reverse-反调试-异常处理|tea
简介
异常常用于动态反调试技术。正常运行的进程发生异常时,在**SEH(Structured Exception Handling)**机制的作用下,OS会接收异常,然后调用进程中注册的SEH处理。但是,若进程正被调试器调试,那么调试器就会先于SEH接收处理。利用该特征可判断进程是正常运行还是调试运行,然后根据不同的结果执行不同的操作,这就是利用异常处理机制不同的反调试原理。
上面回答 好官方 呃呃
下面我就一道题来讲解
NewStarCTF week4 - exception
一看题目 就是考察异常处理的
(题目算法就一个tea加密)
拖入ida静态分析
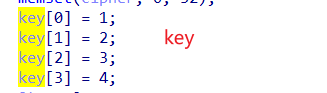
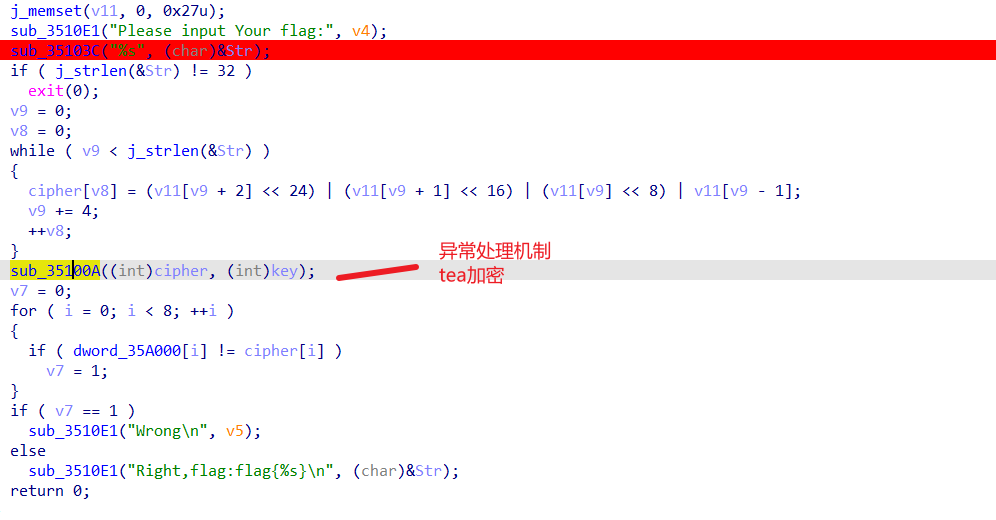
跟进35100A
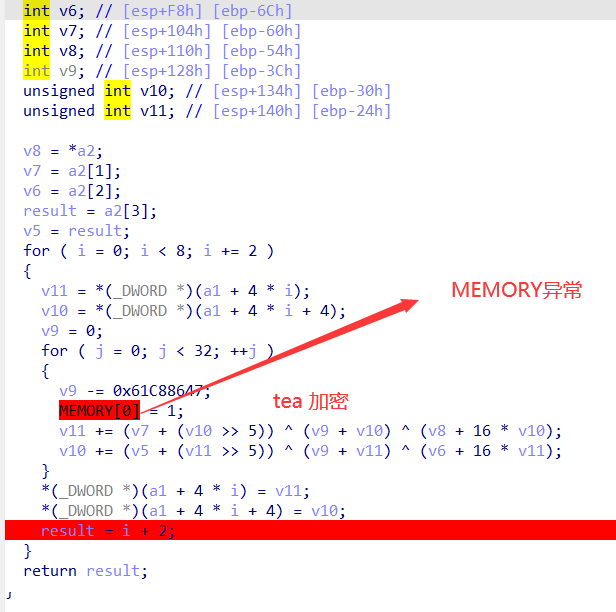
搜一下贴一下(看不懂 )
https://blog.csdn.net/u011279649/article/details/12840937
