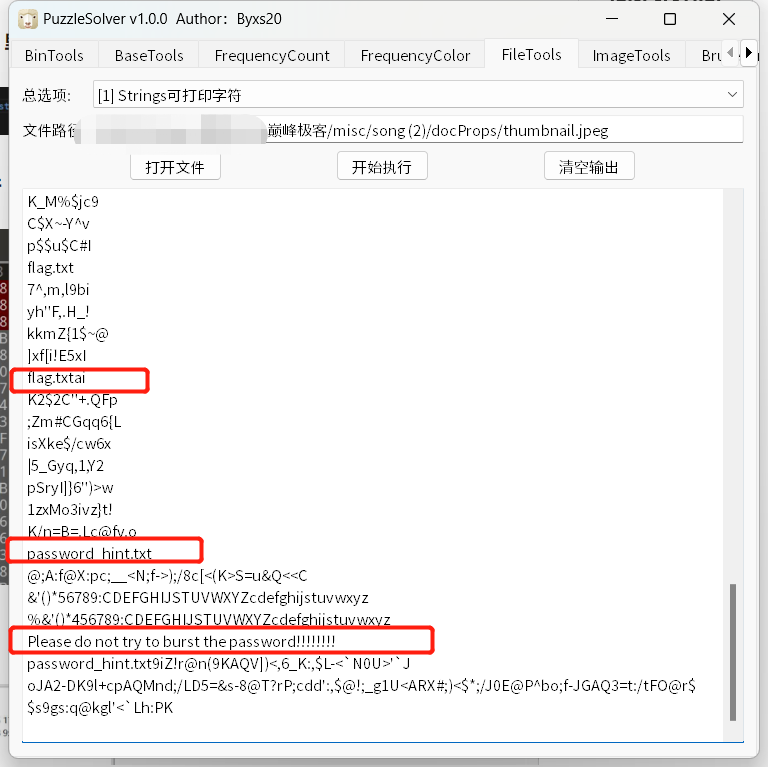
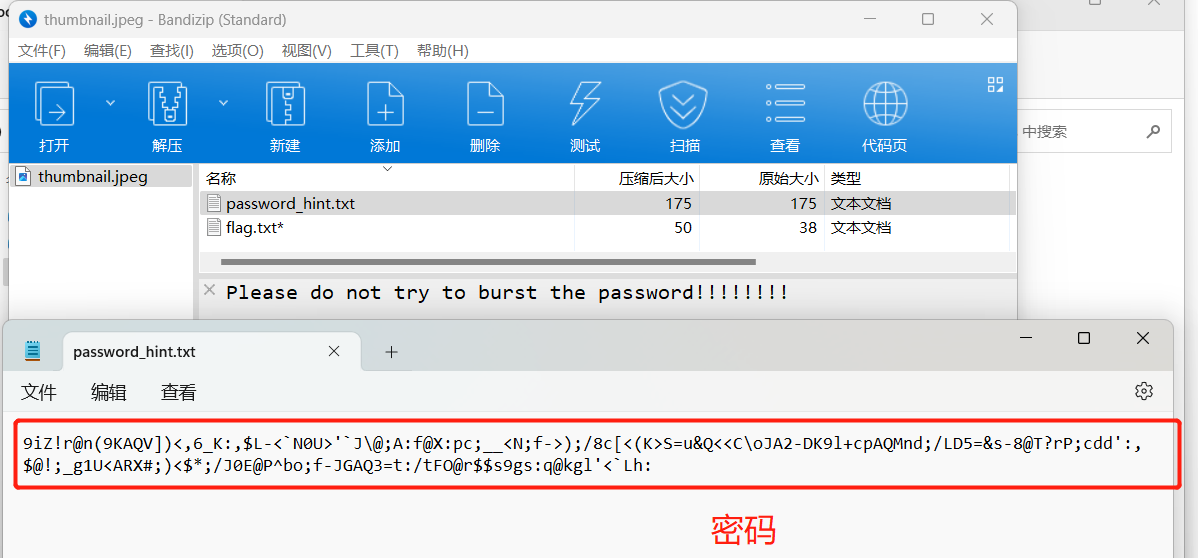
解码
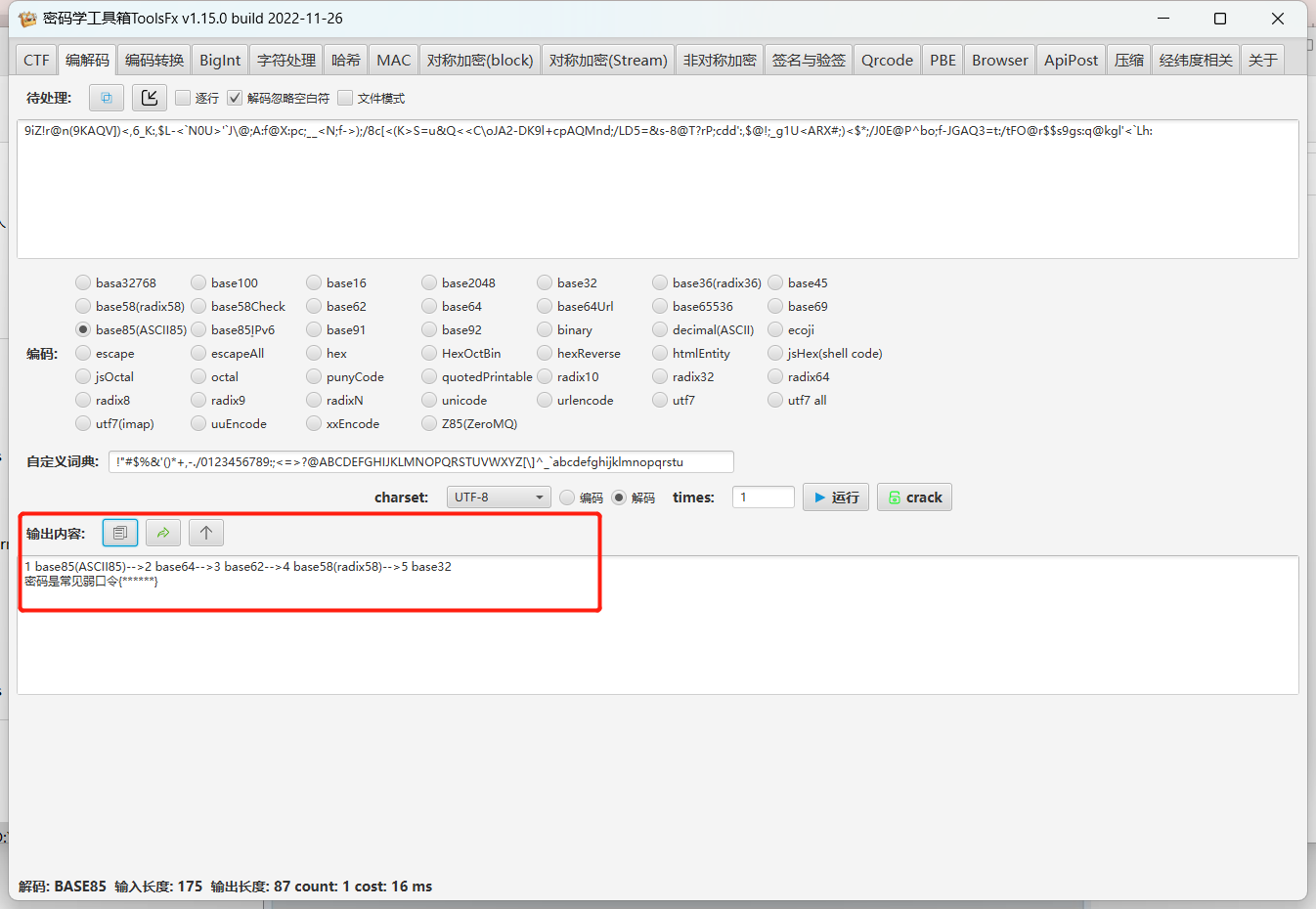
常见弱口令 – 123456
