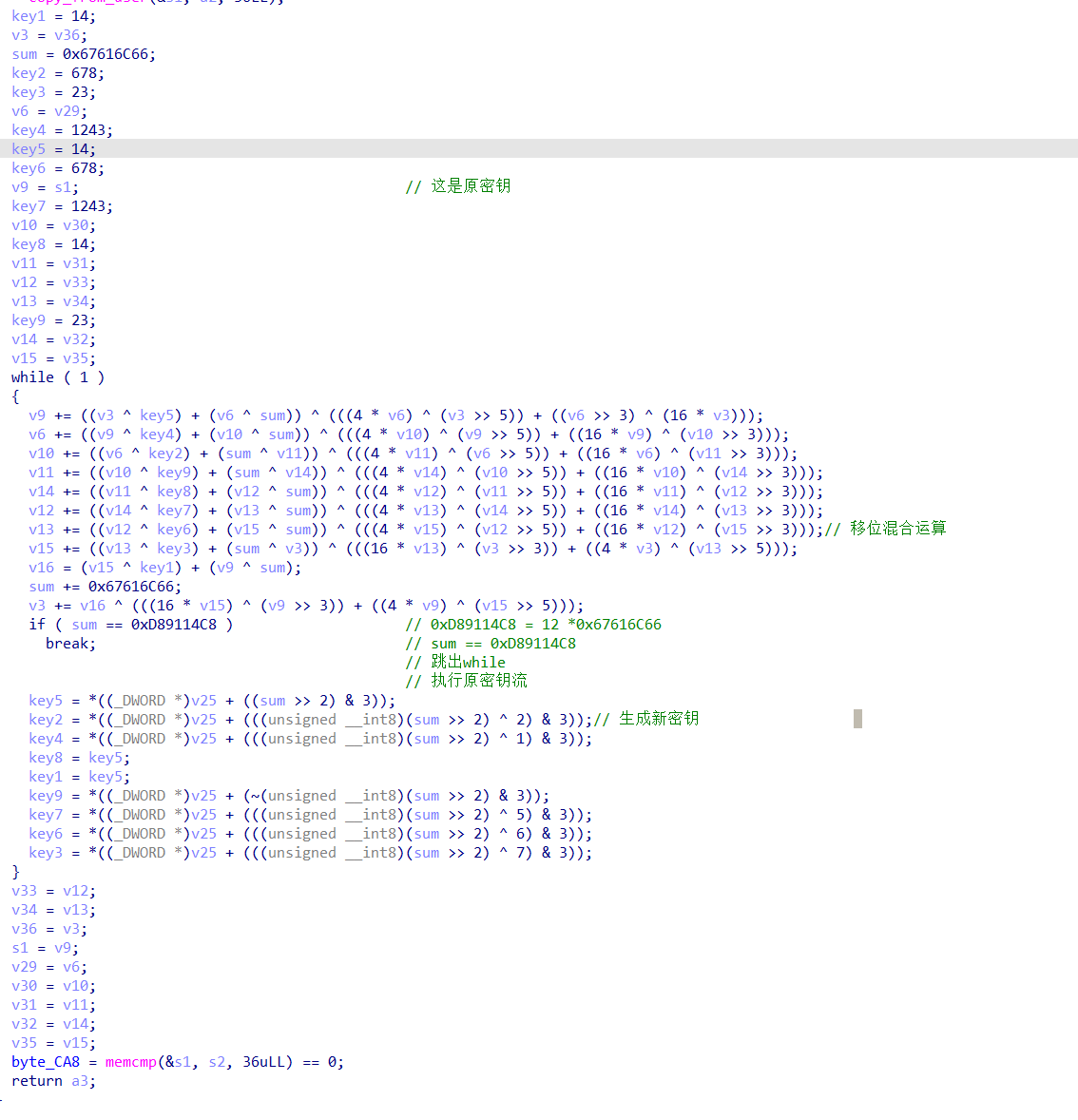
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
| #define _CRT_SECURE_NO_WARNINGS 1
#include <stdio.h>
#include <iostream>
#include <Windows.h>
using namespace std;
void encry()
{
unsigned int key4;
unsigned int sum;
int key2;
unsigned int v6;
int key3;
int key1;
unsigned int v9;
unsigned int v10;
unsigned int v11;
unsigned int v12;
unsigned int v13;
unsigned int v14;
unsigned int v15;
unsigned int v17;
int v16;
int key5;
int v19;
int key6;
int key7;
int key8;
int v23;
__int64 s2[4];
int v27;
unsigned int s1;
unsigned int v29;
unsigned int v30;
unsigned int v31;
unsigned int v32;
unsigned int v33;
unsigned int v34;
unsigned int v35;
unsigned int v36;
BYTE mycryp[] = { 0xaa, 0xb3, 0x83, 0xc8, 0x50, 0x39, 0xfb, 0x7, 0x59, 0x59, 0xbc, 0x75, 0x27, 0x7e, 0xb5, 0x7a, 0x0, 0x98, 0x24, 0xc0, 0x53, 0x57, 0xa3, 0xad, 0x3f, 0x49, 0x1d, 0xbf, 0x4, 0xaf, 0x14, 0x6e };
v27 = 1182995140;
s2[0] = 0x7FB3950C883B3AALL;
s2[1] = 0x7AB57E2775BC5959LL;
s2[2] = 0xADA35753C0249800LL;
s2[3] = 0x6E14AF04BF1D493FLL;
uint32_t key[] = { 0x4DB,0xE,0x17,0x2A6 };
s1 = {};
v9 = 0xC883B3AA;
v6 = 0x7FB3950;
v10 = 0x75BC5959;
v11 = 0x7AB57E27;
v14 = 0xC0249800;
v12 = 0xADA35753;
v13 = 0xBF1D493F;
v15 = 0x6E14AF04;
v17 = 0x468312C4;
sum = (0x67616C66 * 11);
int delta = 0x67616C66;
for (int tmp = 0; tmp < 11; tmp++)
{
if (sum != 0x67616C66)
{
key1 = *(key + ((sum >> 2) & 3));
key2 = *(key + (((sum >> 2) ^ 2) & 3));
key3 = *(key + (((sum >> 2) ^ 1) & 3));
v19 = key1;
v23 = key1;
key5 = *(key + (~(sum >> 2) & 3));
key6 = *(key + (((sum >> 2) ^ 5) & 3));
key7 = *(key + (((sum >> 2) ^ 6) & 3));
key8 = *(key + (((sum >> 2) ^ 7) & 3));
}
else
{
v23 = 14;
key2 = 678;
key8 = 23;
key3 = 1243;
key1 = 14;
key7 = 678;
v19 = 14;
key5 = 23;
key6 = 1243;