对于这道题 就是干扰我们得到delta
动调一下
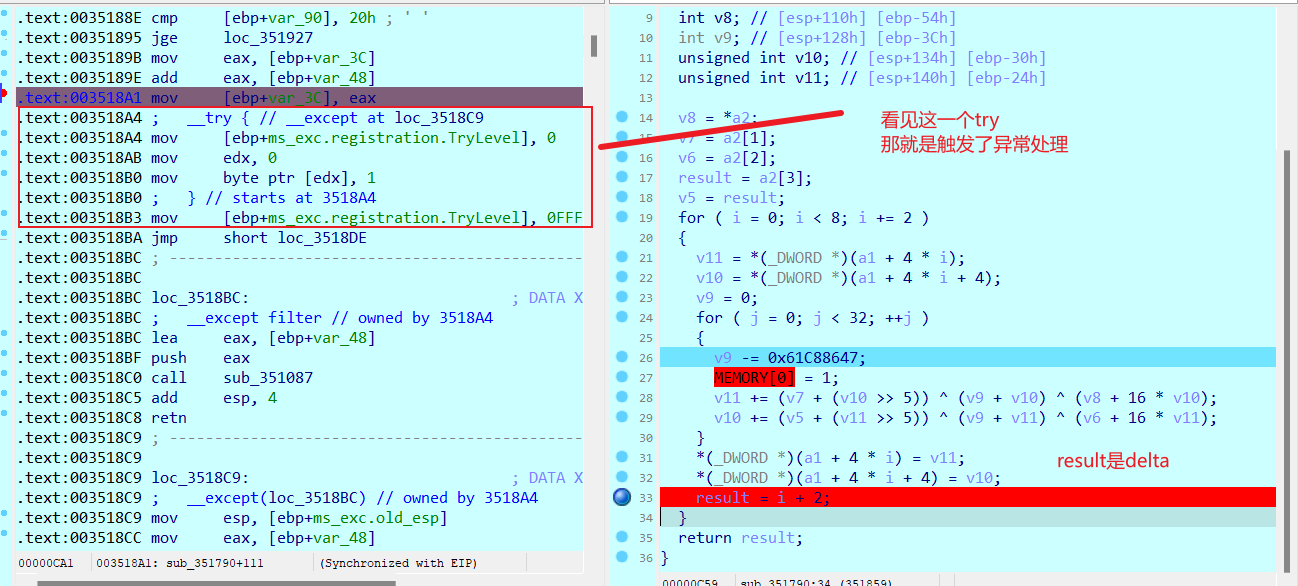
触发异常后, 将[ebp+var_48] ^ 0x1234578
(点击查看[ebp+var_48] 其实就是result(记着大小端序的问题))
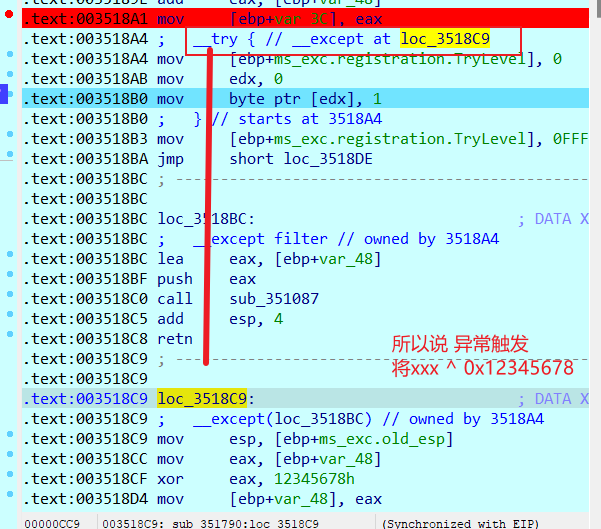
所以说可以写个脚本跑出值
贴exp
1 | sum = 0 |
1 | [0x9E3779B9, 0x2a3aa97a, 0xc8722333, 0x547552f4, 0xF2ACCCAD, 0x7EAFFC6E, 0x1CE77627 |
当然 你也可以通过动调获得delta的值 就是循环后result的值
就是运行查看result的值 一直循环32次(。。。。)
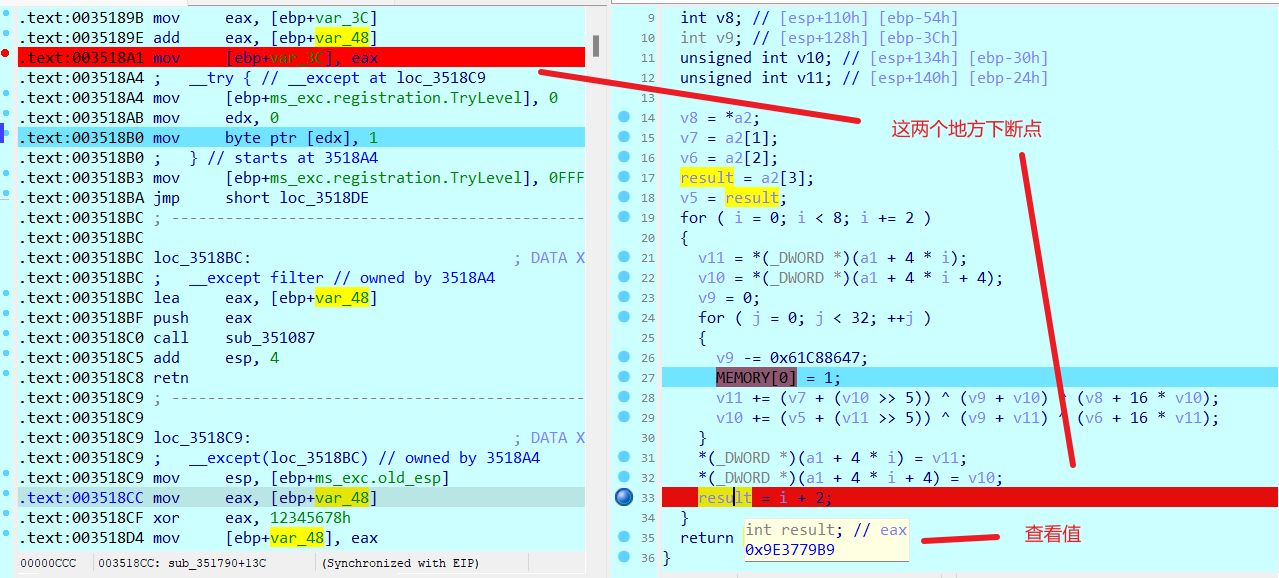
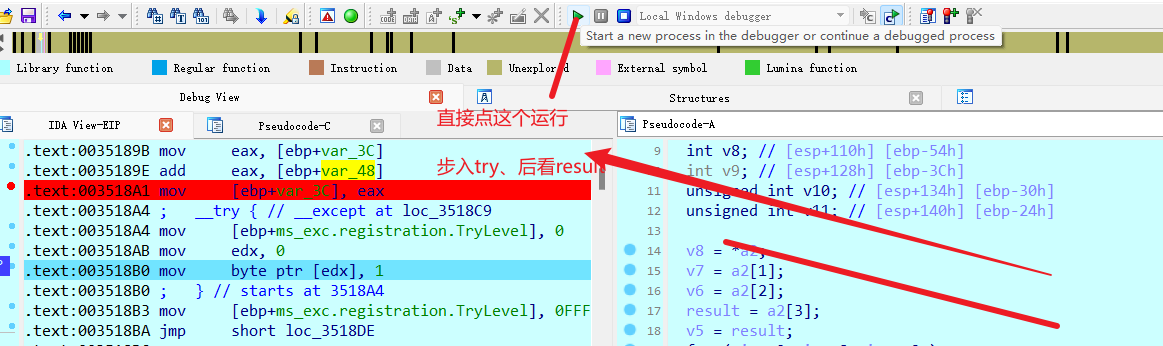
得到delta后即可以写exp了