使用deepsound解密image4.ape(修改后缀
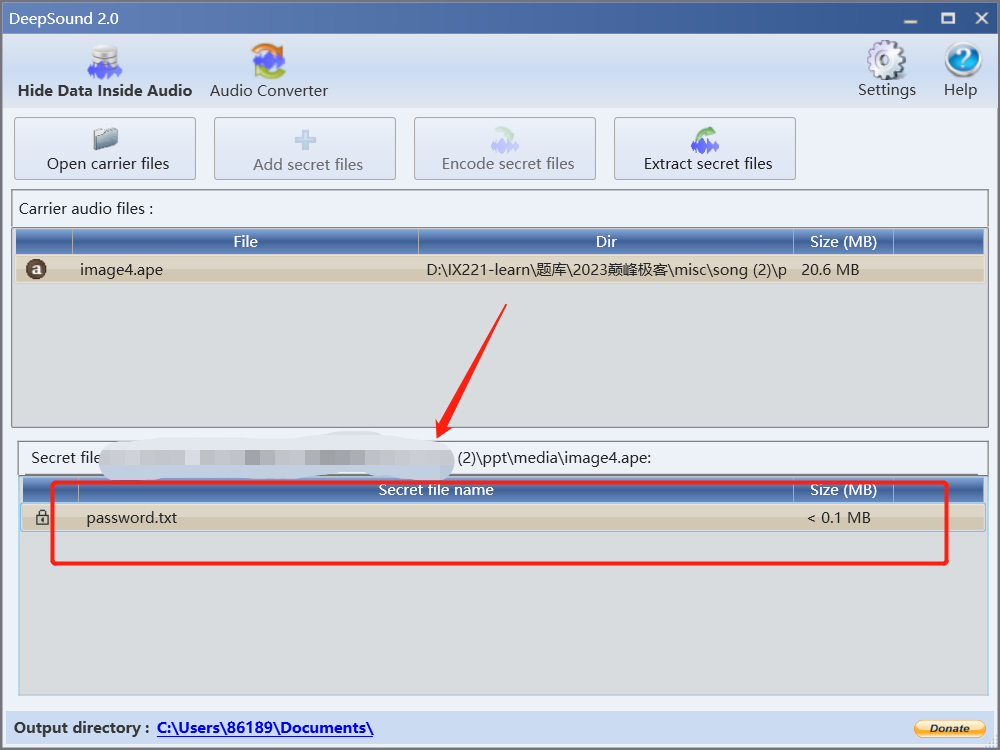
ook解码
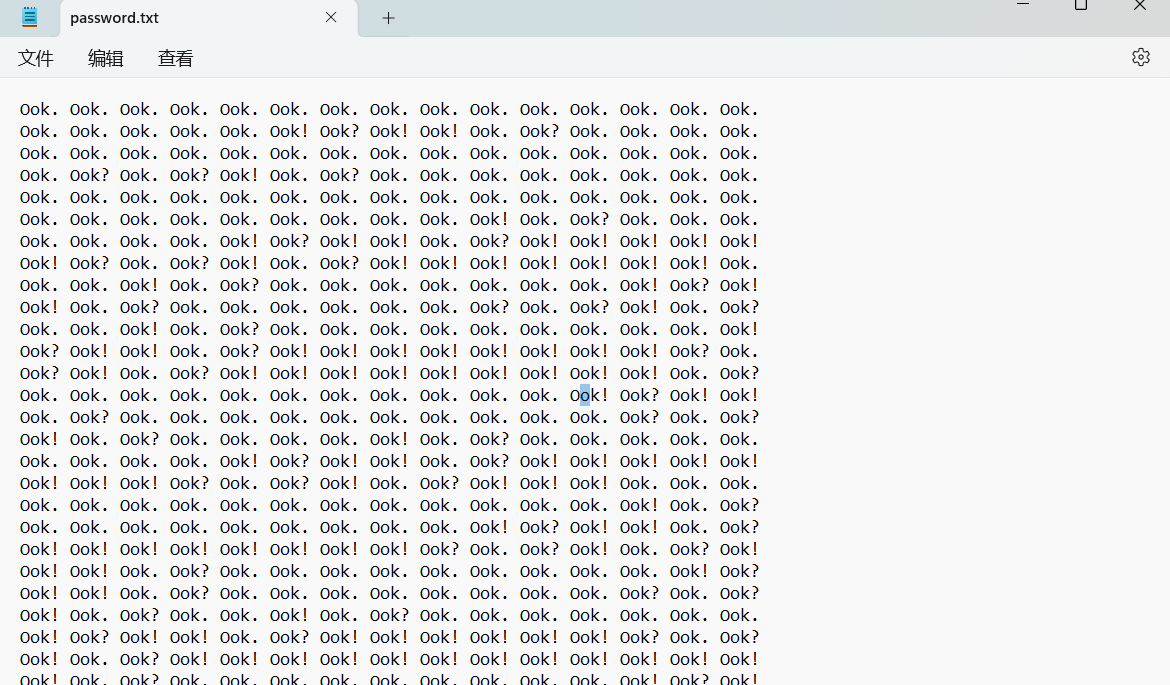
[Brainfuck/Ook! Obfuscation/Encoding splitbrain.org]
this_zip_password_is_QazWsx147!@#
打开flag.txt即可得解
flag{lW9tUyrh8RzzvysrswAwY7MHR4mmbLSt}
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 摘星阁!
