2023数字人才挑战赛-永信赛道WP
前言
本次比赛, 打的挺舒服的
作为一个逆向手, 数据分析感觉做的很顺, 很爽
确实学到了很多东西, 也意识到了很多的不足
然后的话, 因为和队友没有提前沟通好的原因, 丢了100分就特别难受
我靠 数据安全题(CTF题型)累死累活才做出来 分数时动态的
而数据分析 思维活跃 随便解 分数却是死的 好烦
(就是说 比赛时 内部一定要交流好哇~~)
**一起共勉 加油 ^_^ **
数据分析题解
区块链威胁分析.1
请提交App的Team Identifier。(答案严格区分大小写)
题目010打开 发现是PK
改.zip打开是个 DAFOM.app
(就是这个app的名字)
Google搜索相关team ID信息
这是一篇很好的博客,讲的很到位(https://blog.csdn.net/liuxiaoxiaobo/article/details/122047015)
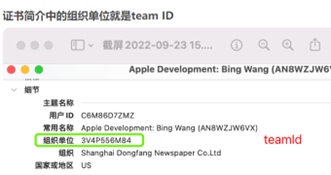
然后随便翻翻文件有个叫DAFOM的
在010 打开
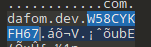
W58CYKFH67
这个 就是 flag
区块链威胁分析.2
这个app 就是一个黑客组织Lazarus 向区块链行业 弄得恶意应用程序
所以答案就是Lazarus
C2流量分析.1
追踪TCP流 在流16
发现了答案
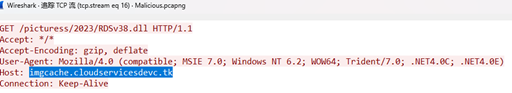
这个就是flag
http://imgcache.cloudservicesdevc.tk/picturess/2023/RDSv38.dll
C2流量分析.2
请提交Payload的SHA256哈希值。(字母大写,请根据流量内容作答)
找个在线网站
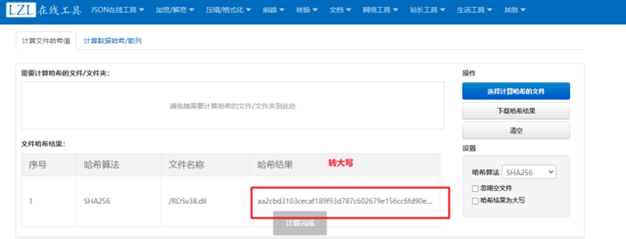
当然也可以用Linux命令(推荐)
flag AA2CBD3103CECAF189F93D787C602679E156CC6FD90E22646D637F01C64222CF
C2流量分析.3
Wireshark把文件导出来
根据题目描述 说有个有毒的程序
定位 最下面的DLL程序
确实也报毒了
用ida64打开
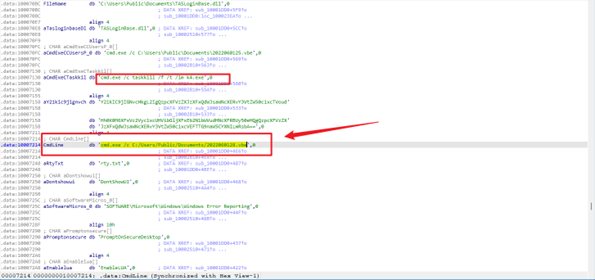
flag cmd.exe /c C:/Users/Public/Documents/2022060128.vbe
C2流量分析.4
请提交Payload中需要Base64解码的cmd命令的个数。(答案示例:1)

咱就是说, 我们这的师傅直接猜3拿了一血,牛
还有就是, 这数据分析题对逆向师傅来说也太友好了吧
fernet.3
针对 前两个我没写全(别的师傅解的), 我就只贴这个了
wireshark追踪流
7,8 ,9