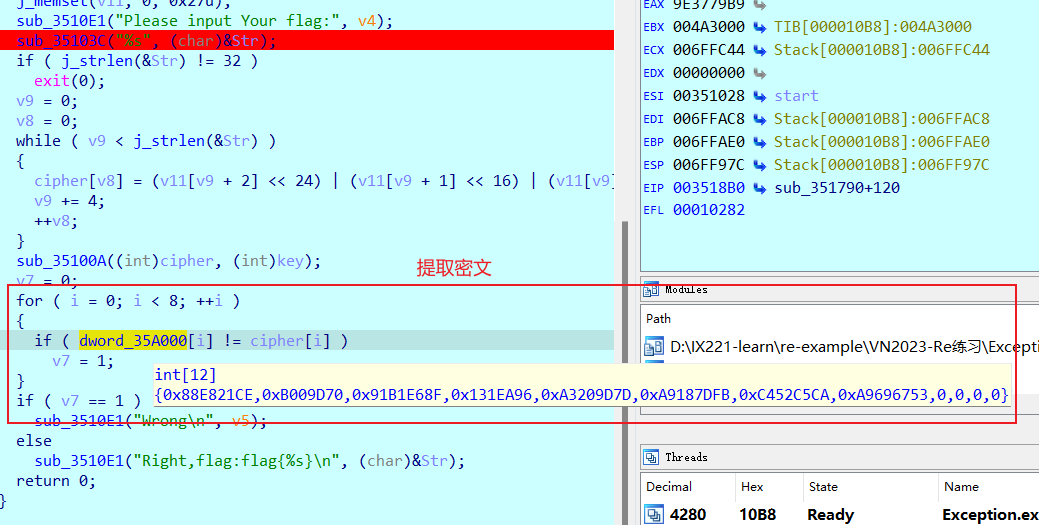
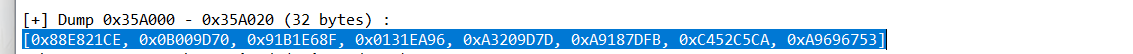
1 | [0x88E821CE, 0x0B009D70, 0x91B1E68F, 0x0131EA96, 0xA3209D7D, 0xA9187DFB, 0xC452C5CA, 0xA9696753] |
EXP
1 | encData = [0x88E821CE, 0x0B009D70, 0x91B1E68F, 0x131EA96, 0x0A3209D7D, 0x0A9187DFB, 0x0C452C5CA, 0x0A9696753] |
这是大端序 转成小端序
转字符就是flag了
flag{44C3A7F112DA2BE728F451C5E2D09558}
总结
简单的tea加密
加上一个异常处理
异常处理不是很麻烦
慢慢看 就好了
好的 本期结束
感谢观看
Orz Orz
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 摘星阁!