}
v17 -= (v15 ^ v23) + (v9 ^ sum) ^ (((16 * v15) ^ (v9 >> 3)) + ((4 * v9) ^ (v15 >> 5)));
v15 -= ((v13 ^ key8) + (sum ^ v17)) ^ (((16 * v13) ^ (v17 >> 3)) + ((4 * v17) ^ (v13 >> 5)));
v13 -= ((v12 ^ key7) + (v15 ^ sum)) ^ (((4 * v15) ^ (v12 >> 5)) + ((16 * v12) ^ (v15 >> 3)));
v12 -= ((v14 ^ key6) + (v13 ^ sum)) ^ (((4 * v13) ^ (v14 >> 5)) + ((16 * v14) ^ (v13 >> 3)));
v14 -= ((v11 ^ v19) + (v12 ^ sum)) ^ (((4 * v12) ^ (v11 >> 5)) + ((16 * v11) ^ (v12 >> 3)));
v11 -= ((v10 ^ key5) + (sum ^ v14)) ^ (((4 * v14) ^ (v10 >> 5)) + ((16 * v10) ^ (v14 >> 3)));
v10 -= ((v6 ^ key2) + (sum ^ v11)) ^ (((4 * v11) ^ (v6 >> 5)) + ((16 * v6) ^ (v11 >> 3)));
v6 -= ((v9 ^ key3) + (v10 ^ sum)) ^ (((4 * v10) ^ (v9 >> 5)) + ((16 * v9) ^ (v10 >> 3)));
v9 -= ((v17 ^ key1) + (v6 ^ sum)) ^ (((4 * v6) ^ (v17 >> 5)) + ((v6 >> 3) ^ (16 * v17)));
sum -= 0x67616C66;
}
printf("%c%c%c%c", *((char*)&v9 + 0), *((char*)&v9 + 1), *((char*)&v9 + 2), *((char*)&v9 + 3));
printf("%c%c%c%c", *((char*)&v6 + 0), *((char*)&v6 + 1), *((char*)&v6 + 2), *((char*)&v6 + 3));
printf("%c%c%c%c", *((char*)&v10 + 0), *((char*)&v10 + 1), *((char*)&v10 + 2), *((char*)&v10 + 3));
printf("%c%c%c%c", *((char*)&v11 + 0), *((char*)&v11 + 1), *((char*)&v11 + 2), *((char*)&v11 + 3));
printf("%c%c%c%c", *((char*)&v14 + 0), *((char*)&v14 + 1), *((char*)&v14 + 2), *((char*)&v14 + 3));
printf("%c%c%c%c", *((char*)&v12 + 0), *((char*)&v12 + 1), *((char*)&v12 + 2), *((char*)&v12 + 3));
printf("%c%c%c%c", *((char*)&v13 + 0), *((char*)&v13 + 1), *((char*)&v13 + 2), *((char*)&v13 + 3));
printf("%c%c%c%c", *((char*)&v15 + 0), *((char*)&v15 + 1), *((char*)&v15 + 2), *((char*)&v15 + 3));
printf("%c%c%c%c", *((char*)&v17 + 0), *((char*)&v17 + 1), *((char*)&v17 + 2), *((char*)&v17 + 3));
}
int main()
{
encry();
return 0;
}
|