Base64转图片
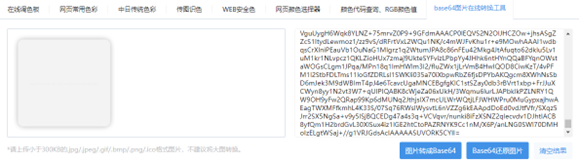
太抽象了 Stegsolve 转一下色道

flag{a20cb3c9-141c-41c4-8255-0cd3eb95b681}
贴一下我的脚本
1 | # 这是思路 |
就是这样, 明白了吧
1 | import base64 |
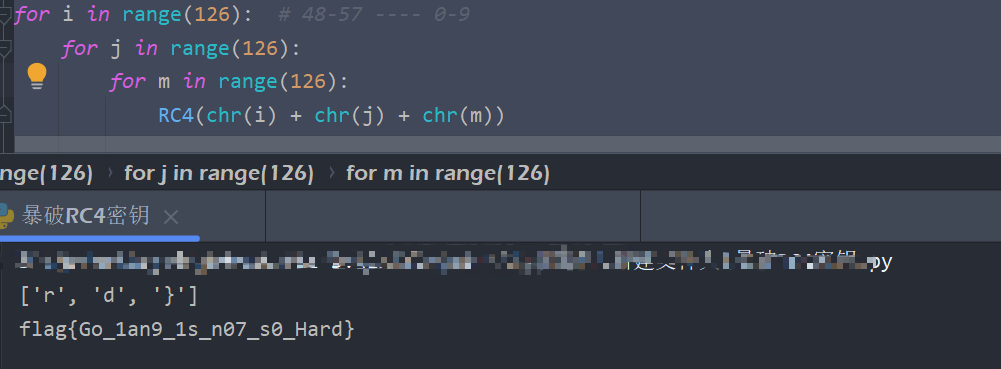
数据安全-逆向部分
有两个是逆向题
一个看着吓人, 其实就是个RC4算法,而且还没魔改(不对, RC4确实不好魔改, 但是呢,也没有结合别的算法)挺好解的, 就是有点唬人了
而另一个不出意外的话就出意外了(BUSHI) 爆零了
letsGO
用go语言写的
总体思路就是
- 发现是RC4加密
- 找到密文
- 找流密钥(没有就暴破)
- 解密
ida64分析
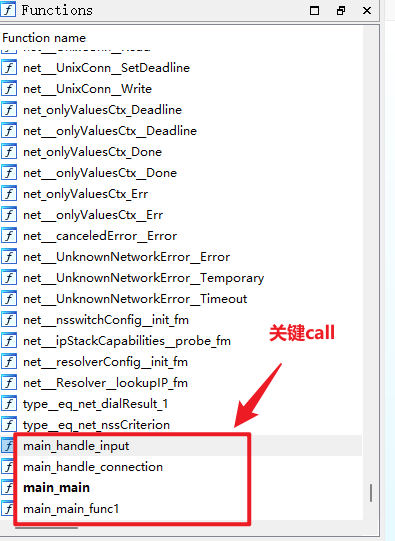
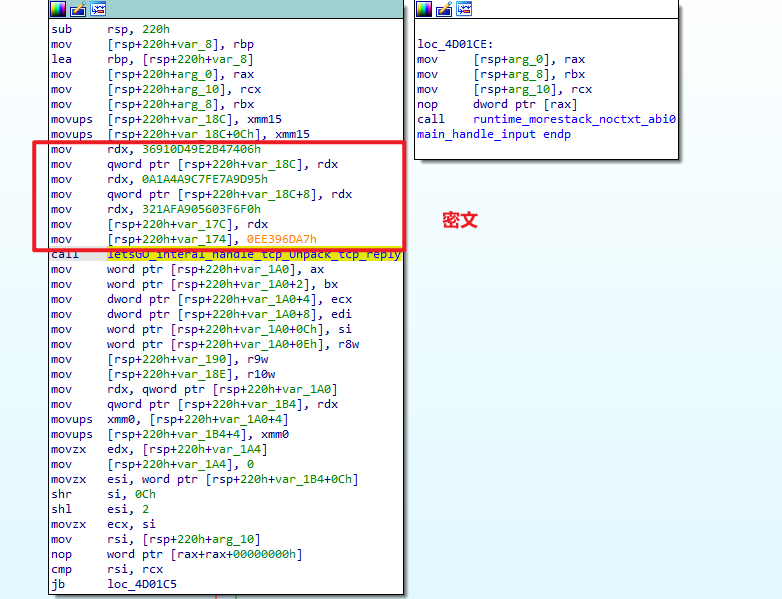
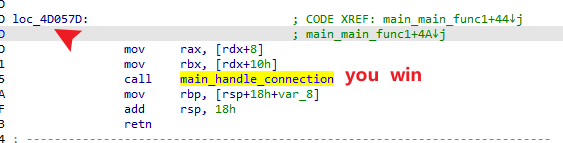
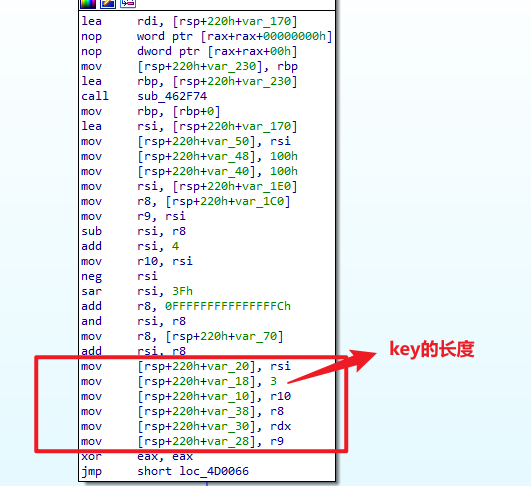
贴exp
1 | #include<stdio.h> |
1 | # # def RC4(keys): |
python 比较慢